Technology
6 things to do right now to boost your security, privacy before it’s too late

There are so many things you can do to protect yourself and your loved ones by stepping up your privacy and security. All the things you can do, however, can be overwhelming. Below are six simple steps you can take right now that will help make your life safer and more secure immediately.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER
Security icon on the computer (Kurt “CyberGuy” Knutsson)
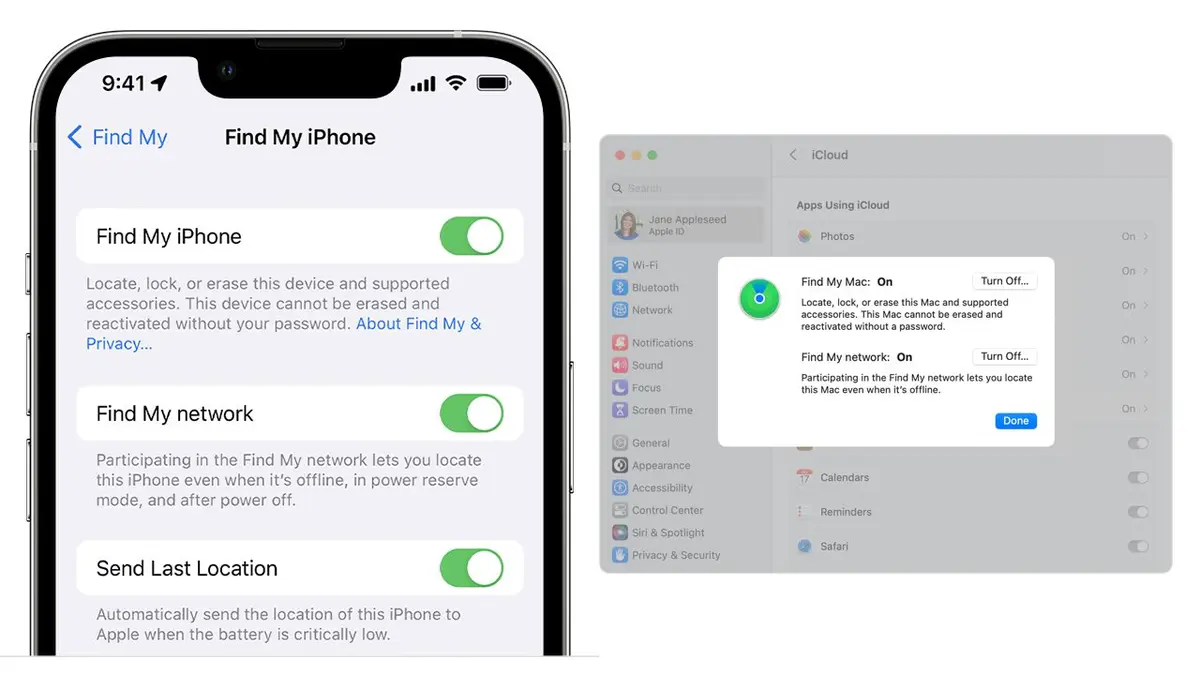
1. Turn on ‘Find My’ on your iPhone
While it seems like a basic step, “Find My” is not on by default on your iPhone. If you own an Apple device or are fully immersed in the Apple ecosystem, it is worth it to make sure to turn on Find My.
If you lose or have your Apple device stolen, and it is linked to Find My and turned on, you can use the app or sign into your iCloud account to track your device. For the Find My app to be effective, the device that is lost or stolen needs to be powered on and usually connected to the internet or data network.
Apple offers another feature known as Find My Network. This allows for tracking Apple devices even when they are not connected to the internet. However, it’s important to note that for this feature to be effective, Find My must be enabled on the device before it is lost or stolen.
Now, let’s discuss the steps to follow for Android. Install the Find My Device app to be prepared to use one Android phone or tablet to find another. Click here to learn how to find, lock or erase your Android device.
Find My iPhone feature (Kurt “CyberGuy” Knutsson)
MORE: 8 WAYS TO LOCK UP YOUR IPHONE’S PRIVATE STUFF
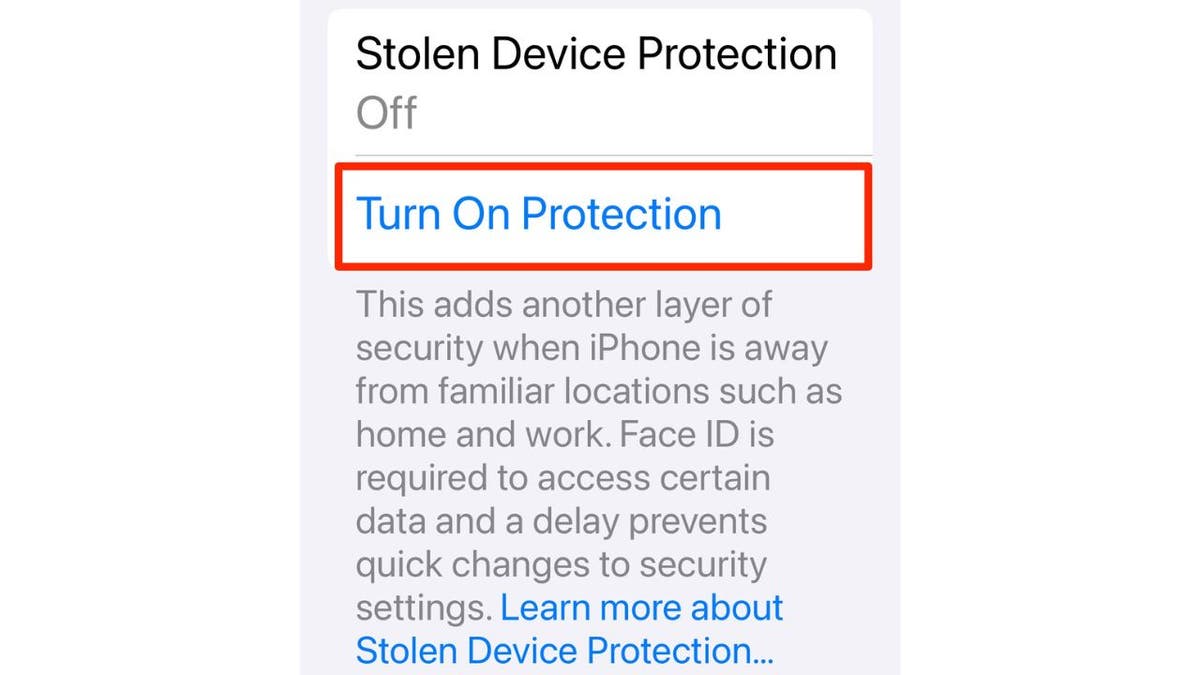
2. Activate ‘Stolen Device Protection’
iPhones are not only expensive, but they usually contain important personal and professional information. This makes having your iPhone stolen a complete nightmare. Turning on this “Stolen Device Protection” feature on your iPhone can give you an extra layer of protection. This feature gives you an additional layer of protection when your iPhone leaves a familiar location, such as work or home.
If you have this feature on, and your device is away from your familiar locations, it will require Face ID or Touch ID for biometric authentication to access certain features of your iPhone, such as accessing passwords or credit card information.
Additionally, a security delay is activated, so outside your familiar locations, there is an hour delay to take security actions such as changing your Apple ID password and then a Face ID or Touch ID authentication.
Stolen Device Protection on iPhone (Kurt “CyberGuy” Knutsson)
3. Secure your social media accounts before they get hijacked
While it can be easy to dismiss social media accounts as a nonessential aspect of your digital security or privacy, it can be the gateway for danger if you aren’t proactive. Once your social media accounts are hacked, not only can hackers and scammers target your information to wreak havoc in other aspects of your life, but they can use it to target your social or professional networks.
If inappropriate materials are posted on your social media accounts, it can damage not only your social reputation but also your professional one. To avoid this, take several steps right away, including changing your passwords or turning on two-factor authentication. Also, consider using a password manager to generate and store complex passwords.
In addition, here’s how to change your privacy settings on Facebook, Instagram and X.

A person reaching to pull out their wallet (Kurt “CyberGuy” Knutsson)
MORE: HOW IMPOSTERS ARE TRYING TO EXPLOIT YOUR GRIEF AND WALLET IN A NEW FUNERAL SCAM
4. Empty your wallet of these items
Sometimes it isn’t your devices that can put you at risk from scammers and criminals. It might be as simple as what you carry in your wallet. Because you’re usually carrying your wallet when you’re operating in the world, it has the potential to leave you more vulnerable than certain devices, such as your desktop.
Carrying items such as all your credit and debit cards in your wallet puts all your accounts at risk as opposed to only carrying the cards you most commonly use. If your wallet gets stolen, you still have alternative cards to use while you freeze or replace your cards. For other items to remove from your wallet immediately, read “Why you should never carry these things in your wallet.”
5. Back up your devices
Because hackers have become more sophisticated and resilient, it has caused consumers to return equal force with more sophisticated efforts to maintain their security and privacy. An old-school step, however, that gets lost in the shuffle of this effort is backing up your devices. Data, whether it be photos or contacts, is sometimes irreplaceable. Though devices can be expensive to replace, data, if lost, can be incredibly hard to recover.
Regularly backing up your devices can give you an advantage over any breaches in security. If you have the option to remotely delete information on your device if it gets stolen, you can do so with definitive ease. If your device crashes or breaks, you don’t have to spend costly amounts of money to try to recover data.

A woman typing on laptop (Kurt “CyberGuy” Knutsson)
MORE: WINDOWS DEFENDER VS ANTIVIRUS SOFTWARE: FREE PROTECTION FALLS SHORT
6. Have good antivirus software on all your devices
Viruses or malware can not only make your device a nightmare to use, they can also make it your worst enemy by being a wealth of personal and professional information that can be used against you. If the problem is bad enough, you may be required to reset your device to its factory setting, which means you can lose all your data.
The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams.
By simply installing and turning on an antivirus service, you can catch viruses and malware before they completely infect and infiltrate your device. See expert reviews of the best antivirus protection for your Windows, Mac, Android and iOS devices.
Kurt’s key takeaways
In a more complicated world with a variety of devices that can leave you more vulnerable to criminals, it may seem easier to bury your head in the sand. If you take or have taken any of the simple steps above, you have already made your life safer.
Have you ever lost or had your device stolen? Have you ever lost your wallet and experienced identity theft or fraud as a result? What behavioral or physical changes have you had to make to adjust to the changing landscape of modern life? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.

Technology
Amazon says its Prime deliveries are getting even faster
/cdn.vox-cdn.com/uploads/chorus_asset/file/23935559/acastro_STK103__02.jpg)
To me, Prime’s promise of two-day shipping is more of an added bonus to Prime Video and stuff like Fallout. But it’s become an expectation, leading other retailers like Walmart and Target to roll out faster shipping options of their own.
Now, Amazon says its deliveries are getting even faster, announcing that it delivered over 2 billion items the same or next day to Prime members during the first three months of 2024, breaking its record for 2023. The company says it delivered almost 60 percent of Prime orders the same or next day in 60 of the biggest metropolitan areas in the US.
If you buy from Amazon, have you noticed any differences lately? Same-day and next-day options seem to be more widely available, but it’s hard to tell how that applies to different items in different places or whether the associated costs are worth it based on reports of warehouse injuries and workers organizing for better conditions.
The control Amazon has over shipping and fulfillment has helped make it the target of a lawsuit from the Federal Trade Commission. The agency alleges Amazon engages in anticompetitive behavior by unfairly limiting which sellers are eligible for Prime shipping and coercing companies into using its fulfillment services. Amazon claims that the FTC’s efforts could result in “slower or less reliable” Prime shipping for customers.
In 2019, Amazon said it was spending billions to build up an in-house fulfillment operation covering planes, trucks, drones, and robots to rival FedEx and UPS and enable these one-day-or-less deliveries. And last year, it introduced a program that allows sellers to ship their products directly from factories — regardless of whether they’re going to one of Amazon’s many warehouses.
Technology
How ‘Yahoo Boys’ use real-time face-swapping to carry out elaborate romance scams

We’ve all heard of catfish scams – when someone pretends to be a lover on the other side of the screen, but instead, they aren’t who they say they are once their real face is revealed. Now, there’s a similar scam on the rise, and it’s much more sophisticated because scammers can fake the face, too. The scam is known as the “Yahoo Boys” scam, and it’s taking “catfishing” to a whole new level.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER
Woman on laptop making a heart sign (Kurt “CyberGuy” Knutsson)
How does deepfake technology work?
Deepfake technology uses AI to allow people to impersonate others over audio or video. The technology is essentially able to replicate someone’s face, facial expressions, gestures, voice, etc., so that the scammer can pretend to be someone they aren’t with almost perfect accuracy. Although deepfake technology has some intentions for good – like in the film industry or advertising (though there are some debates regarding the ethics of this) – it’s generally used for more malicious purposes than anything else.
Because it’s very difficult to tell whether or not a deepfake is the real person or a deepfake (and also because deepfakes are relatively new), deepfakes can have the potential to do a lot of damage. From the larger implications of it being used to spread inaccurate news stories that can sway public opinion and political processes to it being used to inflict damage on individuals with scams, it’s important to know what to watch out for.

Woman with a scan on her face (Kurt “CyberGuy” Knutsson)
MORE: EXPOSING THE TOP SCAMS TARGETING COSTCO SHOPPERS
What is the ‘Yahoo Boys’ scam?
The “Yahoo Boys” scam involves a group of sophisticated cybercriminals, primarily based in Nigeria, who are using this technology to conduct what’s otherwise known as romance scams. Like some catfishing attempts, they first build trust with victims through personal and romantic interactions over messaging and, eventually, video calls, where they then manipulate their appearances in real time to match the description and profile they may have shared with them up until that point.
By doing this, they can trick the victim into trusting them even more. This is because most of us still use video as a way to verify a person’s identity, when messaging isn’t convincing enough. Finally, when the timing is right, the victims are often persuaded into transferring money based on various fabricated scenarios, leading to significant financial losses. In fact, the FBI reported over $650 million lost to romance scams like these.

Man on his cellphone (Kurt “CyberGuy” Knutsson)
MORE: DON’T FALL FOR THESE SNEAKY TAX SCAMS THAT ARE OUT TO STEAL YOUR IDENTITY AND MONEY
How does it actually work?
In the case of the “Yahoo Boys” scam, the scammers do their dirty work by:
Step 1: The scammer will use two smartphones or a combination of a smartphone and a laptop. One device is used to conduct the video call with the victim, while the other runs face-swapping software.
Step 2: On a secondary device, the scammer activates face-swapping software. This device’s camera films the scammer’s face, and the software adds a digital mask over it. This mask is a realistic replica of another person’s facial features, which the scammer has chosen to impersonate. The software is sophisticated enough to track and mimic the scammer’s facial movements and expressions in real time, altering everything from skin tone and facial structure to hair and gender to match the chosen identity.
Step 3: For the video call, the scammer uses a primary device with its rear camera aimed at the secondary device’s screen. This screen shows the deepfake – the digitally altered face. The rear camera captures this and sends it to the victim, who sees the deepfake as if it’s the scammer’s actual face. To make the illusion more convincing, the devices are stabilized on stands, and ring lights provide even, flattering lighting. This setup ensures that the deepfake appears clear and stable, tricking the victim into believing they’re seeing a real person.
Step 4: Throughout the call, the scammer speaks using their own voice, although in some setups, voice-altering technology might also be used to match the voice to the deep-faked face. This comprehensive disguise allows the scammer to interact naturally with the victim, reinforcing the illusion.
Though each deepfake scam is different, having a basic level of understanding in terms of how scams like these work can help you recognize them.

Scammer typing on a keyboard (Kurt “CyberGuy” Knutsson)
How to stay safe from deepfake scams
To protect yourself from deepfake scams like the “Yahoo Boys” scam, here’s what you can do:
Verify identities: Always confirm the identity of individuals you meet online through video calls by asking them to perform unpredictable actions in real time, like writing a specific word on paper and showing it on camera.
Be skeptical of unusual requests: Be cautious if someone you’ve only met online requests money, personal information or any other sensitive details.
Enhance privacy settings: Adjust privacy settings on social media and other platforms to limit the amount of personal information available publicly, which can be used to create deepfake content.
Use secure communication channels: Prefer secure, encrypted platforms for communications and avoid sharing sensitive content over less secure channels.
Educate yourself about deepfakes: Stay informed about the latest developments in deepfake technology to better recognize potentially manipulated content.
Report suspicious activity: If you encounter a potential scam or deepfake attempt, report it to the relevant authorities or platforms to help prevent further incidents.
By following these guidelines, you can reduce your risk of falling victim to sophisticated digital scams and protect your personal and financial information from falling into the hands of these scammers.

Woman talking on her cellphone (Kurt “CyberGuy” Knutsson)
MORE: CAN AI HELP SOMEONE STAGE A FAKE KIDNAPPING SCAM AGAINST YOUR FAMILY
Protecting your identity in the age of deepfakes
As deepfake technology becomes more accessible and convincing, the risk of identity theft increases. Scammers can use stolen personal information to create more believable deepfakes, making it harder for you to detect fraud. Furthermore, the sophistication of deepfakes may allow criminals to bypass biometric security measures, potentially granting them unauthorized access to your personal accounts and sensitive financial information. This is where identity theft protection services become invaluable.
Identity Theft companies can monitor personal information like your Social Security Number, phone number and email address and alert you if it is being sold on the dark web or being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals.
One of the best parts of using some services is that they might include identity theft insurance of up to $1 million to cover losses and legal fees and a white-glove fraud resolution team where a U.S.-based case manager helps you recover any losses. See my tips and best picks on how to protect yourself from identity theft.
By subscribing to a reputable identity theft protection service, you can add an extra layer of security, ensuring that your digital presence is monitored and protected against the ever-evolving tactics of cybercriminals like the “Yahoo Boys.”
MORE: UNFORGETTABLE MOTHER’S DAY GIFTS 2024
Kurt’s key takeaways
The main targets of the “Yahoo Boys” scam are individuals who establish online romantic relationships with the scammers. Because these victims are often emotionally invested and therefore more susceptible to manipulation, there’s not necessarily a specific age or demographic that can become a victim. And because we know the root of all these scams is the deepfake technology, truly anyone can become a target. So, we hope this helps, but also, be sure to spread the word to friends and family.
Have you heard of any other types of deepfake scams? Or do you know anyone who has been a victim of scams like this? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Financial Times signs licensing deal with OpenAI
/cdn.vox-cdn.com/uploads/chorus_asset/file/25362057/STK_414_AI_CHATBOT_R2_CVirginia_B.jpg)
The Financial Times has struck a deal with OpenAI to license its content and develop AI tools, the latest news organization to work with the AI company.
The FT writes in a press release that ChatGPT users will see summaries, quotes, and links to its articles. Any prompt that returns information from the FT will be attributed to the publication.
In return, OpenAI will work with the news organization to develop new AI products. The FT already uses OpenAI products, saying it is a customer of ChatGPT Enterprise. Last month, the FT released a generative AI search function on beta powered by Anthropic’s Claude large language model. Ask FT lets subscribers find information across the publication’s articles.
Financial Times Group CEO John Ridding says that even as the company partners with OpenAI, the publication continues to commit to “human journalism.”
“It’s right, of course, that AI platforms pay publishers for the use of their material,” Ridding says. He adds that “it’s clearly in the interests of users that these products contain reliable sources.”
-

 Kentucky1 week ago
Kentucky1 week agoKentucky first lady visits Fort Knox schools in honor of Month of the Military Child
-

 News1 week ago
News1 week agoIs this fictitious civil war closer to reality than we think? : Consider This from NPR
-

 World1 week ago
World1 week agoShipping firms plead for UN help amid escalating Middle East conflict
-

 Politics1 week ago
Politics1 week agoICE chief says this foreign adversary isn’t taking back its illegal immigrants
-

 Politics1 week ago
Politics1 week ago'Nothing more backwards' than US funding Ukraine border security but not our own, conservatives say
-

 News1 week ago
News1 week agoThe San Francisco Zoo will receive a pair of pandas from China
-

 World1 week ago
World1 week agoTwo Mexican mayoral contenders found dead on same day
-

 Politics1 week ago
Politics1 week agoRepublican aims to break decades long Senate election losing streak in this blue state















