The fate of Google’s search business is now in the hands of Judge Amit Mehta, as closing arguments concluded in the landmark trial on Friday.
Technology
Tired of getting those mysterious password reset emails? Here’s what to do about it

Passwords can definitely be a frustrating part of our lives. Remembering which passwords you used for your dozens of different accounts is nearly impossible without the help of password managers.
Should you suddenly start receiving constant emails telling you that you have to reset your password for whatever reason (or sometimes with no reason listed) on top of everything else, you may be at the end of your patience.
Several reasons exist for receiving these email messages, and they can range from legitimate to scam to somewhere in between.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER
Apps on a smartphone (Kurt “CyberGuy” Knutsson)
What is a password reset email message?
When you are entering your username and password at a website to access your account, you may see a small “Forgot Password” text link. If you can’t remember your password, and you click this link, the account holding company will send you an email that allows you to reset your password. This type of email reset message, like the one below, would be a legitimate one.
However, some password reset emails you receive are fake, usually attempting to trick you into revealing your username and password to a hacker.
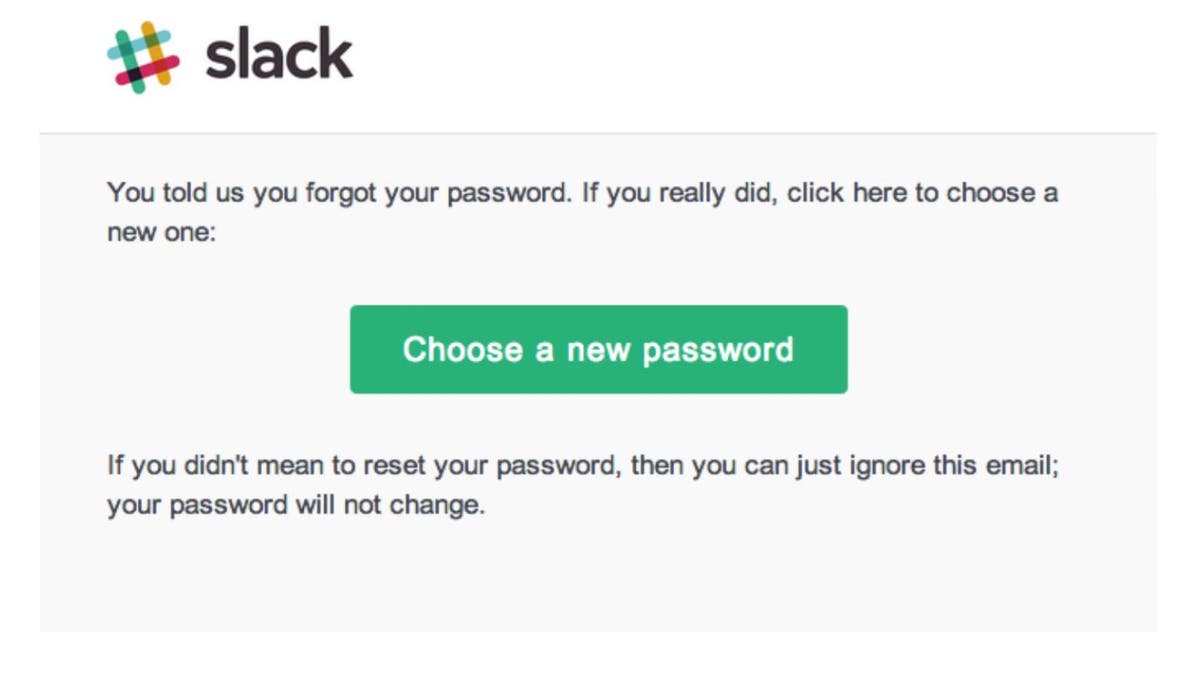
Example of legitimate password reset email (Kurt “CyberGuy” Knutsson)
MORE: THIS IS HOW YOUR EMAIL GETS INTO WRONG HANDS
Why do I receive fake password reset emails?
When you receive email messages asking you to reset a password when you did not make the request, the message could be a fake. Some of the reasons you may receive fake emails like this include:
Beware the bait: A hacker is attempting a phishing attack, hoping you’ll click on a fake link in the message.
Privacy alert: You potentially shared your email address at an unsafe website, and hackers are trying to steal your account password by tricking you into revealing it.
Security warning: Your account has some sort of security issue that is triggering these messages.
Update required: You may need to update your software or app to the latest version.

Illustration of a hacker on a laptop (Kurt “CyberGuy” Knutsson)
MORE: HOW TO KEEP YOUR ONLINE PASSWORDS SAFE
What should I do if the password reset emails are legitimate?
The password reset email message you are receiving could be a legitimate request. It may indicate that your account is under attack from a hacker. You can protect yourself in a few ways.
Go to the website directly and access your account. Then change your password to make it stronger.
Set up two-factor authentication (2FA) on your account. Should someone figure out how to hack your account password, having the second verification requirement significantly protects you.
Reach out to the website that holds your account for help with taking the necessary steps to protect yourself.
You may receive the message because you need to change your password every few months to match the requirements of the company holding the account.
Never click on a link in the email message as it could be a fake. If you click on it, you may actually give the hacker the information to take over your account rather than protect your account. The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams.
Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
Steps you can take to eliminate password reset emails
You can take a few steps to try to reduce the number of emails you receive requesting a password reset.
1. Double-check your username and password. When accessing your account, you may have a typo in your login information. Should you repeatedly attempt to access your account with this error, the company that holds the account may believe a hacking attempt is occurring, triggering an automatic reset. If your web browser automatically populates your username and password for you, make sure this information is free of typos.
RURAL TEXAS TOWNS REPORT CYBERATTACKS THAT CAUSED WATER SYSTEM TO OVERFLOW
2. Remove unauthorized devices. Some accounts maintain a list of devices authorized to use your account. If a hacker manages to gain some of your personal information, it may be able to add one of its devices to your authorized list, triggering account login errors as it tries to hack your password. Check the list of authorized devices and remove any items you don’t recognize.
The process varies, depending on the type of account. We’ll cover steps for Microsoft, Gmail, Yahoo and AOL.
Microsoft:
- From your Microsoft account home page, click on your personalized logo at the top right of the page.
- Then click My Microsoft Account
- Scroll down the page until you see your list of trusted devices.
- Click View All Devices
- On the next page, you can click Remove Device for any device you want to remove from your account.
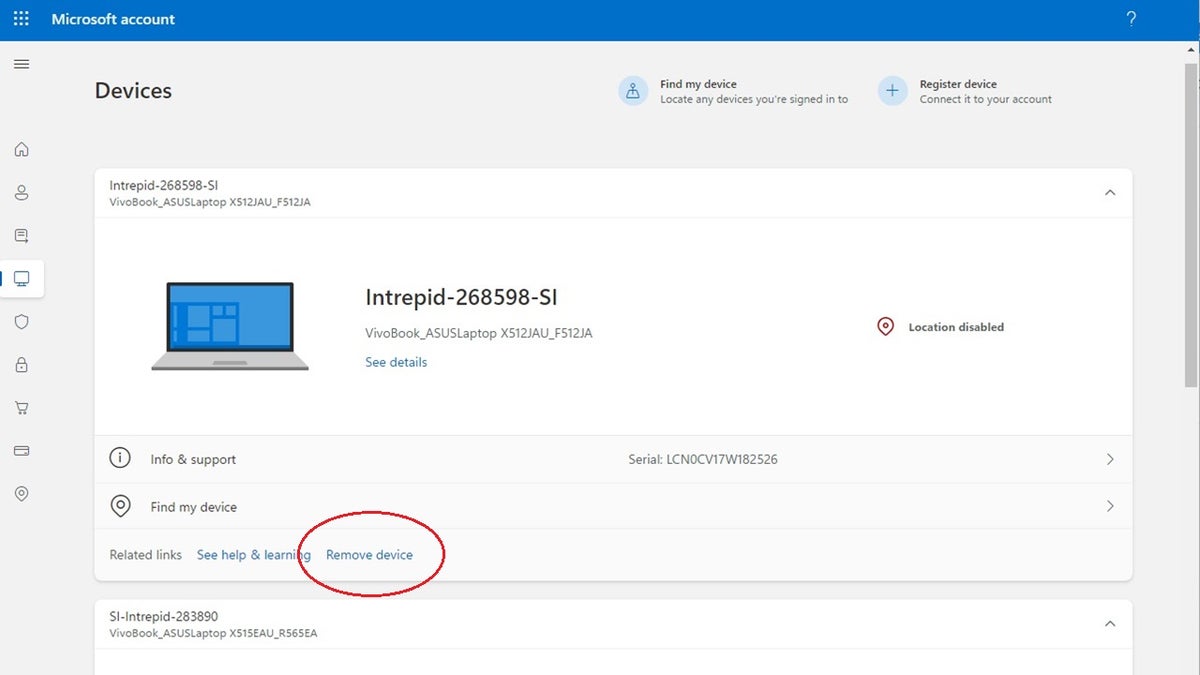
Steps to remove unauthorized devices from PC (Kurt “CyberGuy” Knutsson)
Gmail:
- Sign in to your Google Account at myaccount.google.com.
- Click the Security tab on the left side of the page.
- Scroll down to the section labeled “Your Devices” and select Manage all devices.
- You’ll see a list of devices where your Google account is currently signed in.
- If you see a device you don’t recognize, click on it and select Sign out.
Yahoo:
- Go to the Yahoo Account security page at help.yahoo.com/kb/account.
- Click on Recent activity.
- Review the list of devices and locations that have accessed your account.
- If you notice any unfamiliar activity, click Remove or Sign out next to the suspicious device.
AOL:
- Sign in to your AOL account and go to the Recent Activity page.
- Review the sections for Recent activity, Apps connected to your account and Recent account changes.
- If you find any activity or devices that you don’t recognize, click Sign out or Remove next to it.
Remember to regularly check your account settings and authorized devices to ensure the security of your accounts. If you suspect any unauthorized access, it’s also a good idea to change your passwords and review your account recovery options.
3. Sort such messages to spam. If you’d prefer to simply not see these kinds of email messages, set up your email client to sort messages like this to a spam folder. (Because many of them are spam, some email clients do this automatically.) Should you ever legitimately request a password reset, though, you’ll need to remember to look in the spam folder for the message.
4. Use a static IP address. Some accounts attempt to recognize your device through your IP address. If you have a dynamic IP address, your IP address changes constantly, meaning the account may not recognize your device, triggering the reset message. This often occurs because you are using a VPN. See if your VPN allows you to use a static IP address.

Woman holding a tablet with VPN installed (Kurt “CyberGuy” Knutsson)
MORE: WHAT HAPPENS WHEN CYBERCRIMINAL GETS ACCESS TO YOUR EMAIL ADDRESS
Kurt’s key takeaways
Although it can be frustrating to receive password reset emails, you should investigate any request like this that comes from an account you use regularly. Reach out to the customer service team for the account where you are having the issue. You may find that a simple glitch is causing the issue. Fix that, and you can put a halt to these frustrating messages. Or if it is a fake password reset email, you now know how to handle the situation to stay safe and secure.
Can you share a time when you strengthened your online security measures in response to a threat? What prompted it and how did you do it? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.

Technology
As Google’s antitrust trial wraps, DOJ seeks sanctions over missing messages
/cdn.vox-cdn.com/uploads/chorus_asset/file/24016883/STK093_Google_06.jpg)
The Department of Justice and plaintiff states made their last arguments Thursday on Google’s alleged anticompetitive conduct in the general search market, and on Friday focused on its allegedly illegal conduct in search advertising. Google was also under fire (separately) for failing to retain chat messages that the DOJ believes could have been relevant to the case.
The government is trying to show that Google locked up key distribution channels for the general search engine market, so that would-be rivals could not grow into significant threats. It says it did so through contracts with phone manufacturers and browser companies to be their exclusive default search engine. If the judge agrees that Google successfully foreclosed competition in that market, he can consider the government’s arguments about the search advertising market as evidence of anticompetitive conduct.
In his summary, DOJ attorney Kenneth Dintzer said that the last major tech monopoly decision, US v. Microsoft, “fits like a glove” on Google. Google’s lead litigator in the case, John Schmidtlein, disagreed. In Microsoft, he said, manufacturers were coerced into deals and customers were spoon-fed an inferior product they didn’t want. “Google has won with a superior product,” he said.
“The importance and significance of this case is not lost on me,” Mehta said as he concluded Friday’s court proceedings. “Not only for Google, but for the public.”
An adequate substitute for Google ads
If Google charges higher prices for advertising, are there suitable substitutes that advertisers would flee to? The answer to that question can say a lot about whether or not Google has the monopoly power that the DOJ alleges it has created through the contracts it has to be the default search engine on various browsers and devices. Google says there’s plenty of alternatives for advertisers; the government disagrees.
Mehta seemed sympathetic to the government’s arguments, though he acknowledged that alternatives to Google are robust ad companies in their own right. Amazon, for instance, isn’t exactly an inferior substitute to Google for ads, said Mehta. Unlike wrapping a sandwich in newspaper instead of cellophane, Mehta said, “If you move your ad money from Google to Amazon, you’re not wrapping your ad in newspaper.”
But Mehta later differentiated ad platforms like Facebook and TikTok from Google. Users searching on Google come with a strong idea of what they’re looking for, pretty much spelling it out in the query. Social media platforms often have to infer that intent from indirect signals.
In 2017, Google ran an experiment over several weeks and found it could increase prices five to 15 percent while still growing revenue
In 2017, Google ran an experiment over several weeks and found it could increase prices five to 15 percent while still growing revenue. “Google is able to decide on what the margin that they are going to acquire is. And that’s why they’re running experiments to say, ‘well if we up it by 15 percent, how much are we going to lose in revenue?’” Mehta said to Schmidtlein. “That’s something that only a monopolist could do, right?” Schmidtlein disagreed, saying it’s fair to run pricing experiments to figure out if they’re charging the right price.
Mehta pointed out that there was “no evidence that Google ever looks at a competitors’ pricing” for that purpose. Schmidtlein responded it wasn’t that simple. Because ads are sold through a complicated auction, not even Google has total insight into the pricing mechanism behind it. It simply isn’t the same as a Coca-Cola rep walking through a grocery store to see Pepsi’s prices.
Sabotaging ads on Bing
The plaintiff states — the attorneys general for 38 states led by Colorado and Nebraska that brought the suit alongside the DOJ — are also arguing that Google intentionally dragged its feet when building certain features for SA360, its search engine marketing tool. SA360 helps advertisers manage ads through different platforms — not just Google, but competitors like Microsoft’s Bing.
The states say that Google lagged behind in building a SA360 feature for Bing ads when it had already implemented it for Google search ads.
“The evidence here is a little bit tricky for Google,” Mehta said, noting the significance of Google having said rather publicly at the start that it was “not going to play favorites” when it came to SA360. While Google could have chosen to exclude Microsoft from the tool at the outset, “that’s not the choice they made,” Mehta said.
The tool was not delivered for nearly five years after Microsoft asked for it. “How can that not be at least inferred to be anticompetitive?” Mehta asked.
Deleted chats
Hanging over the whole case is an issue about whether Google intentionally deleted or failed to retain documents that might have been used as evidence in this trial.
Google had a policy of having “history off” on its chats by default, leaving it to employees to determine when to turn it on for relevant conversations. DOJ’s Dintzer called the alleged destruction of documents “unequivocal and honestly breathtaking.” He added that “there’s no question” executives “intentionally had conversations with history off.”
“Google’s retention policy leaves a lot to be desired,” said the judge, adding disapprovingly that it was “surprising to me that a company would leave it to their employees to decide when to preserve documents.”
“Google’s retention policy leaves a lot to be desired”
Soon after, Dintzer’s slide deck paused on a slide that simply read “This is Wrong,” as the DOJ attorney pointed out Google never apologized for the unretained documents nor promised not to do it again in the future. He said it’s imperative that the court impose sanctions that show the risk of destroying documents is not worthwhile. The DOJ is asking Mehta to make an adverse inference about Google for any element of the case where he doesn’t think plaintiffs have sufficient evidence. That would mean the judge would assume that any deleted chats would have been bad for Google and showed their anticompetitive intent behind their contracts with manufacturers and browsers. The DOJ also wants Mehta to take the destroyed chats as a signal of its anticompetitive intent.
Google attorney Colette Connor said the company’s lawyers had informed the state of Texas (one of the plaintiffs) early on about their retention policies. Dintzer said even that disclosure came months after the litigation hold and that the DOJ “clearly” would have acted had they known.
Mehta didn’t seem to buy Google’s defense. “It’s interesting to me that Google has been very deliberate — and perhaps after seeing what’s happened with Microsoft – very deliberate in advising employees in what not to say,” he said. In a training for employees, the company advised avoiding terms like “market share.” (Bloomberg Law has noted this is a common practice in large companies.)
It’s now up to Mehta to decide how those absent chats should be accounted for. He hasn’t provided a timeline for his decision, but in the meantime, Google and the DOJ will be preparing for their second antitrust face-off over advertising technology in the fall.
Technology
Creeps are hiding cameras in dressing rooms, bathrooms and worse

Stories like this make my blood boil. Some creep was caught taking pics up a woman’s skirt at a Target store. Let’s give a big cheer to the woman who called him out and filmed it.
I’m giving away a $799 iPhone 15. Try my free daily newsletter for your shot to win. My newsletter has over 209,000 positive reviews with a 4.88 out of 5 star rating!
Peeping Toms and tech are a match made in you-know-where. They use everything from smartphones to hidden cameras to get their fix. Luckily, I’m on your side to keep you and your loved ones safe.
SPAM TEXT FAQ: WHAT TO DO, WHAT NOT TO DO AND HOW TO GET LESS
Skirting around the issue
On an otherwise ordinary day in Greenville, North Carolina, a woman took a trip to her local Target. She noticed a 21-year-old man getting a little too close for comfort — crouching down on the ground near her.
When she moved, so did the man. Then she noticed his cell phone on the floor. That’s when it clicked: She was wearing a skirt that day, and this creep was trying to slide his phone underneath to get a photo.
Caught red-handed
Another Target shopper spotted the creep, too. She started filming the peeper after noticing him following the victim around the store. She captured him putting his phone on the floor and posted it to social media.
Surveillance cameras displayed outside a home security shop in Markham, Ontario, Canada, on June 24, 2023. (Creative Touch Imaging Ltd./NurPhoto via Getty Images)
Ultimately, that video is what led to the peeper’s arrest.
Of course, when the cops picked him up, he denied it all and gladly handed over his phone. Cops got a search warrant to dig deeper, and fortunately, they didn’t find any inappropriate photos of children.
The peeper was released on bond, and his fate now rests in the courts. He also won’t return to his job anytime soon. Where’d he work, you ask? An elementary school.
Protect your privacy
Whether you’re on a Target run or vacation, a Peeping Tom could be lurking. Stay safe and smart with these tips:
7 WAYS TO STOP PAYING SO MUCH ON STREAMING EVERY DANG MONTH
- Any public place is fair game for a creep. Be aware of your surroundings anywhere you change clothes, including fitting rooms, hotel rooms and gyms.
- Be on the lookout for cameras. Red flags include suspicious wires and tiny flashing lights. Cameras can also be hidden behind things like wall decor, lamps and shelves.
- Mirrors are camera hotspots. To check for one, turn off the lights in the room and shine your phone’s flashlight into the mirror.
- Don’t forget to check the toilets, too. Cameras could be hiding behind seats and tanks.
- For an added layer of protection, invest in a hidden camera detector and keep it in your purse. If you want to go the free route, there are also hidden camera detection apps for iPhone and Android. Just don’t expect stellar results.
What about rentals? Yes, you need to check there, too
I once found about a dozen cameras throughout a house I rented, but they were only disclosed in small type at the very bottom of the listing. It was clear they wanted me to miss that warning.
Given all the coverage about hidden cameras spotted in rentals, I’m not surprised Airbnb just banned indoor cameras. If anything, I’m shocked it took this long.
Checking around a small dressing room is one thing. Making sure your entire rental property is creep-free is a bigger job.

The Xiaomi Smart Camera C500 Pro is being showcased at the Mobile World Congress 2024 in Barcelona, Spain, on March 8, 2024. This latest surveillance camera from the Chinese company features smart detection capabilities for pets, baby sounds, or strong noises. (Joan Cros/NurPhoto via Getty Images)
Here’s how to find them
Larger cameras are easy to spot, but anyone can easily hide smaller cameras behind furniture, vents or decorations. A simple way to spot most types of cameras is to look for the lens reflection.
- Turn off the lights and slowly scan the room with a flashlight or laser pointer, looking for bright reflections.
- Scan the room from multiple spots so you don’t miss a camera pointed only at certain places.
- Inspect the vents and any holes or gaps in the walls or ceilings.
You can also get an RF detector. This gadget can pick up wireless cameras you might not see. Unfortunately, RF detectors aren’t great for wired or record-only cameras. For those, you’ll need to stick with the lens reflection method.
If you can connect to the rental’s wireless network, a free program like Wireless Network Watcher shows what gadgets are connected. You might be able to spot connected cameras that way. I do this in every rental I stay in, just to double-check what’s connected to the network.

The Google Nest Cam, an indoor and outdoor smart security camera developed by Google’s home safety brand, is on display on Android Avenue at the Mobile World Congress in Barcelona, Spain, on March 25, 2024. (Joan Cros/NurPhoto via Getty Images)
Be aware that the owner might have put the cameras on a second network, or they could be wired or record-only types, so this is not a fail-safe option.
Get tech-smarter on your schedule
Award-winning host Kim Komando is your secret weapon for navigating tech.
Copyright 2024, WestStar Multimedia Entertainment. All rights reserved. As an Amazon Associate, I earn a small commission from qualifying purchases. I only recommend products I believe in.
Technology
Microsoft needs some time to ‘refine’ updates for Copilot AI in Windows
/cdn.vox-cdn.com/uploads/chorus_asset/file/25357666/STK259_MICROSOFT_COPILOT_2__A.png)
Microsoft’s latest Windows Insider blog posts say that when it comes to testing new Copilot features in Windows 11, “We have decided to pause the rollouts of these experiences to further refine them based on user feedback.” For people who already have the feature, “Copilot in Windows will continue to work as expected while we continue to evolve new ideas with Windows Insiders.”
We’re expecting to see new Surface laptops powered by Qualcomm’s Snapdragon X Elite processors that run Windows on Arm and compete with Apple’s M3-powered MacBook Air. Meanwhile, new features for Windows are expected to include an AI Explorer app that resembles the old Windows 10 Timeline feature that remembered what you were doing and allowed users to pick up tasks across different devices, and play up the idea of a “Copilot for every person.”
Copilot features Microsoft recently tested in the preview include one where the Copilot taskbar icon animated to show when the AI assistant could help. You could then hover the mouse icon over it to see your options, like getting an AI-generated summary of text.
Another allowed Copilot in Windows to pop out of the sidebar and into a normal application window, which users could resize and move around. This feature started rolling out to the Canary channel in March.
New builds going out to both the Dev and Beta channels include a fix for Copilot unexpectedly auto-launching after a restart. There’s also a new shortcut in the right-click menu for tabs in File Explorer, allowing users to duplicate the current tab. But for those who keep a close eye on Task Manager, the most important note of all is that Microsoft has updated the units to correctly reflect memory speed, going from the MHz of yesteryear to a DDR-ready MT/s count.
-

 News1 week ago
News1 week agoLarry Webb’s deathbed confession solves 2000 cold case murder of Susan and Natasha Carter, 10, whose remains were found hours after he died
-

 News1 week ago
News1 week agoFirst cargo ship passes through new channel since Baltimore bridge collapse
-

 World1 week ago
World1 week agoHaiti Prime Minister Ariel Henry resigns, transitional council takes power
-

 World1 week ago
World1 week agoSpanish PM Pedro Sanchez suspends public duties to 'reflect'
-

 World1 week ago
World1 week agoUS secretly sent long-range ATACMS weapons to Ukraine
-

 News1 week ago
News1 week agoAmerican Airlines passenger alleges discrimination over use of first-class restroom
-

 Movie Reviews1 week ago
Movie Reviews1 week agoHumane (2024) – Movie Review
-

 Education1 week ago
Education1 week agoVideo: Johnson Condemns Pro-Palestinian Protests at Columbia University
:max_bytes(150000):strip_icc():focal(750x171:752x173)/jason-mckenzie-plane-crash-050324-1-fd5c599f2f784db28a4d1be83a76e5b0.jpg)














