Technology
Apple, Google, Amazon, and Facebook are always listening unless you change these settings

I take advantage of my voice to get rather a lot achieved. Siri units conferences for me, silences my telephone, and much extra. Faucet or click on for 5 easy voice instructions you’ll use on a regular basis.
An Amazon Echo might help you discover your telephone, lock the entrance door and drop in to talk with family members. Faucet or click on for the issues I at all times ask Alexa to assist with.
What’s the draw back of always-on gadgets that hear for instructions? Almost all voice-activated expertise makes use of microphones that hear for “wake phrases.” Which means they’re, technically, at all times listening.
If you wish to take management of your privateness, right here’s easy methods to cease your good gadgets from listening.
Foiling Fb
Fb generally requests entry to the microphone for video chatting and text-to-speech functions. You won’t really feel snug giving Fb management of your mic. You’ll be able to observe these steps for any app you need to block mic entry to.
Notice: There are a lot of Android producers, so the steps outlined on this article might differ out of your mannequin. In that case, test together with your mannequin’s on-line guide.
For iPhone:
- Open the Settings app. Then, scroll down and faucet Fb.
- Toggle the inexperienced change subsequent to Microphone to the off place.
It’s also possible to observe these steps:
- Open the Settings app. Then, scroll down and faucet Privateness & Safety.
- Find the menu labeled Microphone and faucet it.
- Discover Fb within the record of apps and toggle the inexperienced change to the off place.
For Android:
- Open the Settings app, then faucet Apps.
- Faucet the app you need to change, on this case Fb.
- Select Permissions. To vary a permission setting, faucet it, then select from these choices: Enable solely whereas utilizing the app, Ask each time, or Do not permit.
If you happen to determine to shoot a video or chat with a buddy, return to those settings and allow your mic. You’ll be able to at all times change it off once more while you’re completed.
A Fb emblem.
(Reuters Photographs)
AUTOMAKERS LIKE BMW, GM, AND MERCEDES CHARGE MONTHLY FEES FOR FASTER SPEEDS, HEATED SEATS AND MORE
Stopping voice assistants
It’s common information that digital assistants can decide up snippets of personal conversations should you say one thing that sounds just like the wake phrase. One research outlined 1,000 phrases that tripped up Alexa, Siri, Cortana and Google.
If you happen to’re nervous about your gadget’s always-on microphone, listed here are the steps to show it off. Simply know you’re buying and selling some comfort for privateness.
Amazon Echo
- In your Echo machine, discover the button that appears like a microphone or a circle with a line by means of it.
- Push the button. This stops the machine from passing voltage by means of the mic’s internals.
- If you happen to want to use Alexa, merely press the button once more. You’ll be able to at all times flip the mic off when not in use or throughout a personal dialog.
PRIVACY SMARTS: 30-second test each Google and Fb person should do at present
Siri
- Open the Settings app in your iPhone. Scroll down and faucet Siri & Search.
- Toggle the inexperienced change subsequent to “Pay attention for ‘Hey Siri’” to the off place.
- It’s also possible to flip off Enable Siri When Locked to stop Siri from activating if a button is pressed in your pocket.
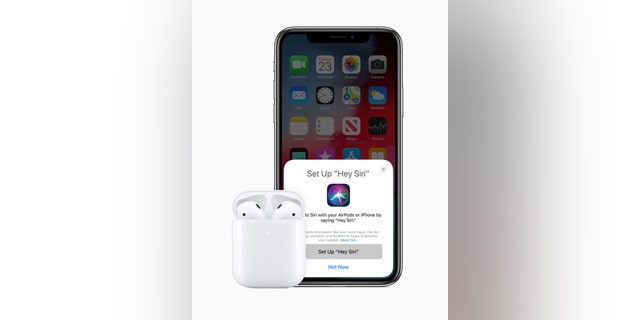
The brand new AirPods function the comfort of “Hey Siri” making it simpler to vary songs, make a name, modify the quantity or get instructions.
(Apple)
Google Assistant
On Android:
- Open the Settings app in your telephone, then select Apps.
- Underneath Normal, faucet Assistant, then See all Assistant Settings.
- From right here, you’ll be able to click on the toggle to show off “Hey Google.”
On iOS:
- Open the Settings app. Scroll down and faucet Privateness & Safety.
- Find the menu labeled Microphone and faucet it.
- Discover Google Assistant within the record of apps and toggle the inexperienced change to the off place.
Cortana on Home windows 10
- Click on the Begin Menu button, then Settings.
- Click on Privateness > Voice Activation.
- Find Microphone on the left-hand panel and click on it.
- Scroll right down to Cortana and toggle the Microphone permission to off.
Cortana on Home windows 11
- Click on the Begin Menu button, then Settings.
- Click on Privateness & Safety > Voice Activation.
- Underneath Let apps entry voice activation providers, disable Cortana.
I-SPY: CHANGE YOUR COMPUTER’S SETTINGS TO STOP PROGRAMS SPYING ON YOU
Sensible safety programs hear, too
Even residence safety gadgets have always-listening microphones. You’ll be able to disable audio recording on two common residence safety gadgets: Google Nest and Amazon Ring.
Google Nest
- Open the Nest app in your smartphone and choose the digital camera on the house display screen.
- Faucet Settings.
- Choose Microphone. Then, faucet the change to show it off.
Amazon Ring
- Open the Ring app in your smartphone and choose the machine you want to mute.
- Faucet System Settings adopted by Video Settings.
- Faucet on the Audio Streaming and Recording toggle to show off the mic.

Nest Studying Thermostat displaying Google emblem in good residence in Lafayette, California, January 17, 2021.
(Photograph by Smith Assortment/Gado/Getty Pictures)
Your good TV
If you wish to cease your good TV from listening to you and scanning your channel-surfing historical past, take a look at our detailed information to disabling these options on TVs made by Samsung, VIZIO, LG and extra.
Faucet or click on right here to see the simplest methods to cease your good TV from monitoring you
Preserve your tech-know going
My common podcast is named “Kim Komando At present.” It’s a stable half-hour of tech information, ideas, and callers with tech questions such as you from everywhere in the nation. Seek for it wherever you get your podcasts. On your comfort, hit the hyperlink beneath for a current episode.
PODCAST PICK: Cops use Fb, ChatGPT drama, prime scams spreading
Plus, easy methods to save large cash with good water tech, know recordsdata hackers use probably the most, the 5 worst tech devices that steal your privateness and callers such as you.
Try my podcast “Kim Komando At present” on Apple, Google Podcasts, Spotify, or your favourite podcast participant.
Take heed to the podcast right here or wherever you get your podcasts. Simply seek for my final identify, “Komando.”
Get extra tech know-how on The Kim Komando Present, broadcast on 425+ radio stations and obtainable as a podcast. Join Kim’s 5-minute free morning roundup for the newest safety breaches and tech information. Need assistance? Drop your query for Kim right here.
Copyright 2023, WestStar Multimedia Leisure. All rights reserved. By clicking the purchasing hyperlinks, you’re supporting my analysis. As an Amazon Affiliate, I earn a small fee from qualifying purchases. I solely suggest merchandise I consider in.

Technology
Asus won’t say if the ROG Ally’s SD card reader will ever be truly fixed
/cdn.vox-cdn.com/uploads/chorus_asset/file/24648944/asus_rog_ally_vjeran_pavic_the_verge_003.jpg)
1) Has Asus actually found a hardware fix for the faulty SD card readers? If someone RMAs their Ally to Asus this way, will they get an SD card reader that no longer fails?
Our commitment is to assist all customers effectively. If any user suspects they’re encountering issues with their products, we encourage them to reach out and make use of our RMA process as needed. They can expect us to provide a suitable resolution.
2) What percentage of ROG Ally systems have this issue?
We cannot comment on this at this time.
3) Assuming there is no hardware fix yet, why has the warranty only been extended by one year?
Apologies Sean, but we cannot comment on assumptions.
4) What does Asus plan to do for customers in territories outside the US? Will we see warranty extensions and SD card reimbursement elsewhere?
Service policies vary from region to region and are subject to local laws and regulations. While I cannot provide you a blanket statement that encompasses all global operations, you can rest assured that our focus is quality and our objective is to effectively answer our users concerns, regardless of location.
Technology
Ask Kurt: How to avoid phishing scams, protect your iPhone

In the digital age, where our lives are intertwined with technology, scammers and hackers lurk in the shadows, always on the prowl for a chance to breach our defenses. They craft their schemes with a facade of legitimacy and an air of urgency, preying on the unsuspecting. It’s a game of wits where staying one step ahead is the key to safety.
Let’s take a look at a real-life scenario that underscores the importance of vigilance:
“Two days ago I received an email (from a local store) thanking me for shopping with them. I unfortunately opened the email and it was an invoice for antivirus software that cost $399.98. I immediately called the number provided but used my landline. I only use my iPhone; don’t own a computer of any kind. Two calls didn’t get me anywhere except to worry. I called my credit card company and with [advised canceling] my credit card. No such charge was in their cue. How [did a hacker] obtain my email and what should I have [done?] I am interested in protecting my IPhone. Please respond with advice.” — Judith, Signal Mountain, Tennessee
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER
Judith, we’re sorry you had to go through that scary experience of opening what seemed like a legitimate email. Sadly, you are not the only one to suffer from this type of activity called phishing.
Hackers and scammers alike masquerade as legitimate companies or people with an urgent proposition to get you to open compromising documents or links that can endanger your security. Our digital data is readily available online, which is likely how your email address was obtained. Additionally, it’s possible that the hacker obtained your email address through a phishing attack, data breach or email harvesting. While we are glad that there were no charges on your credit card accounts, below are some steps you can take to secure your iPhone. (Android users, follow these tips.)
Man using his thumb for biometric authentication (Kurt “CyberGuy” Knutsson)
7 steps to outsmart digital intruders
1. Make sure your iPhone is secure with a passcode and biometric authentication (Face or Touch ID) enabled: Because your biometric information is unique to you, it adds a second layer of security before someone can access your phone.
2. Change your Apple ID & email account password: Your Apple ID is important for protecting your information and accessing your iPhone. Opening a phishing email may have compromised your email account. Change your email and Apple ID to unique, complex alphanumeric passwords.
3. Enable two-factor authentication for any account impacted by the phishing scam: This would include both your Apple ID and your email address. If you have this additional layer of security activated, the hacker or scammer would have to send a code to your other device or account to gain access, even with your password. When you step up the two-factor authentication, choose a device that isn’t your iPhone, if possible, so if your phone becomes compromised, you can still gain access.

Illustration of emails on smartphone (Kurt “CyberGuy” Knutsson)
MORE: HOW A FLAW IN IPHONE’S SECURITY COULD LEAVE YOU LOCKED OUT
4. Check your email settings: See if there are rules set up to forward emails. If there are any rules set up, delete any you didn’t set up so that your messages aren’t forwarded to someone else’s address.
5. Get SIM-swapping protection added to your phone: SIM-swapping fraud is when someone gains control of your cellphone number by moving it to a new SIM card. If you want to add SIM-swapping protection to your phone, you can contact your provider to see if this feature can be added.

Cyberattack warning with sign-in on iPhone (Kurt “CyberGuy” Knutsson)
FINNISH HACKER SENTENCED FOR BLACKMAILING THERAPY PATIENTS AFTER ACCESSING THOUSANDS OF RECORDS
6. Use antivirus software: The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
7. Get identity theft protection: While getting an identity theft service seems like overkill, many identity theft protection services actually provide dark web monitoring services. They continually monitor the dark web to see if any crucial pieces of personal information like your email addresses or social security number end up compromised or up for sale on the dark web. Getting those alerts immediately gives you the opportunity to act faster and take the other steps listed above. If you already gave out your information to a potential scammer, you should follow these steps to see if your identity has been stolen.
One of the best parts of using identity theft protection is that they might include identity theft insurance of up to $1 million to cover losses and legal fees and a white-glove fraud resolution team where a U.S.-based case manager helps you recover any losses. See my tips and best picks on how to protect yourself from identity theft.
MORE: UNFORGETTABLE MOTHER’S DAY GIFTS 2024
Kurt’s key takeaways
Despite our best efforts and intentions, we all will or have fallen for a phishing scam at one point or another. Instead of letting the fear of the inevitable terrorize your digital life, take the precautionary steps listed above to stay one step ahead of the scammers even if you slip up.
In what ways do you think technology companies can further enhance user security against cyberthreats? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Starfield is finally getting a 60fps mode on Xbox
/cdn.vox-cdn.com/uploads/chorus_asset/file/24884362/Starfield_04_Mountains.png)
Starfield players on Xbox will no longer have to deal with the game’s 30-frames-per-second (fps) cap. As part of an update arriving on May 15th, Bethesda will let Xbox Series X players run the game at 60fps.
The 60fps option comes as part of several new display customization settings. The game will let you choose to prioritize visuals to “[keep] the highest resolution while maintaining full detail for special effects, lighting, and crowds” or choose to prioritize frame rate performance, which will “[lower] internal resolution and detail for special effects, lighting, and crowds.” Bethesda recommends choosing the performance mode when running the game at 60fps or above.
It also recommends a variable refresh rate (VRR) display running at 120Hz, but you don’t need one to run Starfield at higher frame rates. The only downside is that you might have to deal with occasional screen-tearing, and you’ll also get fewer options to customize your display. With a VRR display, you can pick 30, 40, 60, or uncapped frame rate modes.
Several other features are coming with the May 15th update, including more detailed surface maps that should make it easier to explore your surroundings, as well as new ship customization tools and gameplay options, such as the ability to access your ship cargo from the player inventory menu. The update is available in beta on Steam now.
Down the line, Bethesda plans on adding a major Shattered Space expansion, along with a new land vehicle and official mod support. We might hear more about what Bethesda has in store for Starfield during the Xbox Games Showcase on June 9th.
-

 Education1 week ago
Education1 week agoVideo: Dozens of Yale Students Arrested as Campus Protests Spread
-

 World6 days ago
World6 days agoHaiti Prime Minister Ariel Henry resigns, transitional council takes power
-

 News1 week ago
News1 week agoLarry Webb’s deathbed confession solves 2000 cold case murder of Susan and Natasha Carter, 10, whose remains were found hours after he died
-

 Politics1 week ago
Politics1 week agoFetterman hammers 'a–hole' anti-Israel protesters, slams own party for response to Iranian attack: 'Crazy'
-

 World1 week ago
World1 week agoPeriod poverty still a problem within the EU despite tax breaks
-

 World7 days ago
World7 days agoUS secretly sent long-range ATACMS weapons to Ukraine
-

 News6 days ago
News6 days agoFirst cargo ship passes through new channel since Baltimore bridge collapse
-

 World1 week ago
World1 week agoTurkey’s Erdogan meets Iraq PM for talks on water, security and trade














