Business
Column: Why hugely profitable corporations won't spend enough to keep hackers from stealing your private info

AT&T is one of America’s largest telecommunications companies. Last year it recorded a pretax profit of nearly $20 billion on $122.4 billion in revenue.
So why, you might ask, has AT&T been so pathetically sloppy about protecting its customers’ private information that the data of nearly all those customers — 110 million users — ended up in the hands of a “financially motivated” hacker group?
The breach was revealed on July 12, although it mostly occurred in 2022; AT&T attributed the reporting delay to requests from federal authorities to keep it under wraps while they investigated its national security significance.
Protecting your data is one of our top priorities.
— AT&T, after disclosing that personal data of as many as 110 million customers was stolen by hackers
This breach, cybersecurity experts say, is especially alarming because of the nature of the stolen data. It’s not merely financial data such as bank account or Social Security numbers that might enable hackers to raid a victim’s bank account or engage in identity theft to open new accounts.
In this case, it included information about what numbers were called by hacked users and the numbers that called them; the length of calls, and location data — where you might have been when making or receiving a call. The data the hackers snarfed up came from May through October 2022 and Jan. 2, 2023.
“Telecom providers hold some of the most sensitive information on consumers — a map of their daily lives — where they are, who they’re talking with, their social graph, everything,” says cybersecurity professional Brian Krebs.
The latest disclosure of a hack at AT&T might be considered a signpost for “the year of the megabreach.”
It follows AT&T’s announcement in April of an earlier, unrelated breach that may have compromised the Social Security numbers, PINs, email and mailing addresses, phone numbers, dates of birth and AT&T account numbers of 73 million current and former AT&T customers.
Both AT&T incidents pale in comparison with a massive data breach earlier this year at UnitedHealth Group, the nation’s biggest health insurance and health provider conglomerate. According to congressional testimony by UnitedHealth Chief Executive Andrew Witty and company news releases, a ransomware attack on the company’s Change Healthcare subsidiary has affected as many as 1 in 3 Americans.
Change Healthcare manages patient payments and reimbursements to medical providers. The ransomware hack crippled medical services nationwide and resulted in the exposure of patients’ treatment details and billing information, including credit card numbers. Patients reported that pharmacies were refusing to fill prescriptions because they couldn’t access insurance approvals, risking the patients’ health.
UnitedHealth said it paid a $22-million ransom in bitcoin, but couldn’t be sure that all the hacked information was returned. It also said that it advanced about $9 billion to providers to cover their expenses before their billing could be restored.
The company told Congress that it already had in place “a robust information security program with over 1,300 people and approximately $300 million in annual investment,” but of course those figures are meaningless — the question is how much it would cost to actually have a “robust” program in place, since $300 million obviously isn’t enough.
The breach occurred, according to testimony and statements by the company, because UnitedHealth tried to integrate Change Healthcare’s technology system with its own without first ensuring that Change’s system would require multifactor authentication, a basic security feature that requires users to enter an algorithmically generated code along with their password to gain access to a system or account.
The hackers breached “a legacy Change Healthcare server” that didn’t meet the parent company’s standards, the company said — but it used the noncompliant equipment anyway.
Data breaches affecting hundreds of thousands or millions of consumers have become such familiar features of the consumer landscape that the guilty companies respond with a standard playbook replete with promises to customers.
They point out all the data that wasn’t compromised — AT&T told customers that the latest debacle didn’t involve “the content of calls or texts, personal information such as Social Security numbers, dates of birth, or other personally identifiable information.” That’s a bit like airlines following up reports of deadly crashes by pointing out how many planes land and take off safely every day.
The companies typically offer aggrieved customers free credit monitoring and identity theft protection for a period of time; at UnitedHealth, that period is two years.
Whether those services are useful is open to question — after a 2017 data breach at the credit reporting firm Equifax exposed the personal data of 143 million Americans, the identity theft service LifeLock trumpeted its protective services (at $29.99 a month). What LifeLock didn’t make very clear was that the services it was selling were actually provided byEquifax.
The breached companies also attest to their determination to get to the bottom of the hacks, and to their commitment to customer security. AT&T’s recent breach disclosure included this pledge: “Protecting your data is one of our top priorities.”
If there were a trophy for flagrant lying in marketing materials, this would be a strong contender. Under the circumstances, it’s either blatantly untrue or reflects a critical flaw in the company’s fulfillment of its priorities. I asked AT&T what steps it has taken to discipline or remove any executives charged with fulfilling such a crucial priority, up to and including the CEO. AT&T didn’t respond directly to this or other questions I submitted, but referred me to its news release and a customer Q&A on the topic.
AT&T says the breach occurred in a company connection to a third-party cloud data service called Snowflake, to which it had entrusted its customer data. As it happens, some 165 of Snowflake’s corporate clients may also have been targeted by the hackers who struck AT&T. An ongoing investigation by cybersecurity experts suggests, however, that the fault isn’t Snowflake’s — it’s the fault of those clients, who didn’t observe best security practices.
That points to several issues that contributed to AT&T’s breach — and similar breaches around the corporate world. One is why AT&T is hoarding so much information about its users in the first place.
“To have years of call histories, text message histories and location data makes you a massive target for hackers,” says Albert Fox Cahn, executive director of the Surveillance Technology Oversight Project, a New York nonprofit.
“Why does AT&T keep so much information on so many users?” Cahn asks. “They have a perverse incentive to hold on to as much of our data as possible, to think about new ways to mine it for value. When they do that, we’re the ones put at risk.”
In any event, if AT&T is going to store data this sensitive, he says, it needs to employ more rigorous safeguards to protect it.
Yet in corporate America, cybersecurity has been an afterthought, if it receives any thought at all. “These companies at some point decide that it’s really expensive to care a lot more about security when there really aren’t a lot of consequences for screwing it up,” Krebs told me. “You might get sued or have to pay a few hundred million dollars in fines, but these are rounding errors on their profits.”
The European Union’s General Data Protection Regulation allows for a fine of up to 4% of a company’s annual revenue for an especially severe breach, but it’s unlikely that such a penalty could be legislated in the U.S. (If it were, AT&T might be liable for a bill of $4.9 billion.)
Krebs blames indifferent boards of directors for their inattention. Even a data-oriented company such as AT&T has no directors with specific expertise in cybersecurity. Of the nine directors in place as of the 2024 proxy statement, five are credited with experience in technology and innovation, according to what Villanova University business professor Noah Barsky correctly calls “perfunctory” language in their bios in the company’s 2024 proxy statement.
Only one, Stephen J. Luczo, is said to have any particular expertise in cybersecurity, but that’s only as a private equity investor — his background is in investment banking. The board’s newest member, Marissa Mayer, may have cybersecurity experience, but it’s not encouraging: During her tenure as CEO of Yahoo (2012 to 2017), that company experienced an epic data breach that compromised all 3 billion of its user accounts.
“It’s clear that industry is never going to do enough on its own” to protect customer data, Cahn says. The task may have to be placed in regulatory hands. Krebs suggests something akin to a cybersafety review board to introduce something close to accountability. Cahn suggests rules requiring the proactive deletion of sensitive information such as location data and medical records — “You can’t steal what doesn’t exist,” he told me.
The market may yet exercise its own discipline. UnitedHealth is learning the hard way that carelessness about cybersecurity can have a material effect on earnings. In its second-quarter earnings report released Tuesday, the company said that the full-year cost of the Change Healthcare hack may come to as much as $2.05 per share, an increase of as much as 45 cents from its original estimate. Its second-quarter earnings came to $4.54 per share.
But it’s customers who will really bear the costs. “Most Americans,” Krebs says, “have no choice but to do business with these companies if they want to participate in the modern society.”

Business
Video: The Web of Companies Owned by Elon Musk

new video loaded: The Web of Companies Owned by Elon Musk

By Kirsten Grind, Melanie Bencosme, James Surdam and Sean Havey
February 27, 2026
Business
Commentary: How Trump helped foreign markets outperform U.S. stocks during his first year in office
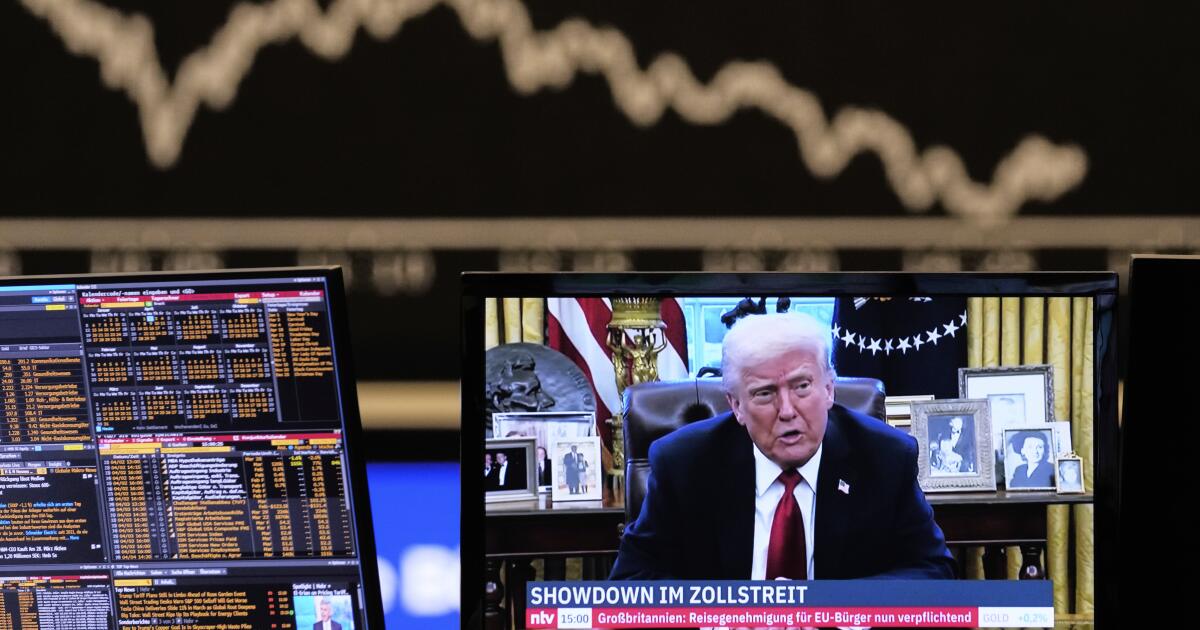
Trump has crowed about the gains in the U.S. stock market during his term, but in 2025 investors saw more opportunity in the rest of the world.
If you’re a stock market investor you might be feeling pretty good about how your portfolio of U.S. equities fared in the first year of President Trump’s term.
All the major market indices seemed to be firing on all cylinders, with the Standard & Poor’s 500 index gaining 17.9% through the full year.
But if you’re the type of investor who looks for things to regret, pay no attention to the rest of the world’s stock markets. That’s because overseas markets did better than the U.S. market in 2025 — a lot better. The MSCI World ex-USA index — that is, all the stock markets except the U.S. — gained more than 32% last year, nearly double the percentage gains of U.S. markets.
That’s a major departure from recent trends. Since 2013, the MSCI US index had bested the non-U.S. index every year except 2017 and 2022, sometimes by a wide margin — in 2024, for instance, the U.S. index gained 24.6%, while non-U.S. markets gained only 4.7%.
The Trump trade is dead. Long live the anti-Trump trade.
— Katie Martin, Financial Times
Broken down into individual country markets (also by MSCI indices), in 2025 the U.S. ranked 21st out of 23 developed markets, with only New Zealand and Denmark doing worse. Leading the pack were Austria and Spain, with 86% gains, but superior records were turned in by Finland, Ireland and Hong Kong, with gains of 50% or more; and the Netherlands, Norway, Britain and Japan, with gains of 40% or more.
Investment analysts cite several factors to explain this trend. Judging by traditional metrics such as price/earnings multiples, the U.S. markets have been much more expensive than those in the rest of the world. Indeed, they’re historically expensive. The Standard & Poor’s 500 index traded in 2025 at about 23 times expected corporate earnings; the historical average is 18 times earnings.
Investment managers also have become nervous about the concentration of market gains within the U.S. technology sector, especially in companies associated with artificial intelligence R&D. Fears that AI is an investment bubble that could take down the S&P’s highest fliers have investors looking elsewhere for returns.
But one factor recurs in almost all the market analyses tracking relative performance by U.S. and non-U.S. markets: Donald Trump.
Investors started 2025 with optimism about Trump’s influence on trading opportunities, given his apparent commitment to deregulation and his braggadocio about America’s dominant position in the world and his determination to preserve, even increase it.
That hasn’t been the case for months.
”The Trump trade is dead. Long live the anti-Trump trade,” Katie Martin of the Financial Times wrote this week. “Wherever you look in financial markets, you see signs that global investors are going out of their way to avoid Donald Trump’s America.”
Two Trump policy initiatives are commonly cited by wary investment experts. One, of course, is Trump’s on-and-off tariffs, which have left investors with little ability to assess international trade flows. The Supreme Court’s invalidation of most Trump tariffs and the bellicosity of his response, which included the immediate imposition of new 10% tariffs across the board and the threat to increase them to 15%, have done nothing to settle investors’ nerves.
Then there’s Trump’s driving down the value of the dollar through his agitation for lower interest rates, among other policies. For overseas investors, a weaker dollar makes U.S. assets more expensive relative to the outside world.
It would be one thing if trade flows and the dollar’s value reflected economic conditions that investors could themselves parse in creating a picture of investment opportunities. That’s not the case just now. “The current uncertainty is entirely man-made (largely by one orange-hued man in particular) but could well continue at least until the US mid-term elections in November,” Sam Burns of Mill Street Research wrote on Dec. 29.
Trump hasn’t been shy about trumpeting U.S. stock market gains as emblems of his policy wisdom. “The stock market has set 53 all-time record highs since the election,” he said in his State of the Union address Tuesday. “Think of that, one year, boosting pensions, 401(k)s and retirement accounts for the millions and the millions of Americans.”
Trump asserted: “Since I took office, the typical 401(k) balance is up by at least $30,000. That’s a lot of money. … Because the stock market has done so well, setting all those records, your 401(k)s are way up.”
Trump’s figure doesn’t conform to findings by retirement professionals such as the 401(k) overseers at Bank of America. They reported that the average account balance grew by only about $13,000 in 2025. I asked the White House for the source of Trump’s claim, but haven’t heard back.
Interpreting stock market returns as snapshots of the economy is a mug’s game. Despite that, at her recent appearance before a House committee, Atty. Gen. Pam Bondi tried to deflect questions about her handling of the Jeffrey Epstein records by crowing about it.
“The Dow is over 50,000 right now, she declared. “Americans’ 401(k)s and retirement savings are booming. That’s what we should be talking about.”
I predicted that the administration would use the Dow industrial average’s break above 50,000 to assert that “the overall economy is firing on all cylinders, thanks to his policies.” The Dow reached that mark on Feb. 6. But Feb. 11, the day of Bondi’s testimony, was the last day the index closed above 50,000. On Thursday, it closed at 49,499.50, or about 1.4% below its Feb. 10 peak close of 50,188.14.
To use a metric suggested by economist Justin Wolfers of the University of Michigan, if you invested $48,488 in the Dow on the day Trump took office last year, when the Dow closed at 48,448 points, you would have had $50,000 on Feb. 6. That’s a gain of about 3.2%. But if you had invested the same amount in the global stock market not including the U.S. (based on the MSCI World ex-USA index), on that same day you would have had nearly $60,000. That’s a gain of nearly 24%.
Broader market indices tell essentially the same story. From Jan. 17, 2025, the last day before Trump’s inauguration, through Thursday’s close, the MSCI US stock index gained a cumulative 16.3%. But the world index minus the U.S. gained nearly 42%.
The gulf between U.S. and non-U.S. performance has continued into the current year. The S&P 500 has gained about 0.74% this year through Wednesday, while the MSCI World ex-USA index has gained about 8.9%. That’s “the best start for a calendar year for global stocks relative to the S&P 500 going back to at least 1996,” Morningstar reports.
It wouldn’t be unusual for the discrepancy between the U.S. and global markets to shrink or even reverse itself over the course of this year.
That’s what happened in 2017, when overseas markets as tracked by MSCI beat the U.S. by more than three percentage points, and 2022, when global markets lost money but U.S. markets underperformed the rest of the world by more than five percentage points.
Economic conditions change, and often the stock markets march to their own drummers. The one thing less likely to change is that Trump is set to remain president until Jan. 20, 2029. Make your investment bets accordingly.
Business
How the S&P 500 Stock Index Became So Skewed to Tech and A.I.

Nvidia, the chipmaker that became the world’s most valuable public company two years ago, was alone worth more than $4.75 trillion as of Thursday morning. Its value, or market capitalization, is more than double the combined worth of all the companies in the energy sector, including oil giants like Exxon Mobil and Chevron.
The chipmaker’s market cap has swelled so much recently, it is now 20 percent greater than the sum of all of the companies in the materials, utilities and real estate sectors combined.
What unifies these giant tech companies is artificial intelligence. Nvidia makes the hardware that powers it; Microsoft, Apple and others have been making big bets on products that people can use in their everyday lives.
But as worries grow over lavish spending on A.I., as well as the technology’s potential to disrupt large swaths of the economy, the outsize influence that these companies exert over markets has raised alarms. They can mask underlying risks in other parts of the index. And if a handful of these giants falter, it could mean widespread damage to investors’ portfolios and retirement funds in ways that could ripple more broadly across the economy.
The dynamic has drawn comparisons to past crises, notably the dot-com bubble. Tech companies also made up a large share of the stock index then — though not as much as today, and many were not nearly as profitable, if they made money at all.
How the current moment compares with past pre-crisis moments
To understand how abnormal and worrisome this moment might be, The New York Times analyzed data from S&P Dow Jones Indices that compiled the market values of the companies in the S&P 500 in December 1999 and August 2007. Each date was chosen roughly three months before a downturn to capture the weighted breakdown of the index before crises fully took hold and values fell.
The companies that make up the index have periodically cycled in and out, and the sectors were reclassified over the last two decades. But even after factoring in those changes, the picture that emerges is a market that is becoming increasingly one-sided.
In December 1999, the tech sector made up 26 percent of the total.
In August 2007, just before the Great Recession, it was only 14 percent.
Today, tech is worth a third of the market, as other vital sectors, such as energy and those that include manufacturing, have shrunk.
Since then, the huge growth of the internet, social media and other technologies propelled the economy.
Now, never has so much of the market been concentrated in so few companies. The top 10 make up almost 40 percent of the S&P 500.
How much of the S&P 500 is occupied by the top 10 companies
With greater concentration of wealth comes greater risk. When so much money has accumulated in just a handful of companies, stock trading can be more volatile and susceptible to large swings. One day after Nvidia posted a huge profit for its most recent quarter, its stock price paradoxically fell by 5.5 percent. So far in 2026, more than a fifth of the stocks in the S&P 500 have moved by 20 percent or more. Companies and industries that are seen as particularly prone to disruption by A.I. have been hard hit.
The volatility can be compounded as everyone reorients their businesses around A.I, or in response to it.
The artificial intelligence boom has touched every corner of the economy. As data centers proliferate to support massive computation, the utilities sector has seen huge growth, fueled by the energy demands of the grid. In 2025, companies like NextEra and Exelon saw their valuations surge.
The industrials sector, too, has undergone a notable shift. General Electric was its undisputed heavyweight in 1999 and 2007, but the recent explosion in data center construction has evened out growth in the sector. GE still leads today, but Caterpillar is a very close second. Caterpillar, which is often associated with construction, has seen a spike in sales of its turbines and power-generation equipment, which are used in data centers.
One large difference between the big tech companies now and their counterparts during the dot-com boom is that many now earn money. A lot of the well-known names in the late 1990s, including Pets.com, had soaring valuations and little revenue, which meant that when the bubble popped, many companies quickly collapsed.
Nvidia, Apple, Alphabet and others generate hundreds of billions of dollars in revenue each year.
And many of the biggest players in artificial intelligence these days are private companies. OpenAI, Anthropic and SpaceX are expected to go public later this year, which could further tilt the market dynamic toward tech and A.I.
Methodology
Sector values reflect the GICS code classification system of companies in the S&P 500. As changes to the GICS system took place from 1999 to now, The New York Times reclassified all companies in the index in 1999 and 2007 with current sector values. All monetary figures from 1999 and 2007 have been adjusted for inflation.
-

 World2 days ago
World2 days agoExclusive: DeepSeek withholds latest AI model from US chipmakers including Nvidia, sources say
-

 Massachusetts2 days ago
Massachusetts2 days agoMother and daughter injured in Taunton house explosion
-

 Montana1 week ago
Montana1 week ago2026 MHSA Montana Wrestling State Championship Brackets And Results – FloWrestling
-

 Oklahoma1 week ago
Oklahoma1 week agoWildfires rage in Oklahoma as thousands urged to evacuate a small city
-

 Louisiana5 days ago
Louisiana5 days agoWildfire near Gum Swamp Road in Livingston Parish now under control; more than 200 acres burned
-

 Technology6 days ago
Technology6 days agoYouTube TV billing scam emails are hitting inboxes
-

 Denver, CO2 days ago
Denver, CO2 days ago10 acres charred, 5 injured in Thornton grass fire, evacuation orders lifted
-

 Technology6 days ago
Technology6 days agoStellantis is in a crisis of its own making




















