Technology
How to spot fake Russian social media accounts and posts

Younger Males Utilizing Sensible Cellphone Social Media Idea (iStock)
NEWNow you can take heed to Fox Information articles!
Because the Russia-Ukraine Battle escalates, cable information rankings have skyrocketed. However take a look at what they’re exhibiting you: Social media posts and on-line influencers.
There is no query the Ukraine invasion is a social media struggle — the world’s first. Many TV interviews are with Ukrainians who’re garnering massive social media followings. TikTok is stuffed with video clips of after bombing scenes and bomb shelters. They’re shot on smartphones by residents and shared straight with the world, bypassing conventional media retailers.
Right here at dwelling, my connections within the cybersecurity world say cyberattacks are getting extra subtle and can goal companies and peculiar residents such as you and me. Faucet or click on right here for 5 issues it’s essential replace proper now, beginning along with your router.
Amongst real posts and movies you’re sure to run into fakes, previous footage, and deceptive data. Right here’s find out how to spot the junk, so you do not unwittingly share it.
Have a crucial eye
Sharing is at all times one click on away on social media. Not many individuals take the time to analysis earlier than spreading an article, photograph, or video — particularly when it comes from a buddy or on-line character you belief.
Russia’s propaganda machine is working at full throttle. Utilizing synthetic intelligence, Russia is creating pretend accounts of Ukrainians who supposedly agree with the invasion of their nation on Fb, Instagram, Telegram, and Twitter.

A destroyed armored car is seen in entrance of a college which, in line with native residents, was on fireplace after shelling, as Russia’s invasion of Ukraine continues, in Kharkiv, Ukraine, Feb. 28, 2022.
(REUTERS/Vitaliy Gnidyi)
These accounts say Ukraine is a “failed state,” and President Volodymyr Zelensky is “constructing a neo-Nazi dictatorship.” The accounts typically say the particular person works for a information group or represents some political motion in Ukraine to construct credibility.
Need to see an instance? Meet Vladimir Bondarenko.
NBC Information Senior Reporter Brian Collins found Vladimir Bondarenko and posted about him that, “He’s a blogger from Kiev who actually hates the Ukrainian authorities. He additionally doesn’t exist, in line with Fb. He’s an invention of a Russian troll farm concentrating on Ukraine. His face was made by AI.”
When you look intently at Vladimir Bondarenko’s face, there seems to be a chunk lacking out of the highest of his left ear. That’s the issue with AI. It typically misses the main points.
Have you ever ever checked out a picture and had an eerie feeling that one thing was off? Take heed to your instinct.
Are there landmarks or notable buildings in a photograph? What time of yr is it? Are you able to see any clocks or different indicators of time?
It’s not simply repurposed photographs, both. In the present day’s deepfake expertise makes it comparatively straightforward to pretend absolutely anything. Faucet or click on for 10 Russia-Ukraine struggle scams and cons spreading proper now.

A number of buildings in Starobilsk inside the Luhansk Oblast area of Ukraine present important harm due to shelling, in line with pictures shared by the State Emergency Service of Ukraine.
(State Emergency Service of Ukraine)
Discover the primary use
Previous pictures and movies are inclined to go viral throughout a battle, pure catastrophe, or emergency. Following the Russian invasion into Ukraine, a video of a dramatic explosion was shared tens of hundreds of instances. The footage was precise, but it surely confirmed the 2020 blast in Beirut.
There are a couple of instruments that may provide help to spot recycled content material. Begin with Google Photos.
You’ll be able to search the web utilizing a picture as an alternative of phrases. While you run a photograph by way of Google Photos, it’ll search and discover different pictures prefer it so you’ll be able to decide the photograph’s origin. It is going to additionally pull up modified and amended variations.
- To seek for a picture, you’ll be able to:
- Drag the picture to the Google Photos search subject.
- Copy the picture’s URL and paste it into the search engine.
- Proper-click on any picture in Chrome and hit “Search Google for picture.”
TinEye.com is one other reverse picture search choice. Pictures are checked in opposition to its in-house index, containing over 52.6 billion pictures.
Professional Tip: Are you normally scrolling social media or information websites in your cellphone? Faucet or click on for a couple of methods to do a reverse picture search out of your smartphone.
Go on a fact-finding mission
Whether or not you’re taking a look at photographs, movies, or simply textual content, the extra details you realize, the tougher you’re to idiot. The place do you have to begin? Many information organizations are dedicating sources to debunking phony viral content material. Right here’s a listing of truth checks accomplished by the Related Press.
Unbiased teams are doing the identical. Bellingcat is “an impartial worldwide collective of researchers, investigators and citizen journalists” researching data spreading on the Russia-Ukraine Battle. Faucet or click on right here for a listing of Bellingcat’s fact-checked claims.

Hundreds of protesters supporting Ukraine gathered in Washington, D.C. and demanded the Biden administration present extra assist
(Fox Information Digital/Lisa Bennatan)
Metadata tells a narrative, too
Not everybody who posts photographs or movies on-line realizes these information comprise lots of figuring out data. Are you giving freely greater than you notice? Faucet or click on to see how one can sleuth out particulars in your personal photographs or photographs saved to your pc or cellphone.
When you run throughout a photograph and wish to know the place it got here from or when it was shot, use a web-based instrument to look at the metadata. Attempt exifdata or metapicz to see in case you can flip up any fascinating data. You’ll be able to take a look at metadata utilizing enhancing software program like Photoshop, too.
One factor to notice is that social media websites typically strip out metadata to guard consumer privateness. Until a photograph is shared with you straight or by way of a messaging app, you will have extra luck utilizing Google Photos or TinEye.
Report false and deceptive posts while you see them
When you come throughout pretend pictures or deceptive posts, report them. Whether or not that’s Fb or a good information web site, take the time to level out that the knowledge is wrong.
With pretend pictures comes false data, and that may trigger critical issues. Do your half to discern truth from fiction early and infrequently.
Bonus Tip: Ukraine Battle: The risks, scams and hacks it’s essential look ahead to + your calls
Russia has invaded Ukraine and there are fears it might result in cyber warfare — even right here within the U.S. Discover out what it might imply for you. Plus, 10 new struggle cons scammers are utilizing to idiot individuals.
Try my podcast “Kim Komando Explains” on Apple, Google Podcasts, Spotify, or your favourite podcast participant.
Take heed to the podcast right here or wherever you get your podcasts. Simply seek for my final title, “Komando.”
What digital life-style questions do you will have? Name Kim’s nationwide radio present and faucet or click on right here to search out it in your native radio station. You’ll be able to take heed to or watch The Kim Komando Present in your cellphone, pill, tv, or pc. Or faucet or click on right here for Kim’s free podcasts.
Copyright 2022, WestStar Multimedia Leisure. All rights reserved. By clicking the procuring hyperlinks, you’re supporting my analysis. As an Amazon Affiliate, I earn a small fee from qualifying purchases. I solely advocate merchandise I consider in.
Find out about all the most recent expertise on The Kim Komando Present, the nation’s largest weekend radio discuss present. Kim takes calls and dispenses recommendation on at the moment’s digital life-style, from smartphones and tablets to on-line privateness and information hacks. For her every day ideas, free newsletters, and extra, go to her web site at Komando.com.

Technology
Volvo announces pricing for delayed EX30 compact SUV
/cdn.vox-cdn.com/uploads/chorus_asset/file/25840576/318876_Volvo_EX30_Cloud_Blue_Exterior.jpg)
The compact Volvo EX30 is finally arriving in the US — and with it comes some more clarity about its price.
When it was first announced in 2023, the EX30 was positioned as a smaller, more affordable electric vehicle in a market overflowing with expensive, luxury models. And it seemed poised to win over a lot of converts, with a starting price of just $34,950.
At that time, the only other EVs available for a similar price were the utilitarian Chevy Bolt and Nissan Leaf. You could also find a few used EVs, or even a stripped down Tesla Model 3, but the idea of a luxuriously appointed (if bare bones) European model for just under $35,000 was unheard of.
Today, Volvo announced that the most popular trim of the EX30 is finally coming to the US. That would be the EX30 Twin Motor Performance with 422 horsepower, starting at $44,900 for the Plus equipment package (not including delivery charges). Upgrading to the Ultra package will cost $46,600.
That’s decidedly more than $34,950 — and unfortunately Volvo didn’t say when we can expect that more affordable version to arrive stateside. Given the political situation here, I can hardly blame Volvo for playing it close to the vest when it comes to EV sales in the US. The Trump administration is promising fewer incentives and more tariffs — both of which likely add up to higher prices for car shoppers.
Still, the EX30 has been a runaway hit in Europe, with Volvo recording over 100,000 sales of the pint-sized SUV. In August, that was only bested by the Tesla Model Y. It stands to reason that US customers will react similarly — once they get their hands on it.
Volvo has two other EVs in the US: the mid-sized EX40, which starts at $52,500 for the single-motor variant and goes all the way up $60,750 with all the bells and whistles; and the full-sized, three-row EX90, which starts at $79,995 and tops out at $89.845. Delivery charges bring these prices up by at least $1,000.
Technology
Does your Windows 11 PC keep restarting? Let's fix that frustrating problem

Experiencing a Windows 11 boot loop can be incredibly frustrating, transforming your computer into a seemingly endless cycle of restarts that disrupts productivity. When your system continuously fails to load the login screen and instead repeatedly attempts to restart, you’re facing a critical technical issue that demands immediate attention.
This persistent reboot problem can stem from various causes. So, what do you do? Let’s look at some ways to diagnose and resolve the Windows 11 boot loop, helping you restore your computer’s functionality and get back to work.
I’M GIVING AWAY THE LATEST & GREATEST AIRPODS PRO 2
Enter the giveaway by signing up for my free newsletter.
Windows 11 PC (Microsoft) (Kurt “CyberGuy” Knutsson)
What causes a Windows 11 PC to keep restarting?
There’s no single cause for a Windows 11 PC getting stuck in a reboot loop. A reboot loop can be caused by an issue with your computer’s power supply, a malware infection, overheating or even hardware drivers. Here are the different things to check if your Windows 11 laptop or desktop keeps restarting.
Fix #1 – Boot your PC in safe mode
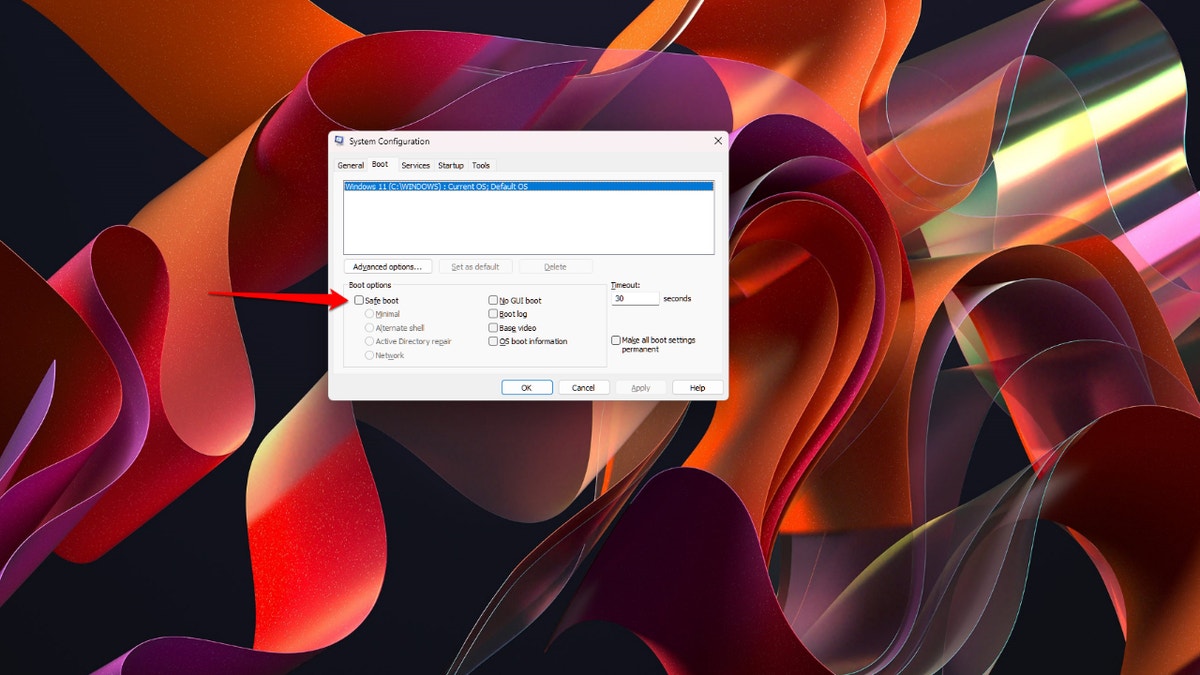
Step to boot your PC in safe mode (Kurt “CyberGuy” Knutsson)
When you are troubleshooting any problem on your PC, you should boot your computer in safe mode. If your PC is in safe mode and no longer experiences the restart loop, this means that the default Windows 11 settings and drivers aren’t causing the issue. This allows you to narrow down the sources of problems causing your Windows 11 PC to crash, making it easier to troubleshoot. Here’s what you need to do to boot in safe mode:
- Press the Windows Logo key and R at the same time
- Type msconfig in the box
- Press OK
- Under Boot Options, click the Safe Boot checkbox
When your computer restarts, it will automatically restart in safe mode. If your computer restarting is making it difficult to follow these steps, you can also follow these steps at the sign-in screen:
- Hold the Shift key while clicking the Power icon
- Select Restart
- Your PC will restart
- Once your PC restarts, you will see a Choose option; click it.
- Select Advanced Options
- Select Startup Settings
Now, when your PC restarts, you will be presented with a list of options. Select 4 or F4 to start your PC in safe mode. If you need to use the internet while the computer is in safe mode, you can select option 5 or press F5.
WINDOWS 11 TIPS AND TRICKS YOU DIDN’T KNOW YOU NEEDED
Fix #2 – Remove any new software
If your automatic rebooting problem began after installing a new app, uninstall that app and monitor your PC. If you still notice your PC restarting, there’s a chance that the app has infected your system settings before you uninstalled it. To fix this, you’ll need to restore the system. To do a system restore, you should first boot your PC in safe mode and then follow these steps:
- Open the Control Panel
- Search the Control Panel for Recovery
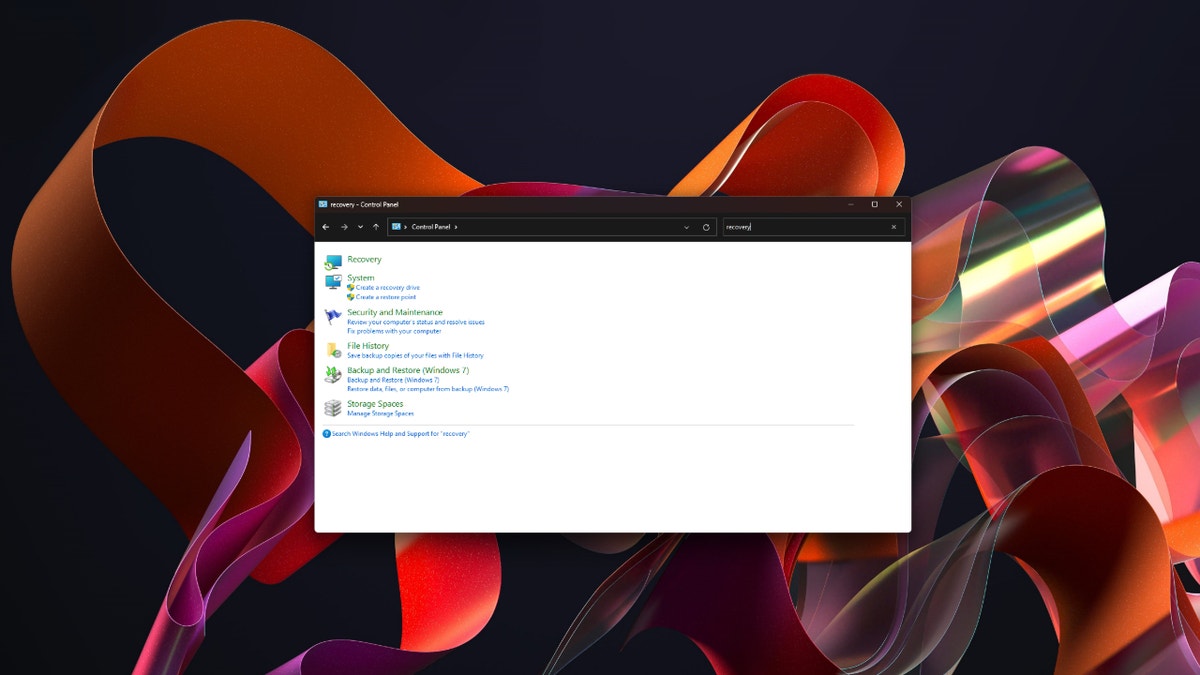
Step to remove any new software (Kurt “CyberGuy” Knutsson)
- Select Recovery
- Choose Open System Restore
- Click Next
- Now you will click on your hard drive and select finish. Your computer will automatically restart.
Fix #3 – Make sure your computer isn’t overheating
An overheating laptop or desktop will try to prevent damage to critical hardware components by shutting itself down. This is one of the leading causes of a Windows 11 PC getting stuck in a restart loop. If you’ve noticed your desktop giving off a lot more heat than usual or a laptop feeling hot to the touch, chances are you have an overheating issue.
A computer’s CPU and GPU generate the most heat, so I recommend monitoring those hardware pieces to see if they are overheating. You don’t need any additional software to monitor the temperatures of your GPU, as some temperature readings are built into Windows 11. Here’s how to check your hardware temperatures in Windows 11:
- Open the Task Manager
- Click the second tile, Performance, on the left-hand side of your screen
- From here, you can click GPU, which will show you your GPU temperature.
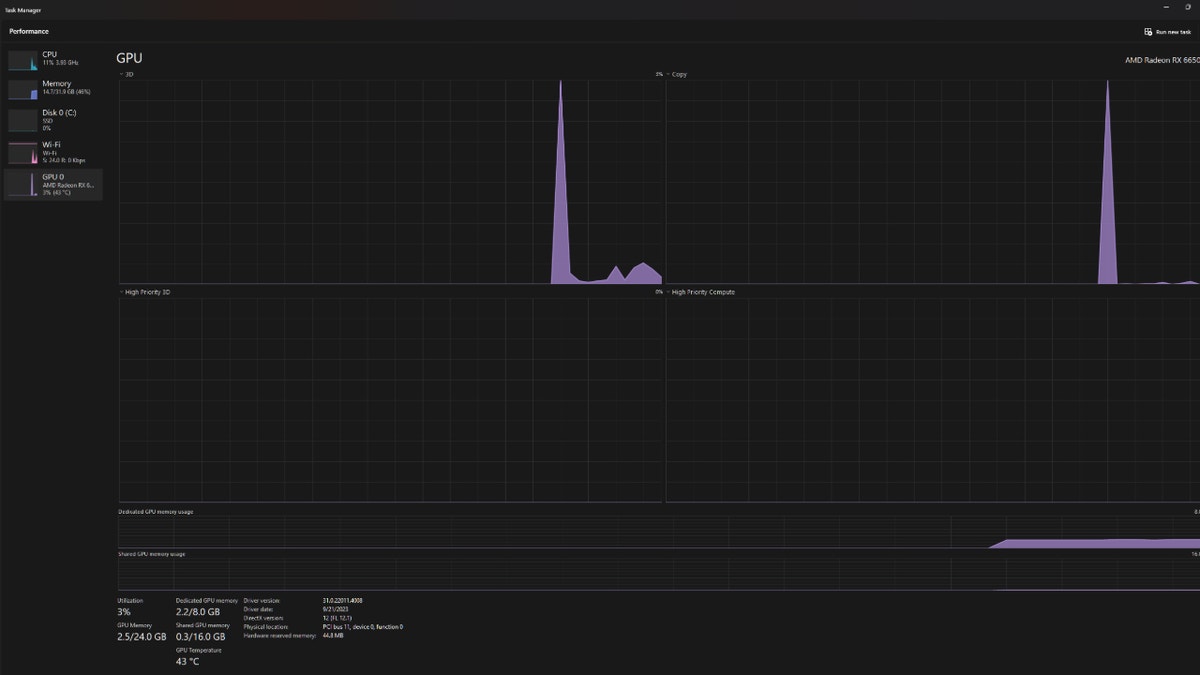
Visual to show overheating on PC (Kurt “CyberGuy” Knutsson)
Unfortunately, the built-in temperature reading doesn’t read your CPU temperature, and you’ll need to manually go into the UEFI/BIOS to check the temperature without installing any additional software. However, there’s a multitude of free-to-use apps that manufacturers have developed to measure your CPU temperature, including Core Temp, HWMonitor or Open Hardware Monitor.
When you open one of these monitoring tools, you’ll be able to view your PC’s stats, including CPU and GPU temperatures and loads. If your CPU or GPU is running too hot, try cleaning the components to remove dust. For custom-built desktops, adding more exhaust fans to the case can improve airflow and cooling. Persistent overheating, especially in older laptops, may indicate that it’s time to consider upgrading your machine.
TAKE YOUR WINDOWS PC’S SECURITY TO THE NEXT LEVEL
Fix #4 – Check for issues with your PC’s power supply

Image of a PC’s power supply (Kurt “CyberGuy” Knutsson)
A computer will randomly restart when it has a failing power supply unit (PSU). If you have an issue with your power supply, you’ll know if your computer won’t restart or turn on. In addition to causing shut-offs and restart loops, a faulty power supply can also cause a blue screen of death error. In severe cases, you might even smell a burning scent or witness smoke coming from your PC’s power supply exhaust vent. If you use a laptop with PSU issues, you cannot send your computer to a repair shop or the manufacturer for repair.
Desktop PC owners have it a bit easier, assuming they have a pre-built PC that can be altered easily. If you do have a desktop, turn off and unplug your computer before going into the case to investigate if dust build-up is affecting your PSU. If your PSU fails, you must purchase and install a new one.
Fix #5 – Scan your PC for viruses

Image of a woman working on a PC (Kurt “CyberGuy” Knutsson)
Malware and other viruses are a common cause of a crashing or constantly restarting PC. The easiest way to do this is by using strong antivirus software. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
If your computer is stuck rebooting, you may need to boot in safe mode in order to run an antivirus application. Here’s what you need to do to boot your PC in safe mode with Windows 11:
- When your computer restarts, at the sign-in screen, press and hold the Shift key
- Click Power
- Click Restart
Now, your computer should act more stable after booting in safe mode, allowing you to run an antivirus scan.
10 USEFUL WINDOWS KEYBOARD SHORTCUTS YOU NEED TO KNOW
Fix #6 – Disable automatic restart
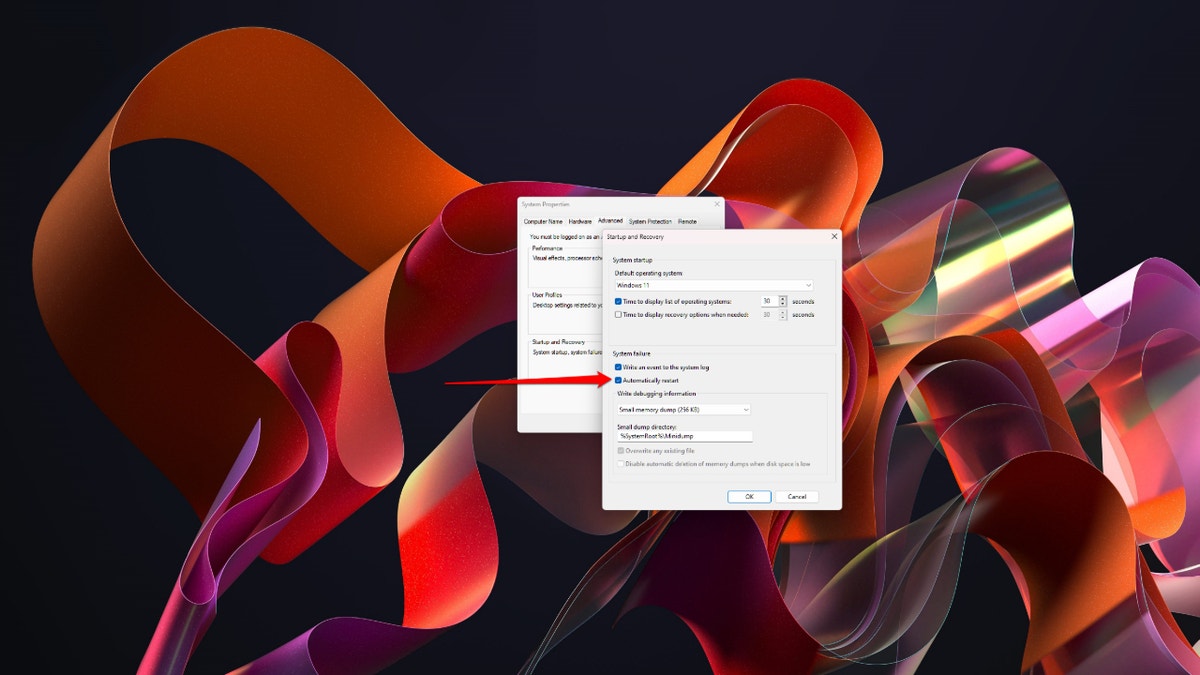
Step to disable automatic restart (Kurt “CyberGuy” Knutsson)
If you have automatic restart enabled in Windows 11, your PC will restart every time it encounters a system failure. You can easily disable this future within the Windows 11 command prompt. Here’s what you need to do:
- Press the Windows key + R on your keyboard
- Type sysdm.cpl and click OK
- Select the Advanced tab
- Under Startup and Recovery, click Settings
- Under System Failure, uncheck the box Automatically restart
- Click OK
Keep in mind this isn’t a fix for the problem, but it will help you further troubleshoot the restart loop problem by disabling automatic restarts.
Fix #7 – Repair your system files
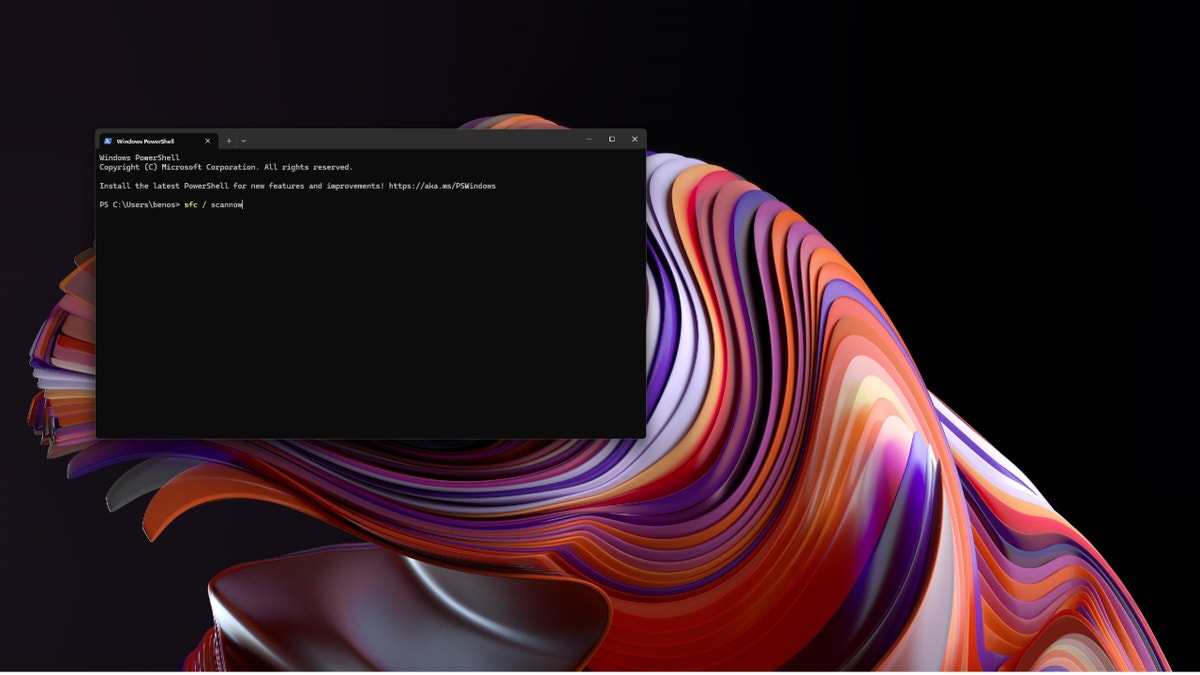
Step to repair your system files (Kurt “CyberGuy” Knutsson)
An issue with your Windows 11 system files may be causing your PC to constantly restart. If you think a corrupted system file is why your PC keeps restarting, there’s a quick and easy fix you can do within the Windows Powershell. The System File Checker (SFC) is a built-in tool that will scan your Windows system files for corruption or any other changes. If a system file has been modified, it will automatically replace the file with the correct version. Here’s how to run the SFC command:
- Open the Windows Powershell (or Command Prompt)
- Type in sfc /scannow
- Press Enter
- Leave the command prompt window open until the command completes, which could take some time
If there’s no problem with your Windows system files, after the scan, you’ll see a message that says, “Windows Resource Protection did not find any integrity violations.” If you instead see a message saying, “Windows Resource Protection found corrupt files but was unable to fix some of them,” you should try running SFC again but in safe mode.
Fix #8 – Check for RAM issues in the command prompt
Your PC might be restarting itself because it doesn’t have access to enough random access memory (RAM). Windows 11 may become unstable without enough RAM in your computer, causing the OS to randomly reboot. You can use the built-in Memory Diagnostics Tool in Windows 11 to check your computer for issues related to RAM. Here’s what you need to do:
- Press the Windows Key and R
- Type mdsched.exe in the text box
- Click OK
- Select Restart Now and Check for Problems
When your PC restarts, the Windows Memory Diagnostics Tool will check for any RAM-related issues; if the test detects an error, take note of the error code. You can check the error code online to find the correct fix for that specific error.
Kurt’s key takeaways
These are the best fixes for a computer that is constantly restarting. While you can perform these fixes at home, it might be your best bet to send your computer to a repair shop or back to the manufacturer if you continue having an issue with your Windows 11 PC being stuck in a restart loop after these fixes. It also may be time to invest in a new laptop if you are experiencing a system slowdown and random restarting on your Windows 11 PC, but I would recommend trying to fix the problem first before buying a new machine.
What was the most challenging computer technical issue you’ve ever encountered, and how did you resolve it? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover. Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Marvel Snap is back in the US
/cdn.vox-cdn.com/uploads/chorus_asset/file/25839948/ss_3022e8dd7eb67c45006bfcbca7c6260abafbe8d7.jpg)
Marvel Snap is back online in the US after access was cut off Saturday night due to the law that banned TikTok and other ByteDance-owned apps. The game’s current publisher, Nuverse, is owned by ByteDance.
In a post published Monday evening, the game’s developer, Second Dinner, says that it plans to bring “more services in-house” and “partner with a new publisher” to prevent a similar situation from happening again. The same message is also showing up when you play the game, as shown in a screenshot posted on Reddit.
The game is still unavailable on the App Store or Google Play. The Steam listing is still live.
TikTok restored service after about half a day of being offline, though the app is still absent from app stores. President Donald Trump signed an executive order on Monday refusing to enforce the law banning TikTok and other apps owned by ByteDance, The Protecting Americans from Foreign Adversary Controlled Applications Act, for 75 days, but companies still may face risks if they don’t follow the law.
-
/cdn.vox-cdn.com/uploads/chorus_asset/file/23935558/acastro_STK103__01.jpg)
/cdn.vox-cdn.com/uploads/chorus_asset/file/23935558/acastro_STK103__01.jpg) Technology1 week ago
Technology1 week agoAmazon Prime will shut down its clothing try-on program
-
/cdn.vox-cdn.com/uploads/chorus_asset/file/25826211/lorealcellbioprint.jpg)
/cdn.vox-cdn.com/uploads/chorus_asset/file/25826211/lorealcellbioprint.jpg) Technology1 week ago
Technology1 week agoL’Oréal’s new skincare gadget told me I should try retinol
-
/cdn.vox-cdn.com/uploads/chorus_asset/file/25832751/2192581677.jpg)
/cdn.vox-cdn.com/uploads/chorus_asset/file/25832751/2192581677.jpg) Technology6 days ago
Technology6 days agoSuper Bowl LIX will stream for free on Tubi
-

 Business1 week ago
Business1 week agoWhy TikTok Users Are Downloading ‘Red Note,’ the Chinese App
-
/cdn.vox-cdn.com/uploads/chorus_asset/file/25835602/Switch_DonkeyKongCountryReturnsHD_scrn_19.png)
/cdn.vox-cdn.com/uploads/chorus_asset/file/25835602/Switch_DonkeyKongCountryReturnsHD_scrn_19.png) Technology4 days ago
Technology4 days agoNintendo omits original Donkey Kong Country Returns team from the remaster’s credits
-

 Culture3 days ago
Culture3 days agoAmerican men can’t win Olympic cross-country skiing medals — or can they?
-
/cdn.vox-cdn.com/uploads/chorus_asset/file/24774110/STK156_Instagram_threads_1.jpg)
/cdn.vox-cdn.com/uploads/chorus_asset/file/24774110/STK156_Instagram_threads_1.jpg) Technology1 week ago
Technology1 week agoMeta is already working on Community Notes for Threads
-

 Politics4 days ago
Politics4 days agoU.S. Reveals Once-Secret Support for Ukraine’s Drone Industry














