Technology
7 tech gems that make life easier and save you time

Renderings of the iPhone X, finances iPhone, and iPhone X Plus (left to proper) (Ben Geskin)
NEWNow you can hearken to Fox Information articles!
Our on a regular basis gadgets make life simpler, however they are often large time sucks.
Are you continuously checking your cellphone? You’re not alone. Faucet or click on for confirmed settings that will help you break your cellphone habit.
Possibly you’re slowed down and annoyed by an outdated laptop computer or desktop pc. Earlier than you hand over and purchase a brand new one, you’ll be able to possible pace yours up and get extra life from it. Faucet or click on for my five-minute tech repair for a quicker PC.
Doesn’t saving time really feel nice? Preserve going. Listed below are seven nifty methods tech can assist you streamline your life.
1. Measure your coronary heart price along with your cellphone
You don’t want a smartwatch to measure your coronary heart price. Cardiio: Coronary heart Charge Monitor is an iPhone app that makes use of your cellphone’s digicam to take a studying of your pulse. Place your index finger on the again digicam, and the app will measure your coronary heart price by detecting colour adjustments. Make sure you maintain your cellphone regular and hold nonetheless. It really works with iPads, too.
For Android, Coronary heart Charge Monitor works equally. Cowl the again digicam, keep nonetheless, and also you’ll get a studying.
Simply bear in mind, apps like this will not be a substitute for seeing a medical skilled or speaking to your physician in the event you’re not feeling properly.
For extra smartphone smarts, take a look at this improbable listing of 10 iPhone methods I exploit every single day, and you’ll, too.
2. Get extra legroom in your subsequent flight
Google Flights is terrific for determining one of the best and least expensive option to get from level A to level B. However would not or not it’s nice additionally to know if you are going to be scrunched in somewhat seat the entire time?
Get the Chrome browser extension referred to as Legroom for Google Flights. When utilizing Google Flights, you may additionally see how a lot legroom there may be per seat by the flight you chose.
One other stable possibility is SeatGuru.com. Enter your airline and flight quantity, and you will see a map of one of the best seats with essentially the most legroom, no obtain required.
Hitting the street quickly? Listed below are 10 journey ideas even seasoned vacationers can profit from.

3. Submit to all of your social media accounts directly
Social media is enjoyable, but it surely may also be a number of work. You’ll be able to spend approach too lengthy crafting the appropriate tweet, the appropriate Fb submit, an Instagram picture, then … properly, you already know.
Right here’s a secret that influencers and entrepreneurs have recognized for years: Social media scheduling apps streamline the method. You’ll be able to create a draft of a submit with textual content, photos, or anything your coronary heart wishes. Then, choose the time you need the submit to go up. You’ll be able to create completely different variations for every social media community, too.
I like Buffer as a result of it has a free possibility. You’ll be able to handle as much as three social media channels for free of charge. In case you run a small enterprise or have extra channels to handle, paid plans begin at $60 per yr.
RELATED: True or false: Folks can see the embarrassing belongings you “like” on social media
4. Observe your tax refund on-line
Anticipating your tax refund within the mail? Right here’s an insider secret to get the submit workplace to ship you an electronic mail with photos of your mail.
Your first cease is on the USPS web site, USPS.com.
Right here, you’ll see an possibility to join Knowledgeable Supply. This free service sends residential and P.O. field prospects grayscale photos of the mail arriving that day.
These photos embrace the entrance of the envelope, so your envelope will present the IRS because the sender if it is your tax refund.
With Knowledgeable Supply, you can too handle any packages arriving, depart supply directions or reschedule a supply.
Professional-tip: The pictures despatched through USPS solely present you the primary 10 items of your mail for that day. To see the remaining, register to your account at USPS.com or skip the e-mail altogether and use the free USPS app. Obtain for Android right here or get it for iPhone right here.

A truck carrying greater than 100 packages in Maryland was carjacked by 5 suspects Thursday morning. The packages had been unloaded and the 2 supply drivers had been unhurt, authorities mentioned.
(AP)
5. Promote your stuff with out assembly in a car parking zone
Craigslist was the go-to option to promote your outdated stuff on-line again within the day. Today, there are much more choices.
You should use Decluttr to promote tech devices, like outdated telephones, computer systems, tablets, and good residence gear. There’s no must create an inventory, write an outline, add pictures, or negotiate with patrons. Merely add details about the gadgets you wish to promote, and also you get a proposal.
You will not must dig out the outdated charger, authentic field, or any equipment. The worth you are provided is for the system solely. The payout is fairly good too. Faucet or click on for a direct hyperlink and a walkthrough of find out how to promote on Decluttr.
For native promoting, skip the yard sale and listing your stuff shortly on OfferUp. The app is free to make use of, and you may message others, so that you need not give your cellphone quantity or electronic mail tackle. If you wish to lengthen your vary, OfferUp enables you to promote nationwide. For a neighborhood sale, cash adjustments arms in individual. For items which are shipped, funds are made by means of the app.
Faucet or click on for obtain hyperlinks for OfferUp, together with 5 different Craigslist alternate options.
6. Conceal your electronic mail tackle
Among the finest methods to cease the fixed circulate of electronic mail spam is to not use your major electronic mail tackle for purchasing on-line, newsletters, and requesting data.
A hidden trick when utilizing Gmail is to arrange distinctive electronic mail addresses everytime you want one. Simply use your major Gmail electronic mail tackle and put a plus signal after your identify and add a phrase the place you’re signing up. Say your electronic mail tackle is bob@gmail.com. Once you’re signing up for my free electronic mail publication, you’ll be able to create an immediate electronic mail tackle that’s bob+komandonewsletters@gmail.com.
Yahoo will allow you to create a disposable tackle in your settings.
Utilizing Apple’s iCloud, you’ll be able to have three completely different electronic mail addresses. However in the event you pay for iCloud, you’ll be able to cover your electronic mail wherever you need.
7. Get all of your electronic mail delivered in a single place
Talking of electronic mail, yours is probably going unfold throughout a number of gadgets. Once you ship, obtain, or delete an electronic mail on one system, it’s vital to maintain that workflow constant throughout others as properly. That approach, you do not miss essential messages or confuse others.
To arrange syncing on all of your gadgets, go to your Gmail web site in your desktop and click on:
- Click on the gear icon and click on Settings.
- Choose Forwarding and POP/IMAP tab.
- Underneath IMAP entry, Allow Pop for all mail, Allow IMAP.
- Scroll down and choose Save Adjustments.
You will discover a hyperlink for configuring mail retrieval by means of different platforms in that very same menu. That is essential when making an attempt to entry your account by means of third events like Thunderbird or the native Mail app on an iPhone. It is a lot simpler to arrange utilizing the official Gmail app.
In case you use Microsoft Outlook at work, and the mailbox you wish to sync is in your firm’s Change server, it’s finest to take the gadgets to your IT division. They’ll give you the area identify and different data you might want to arrange the mailbox on different gadgets.
Inbox feeling cluttered? Listed below are 5 must-do cleanups on your electronic mail inbox, community, and devices.
Bonus Tip: How advertisers acquire your knowledge and goal you with adverts
Male, 38 years outdated, married, two youngsters below 5, watched a YouTube video about garden care, visited a house enchancment retailer within the final 10 days, listened to a podcast about lawns, earns $68,000 a yr in a administration place, and lives in a sure zip code. That is how particular promoting could be as we speak. On this episode, I sit down with promoting CTO Premesh Purayil from Freestar to be taught the way it works and find out how to opt-out of the info monitoring.
Take a look at my podcast “Kim Komando Explains” on Apple, Google Podcasts, Spotify, or your favourite podcast participant.
Take heed to the podcast right here or wherever you get your podcasts. Simply seek for my final identify, “Komando.”
What digital life-style questions do you’ve? Name Kim’s nationwide radio present and faucet or click on right here to seek out it in your native radio station. You’ll be able to hearken to or watch The Kim Komando Present in your cellphone, pill, tv, or pc. Or faucet or click on right here for Kim’s free podcasts.
Copyright 2022, WestStar Multimedia Leisure. All rights reserved. By clicking the purchasing hyperlinks, you’re supporting my analysis. As an Amazon Affiliate, I earn a small fee from qualifying purchases. I solely advocate merchandise I consider in.
Find out about all the most recent expertise on The Kim Komando Present, the nation’s largest weekend radio speak present. Kim takes calls and dispenses recommendation on as we speak’s digital life-style, from smartphones and tablets to on-line privateness and knowledge hacks. For her day by day ideas, free newsletters, and extra, go to her web site at Komando.com.

Technology
How to know if your computer got hacked, what to do next

Have you ever had that sinking feeling that something’s not quite right with your computer? Maybe it’s running slower than usual or there are new icons on your desktop that you don’t recognize. Well, you might not be just imagining things; you could have been hacked.
While the first reaction may be to panic, the best possible first step if you think you’ve been hacked is to disconnect your computer from the internet and take a deep breath. If you’ve got antivirus software already installed, run the scan immediately. But don’t worry just yet. Before you start fretting about cyberthieves and lost data, let’s take a moment to walk through some crucial steps together. From running a trusty antivirus scan to the nitty-gritty of browser settings and remote access – this is your go-to guide for outsmarting those pesky hackers.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
A woman grabbing her computer in frustration (Kurt “CyberGuy” Knutsson)
Were you hacked?
1. Run antivirus software ASAP
When you’re running any antivirus scans or troubleshooting, start from the actual antivirus software program. Don’t follow pop-ups or notifications. If there is indeed a compromise, it should show up on the dashboard of the antivirus software program.
Preventative:
- Keep your antivirus software updated. Hackers are coming up with new viruses often, so if you are up to date, you’re less likely to be compromised. Or the virus is more likely to get caught.
- Be familiar with your antivirus software notifications and alerts, so if you ever get a pop-up or notification, you’ll be more apt to notice fake ones.
- Write down the contact information of the antivirus software you’ve installed and have it near the computer.
If you feel pretty confident that you’ve unfortunately been hacked, but your antivirus scan comes up empty, take a break and call customer service of antivirus software directly. Do not follow links to have a rep call you. Use the number you’ve written down, and call them directly so you know you’re not being duped.
If you don’t have antivirus software installed, make sure to install one and do a computer scan. You can find our top recommendations here.
ASK ANY TECH QUESTION AND GET KURT’S FREE CYBERGUY REPORT NEWSLETTER HERE

A man typing on keyboard (Kurt “CyberGuy” Knutsson)
HOW TO RECOVER A HACKED FACEBOOK ACCOUNT
2. Reformat or reset to factory settings
Sometimes a virus or other nefarious entities have overrun the computer so badly that you might need to simply reformat or reset it to factory settings. If you’ve uninstalled or deleted suspicious programs or applications only to have them reload upon restarting your computer, you may simply need to start from scratch. This is why it is crucial to have recent backups of your data. Our article, “How to securely get rid of your old PC or Mac,” outlines how to reset to factory settings or reformat your computer.
EXPERT TIPS, LEGIT REVIEWS. GET THE FREE CYBERGUY REPORT NEWSLETTER
3. Delete settings or extensions on browsers or uninstall and reinstall browsers completely
There have been many times I have gone to help my mom with her online accounts, only to be inundated with pop-ups, redirects or random links on her browser bar or menu. It turned out that she had either accidentally downloaded extensions that embedded themselves in the browser or, worse, changed the browser setting to open a spammy website as her main search engine or landing page. You can go to settings or preferences and delete extensions you do not recognize. But if these settings or extensions keep reappearing after deleting and restarting the browser, it is likely a bigger problem. Then, uninstall the browser and see if you can reinstall it. If that brings up the same settings again, then it could be a much more invasive virus or malware that needs to be addressed with an antivirus scan or assistance from a professional.
HOW TO OUTSMART CRIMINAL HACKERS BY LOCKING THEM OUT OF YOUR DIGITAL ACCOUNTS
4. Turn off or restrict remote access
While it is harder for hackers to access your computer if it is completely turned off, if you have allowed remote access, a hacker just needs your computer to be hooked up to a network or the internet in order to take over your device and turn it on.
To prevent remote access to your PC:
- Click the Windows Start button
- Input Remote Desktop settings in the search bar
- In the Remote Desktop settings, ensure that the slider under “Enable Remote Desktop” is set to Off.
- Review your current processes in Task Manager (Ctrl+Alt+Del) for any unusual or suspicious activities
To prevent remote access on Macs:
- Click the Apple logo icon in the top left corner.
- Click System Settings
- Tap General
- Click the Sharing icon
- Scroll down and uncheck the boxes next to Remote Login and Remote Management to prevent unauthorized remote access.

A woman on her laptop (Kurt “CyberGuy” Knutsson)
HOW HACKERS CAN CRAFT AN ATTACK FROM YOUR SOCIAL MEDIA PROFILE
5. Review your activity monitor on your computer and network traffic patterns
Periodically, checking your computer’s activity monitor to check which programs are running and what is using up the most bandwidth is a healthy practice. It will teach you to spot any programs or traffic that is unusual or if someone else is connecting to your computer remotely.
To review this activity on your PC:
- Go to Control Panel
- Click Administrative Tools
- In Event viewer, look for the events that are related to startup and shutdown. Any shutdown will be listed there and which program or user-initiated that startup or shutdown. This way, you can see if these actions are that of a virus or an update process.
To review this activity on your Mac:
- Go to the menu bar on the top left when you first log on to your account.
- Select Go
- In the drop-down menu, select Utilities
- When a menu pops up, one of the first options should be Activity Monitor.
Or:
- Go to your Applications folder on your dock (usually located on the bottom or right-hand side of the screen)
- Go to Utilities folder
- Select Activity Monitor

A man putting in his username and password on tablet (Kurt “CyberGuy” Knutsson)
Top 3 preventative measures to not get hacked
1. Turn on 2-factor authentication
While it may seem like a pain to enter a code received via email or text each time you sign in, this extra step is crucial for security. By activating two-factor authentication, you create a barrier against unauthorized access. Even if a hacker discovers your email or username, they won’t get far without the unique code.
Each login attempt triggers a notification, alerting you to potential threats. Repeated failed attempts will secure your account by either locking it or sending you an alert. In the event of suspicious activity, you can swiftly use a trusted device to reset your password and inform the service provider. It’s a small price to pay for significant protection against cyberthreats.

A man backing up his computer (Kurt “CyberGuy” Knutsson)
2. Have strong antivirus software
The best way to protect yourself from clicking malicious links that install malware in an attempt to get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams. Plus, think of it like having a digital bodyguard – always on the lookout, always ready to defend you from cyberthreats. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
3. Configure your email settings
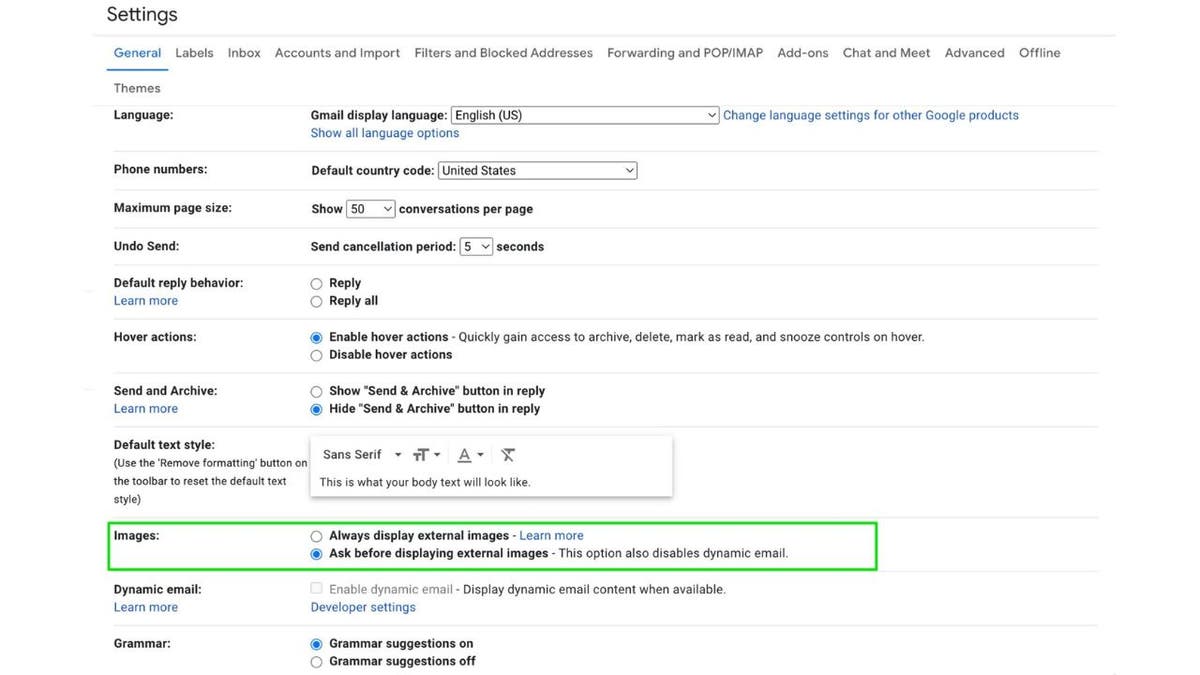
Configure email settings to not automatically images or attachments (Kurt “CyberGuy” Knutsson)
If you configure your email settings to not automatically load content such as images or attachments, then it is harder for viruses or other malware to be automatically downloaded or accidentally opened. If you also have emails received first in rich text format, you can choose which emails load fully with images once you realize it is from a trusted source.
Gmail desktop:
- Click the settings gear icon
- Choose See all settings
- Under the General tab, scroll to the Images section.
- Select Ask before displaying external images
- Scroll to the bottom of the page and click Save Changes
Gmail mobile:
- Tap the hamburger menu (3 horizontal lines)
- Select Settings
- Choose the account you want to manage
- Scroll to the Images section and select Ask before displaying external images.
Apple mail:
- First, click on Mail in your dock at the bottom of your screen
- Then click on Mail in the upper left of your screen
- Click Settings
- Go to the Viewing tab
- Uncheck Load remote content in messages
Outlook desktop (PC):
- Click File
- Choose Options
- Select Trust Center
- Click Trust Center Settings
- Under Automatic Download, check the option that says Don’t download pictures automatically in standard HTML email messages or RSS items.
Outlook desktop (Mac):
- Open Outlook
- Click Preferences
- Under Email select Reading
- Choose Security
- Select Never to prevent image downloads
Yahoo Mail desktop:
- Click Settings.
- Choose More Settings.
- Click Viewing email.
- Under Show images in messages, select Ask before showing external images.
Start Mail desktop:
Please note that the exact wording of the menu items and options can vary based on the version of Start Mail you are using.
- Open Start Mail
- Click on the Settings icon
- Navigate to the Email section
- Look for the Images or Privacy settings
- Choose the option to Ask before displaying external images or a similar setting that controls the automatic downloading of pictures.
These steps should help enhance your email security by giving you control over which images are displayed, thereby reducing the risk of malware being automatically downloaded or opened. Always ensure your email application is updated to the latest version for the best security practices.
Looking for private and secure email solutions? See Best Private and Secure Email Providers 2024
QUICK TIPS. EXPERT INSIGHTS. CLICK TO GET THE FREE CYBERGUY REPORT NEWSLETTER
Data recovery: Protecting your information against loss
This may not seem relevant to an article about hacking, but having your data off your computer and safely on an external hard drive or the cloud will give you more options if you think you’ve been hacked. If you need help deciding what type of data backup would be best for you, please take a look at these articles:
If a hack is bad enough, sometimes a complete wipe of your system is the only way to salvage your computer. If you have a safe copy of your data, while it might be inconvenient, you will not lose all your data. Also, if you keep more sensitive data off your more frequently used computer, then your data is less likely to be compromised if you get hacked.
Kurt’s key takeaways
At the end of the day, being hacked is a massive inconvenience and can potentially lead to data loss or theft. But don’t lose hope. There are steps you can take to outsmart those pesky hackers and keep your devices secure. The key is staying vigilant and taking preventative measures like using strong antivirus software, enabling two-factor authentication and regularly backing up your data. That way, if you do get hacked, you’ll have a recent backup to rely on and can simply wipe your device clean without losing everything.
It’s also crucial to keep an eye out for any suspicious activity on your computer or network. If something seems off, don’t hesitate to run a full antivirus scan and review your activity monitor for any unauthorized access or programs running in the background. Remember, hackers are always coming up with new tricks, so it’s an ongoing battle to stay one step ahead. But by following the tips outlined here, you’ll be well on your way to keeping your digital life secure and hack-free. Stay vigilant, my friends.
Can you share a personal story where being proactive about computer security paid off or, conversely, where neglecting it led to issues? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on Facebook, YouTube and Instagram.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Apple’s next AirTag could arrive in 2025
/cdn.vox-cdn.com/uploads/chorus_asset/file/22461385/vpavic_4547_20210421_0067.jpg)
You may not have even thought about replacing your AirTag yet, but Bloomberg reports that Apple is working on a new one that could arrive in mid-2025. The new AirTag will reportedly feature an updated chip with better location tracking — an improvement it might need as competition among tracking devices ramps up.
By the time Apple rolls out its refreshed AirTag, the Bluetooth tracking landscape will look a lot different on both Android and iOS. Last month, Google revealed its new Find My Device network, which lets users locate their phones using signals from nearby Android devices. Even Life360, the safety service company that owns Tile, is creating its own location-tracking network that uses satellites to locate its Bluetooth tags.
In last week’s iOS 17.5 update, Apple finally started letting iPhones show unwanted tracking alerts for third-party Bluetooth tags. If an unknown AirTag or other third-party tracker is found with an iPhone user, they’ll get an alert and can play a sound to locate it. The feature is part of an industry specification created to prevent stalking across iPhones and Android devices. Several companies that make Bluetooth tracking devices, including Chipolo, Pebblebee, and Eufy are on board with the new standard.
Technology
How to connect your AirPods to your iPhone, iPad the easy way

While the sonic quality of the AirPods certainly works across most devices with a Bluetooth connection, the real magic and a plethora of useful features really shine when you connect AirPods with other Apple devices. If you use the same Apple ID across all your Apple devices, you can really take advantage of the seamless auto-connect features.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
A woman listening to her AirPods (Kurt “CyberGuy” Knutsson)
ASK ANY TECH QUESTION AND GET KURT’S FREE CYBERGUY REPORT NEWSLETTER HERE
How to connect your AirPods to your iPhone
Before you start, make sure you’ve installed the latest version of iOS on your iPhone and be sure your AirPods are charged and in their case. If you’ve already connected your AirPods to your iPhone, it should connect automatically if you are signed in with the same Apple ID you used to sign onto your Mac. If not, here’s how to connect them to your iPhone.
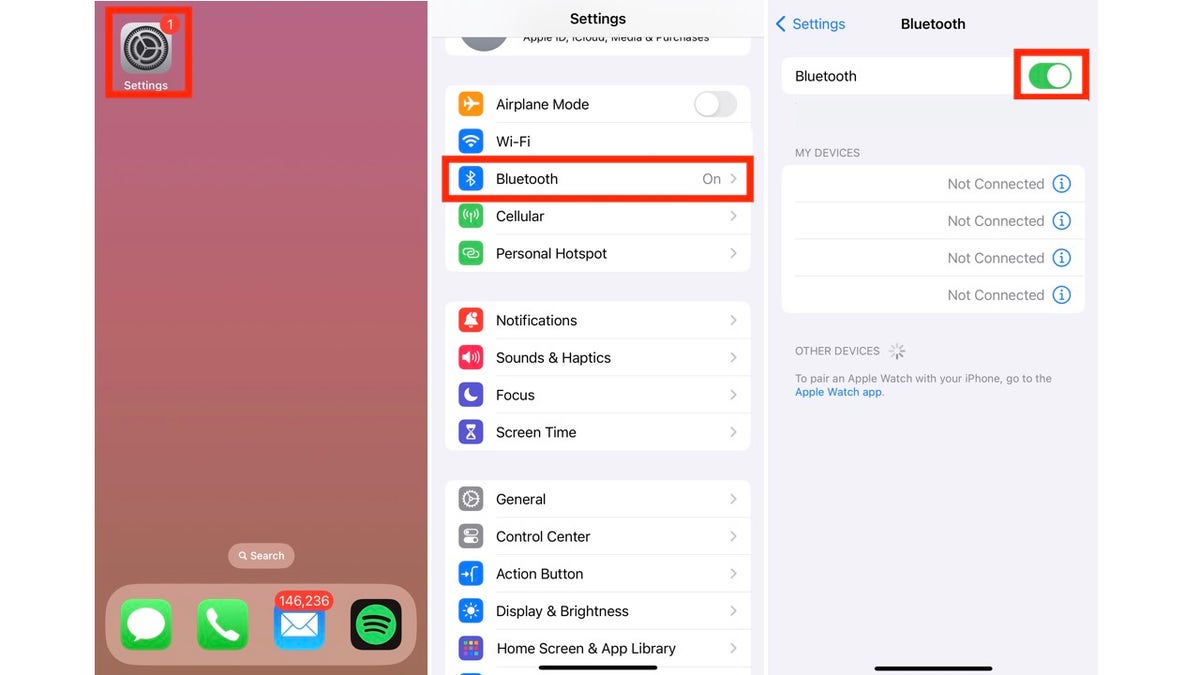
- Unlock your iPhone and go to Settings
- Scroll down and tap Bluetooth, then turn on Bluetooth (if it isn’t already on)
- The toggle next to Bluetooth should be green, not grayed out.
Steps to connect your AirPods to your iPhone (Kurt “CyberGuy” Knutsson)
- Now, grab your AirPods case with the AirPods inside, then hold it next to your iPhone with the case top open.

Steps to connect your AirPods to your iPhone (Kurt “CyberGuy” Knutsson)
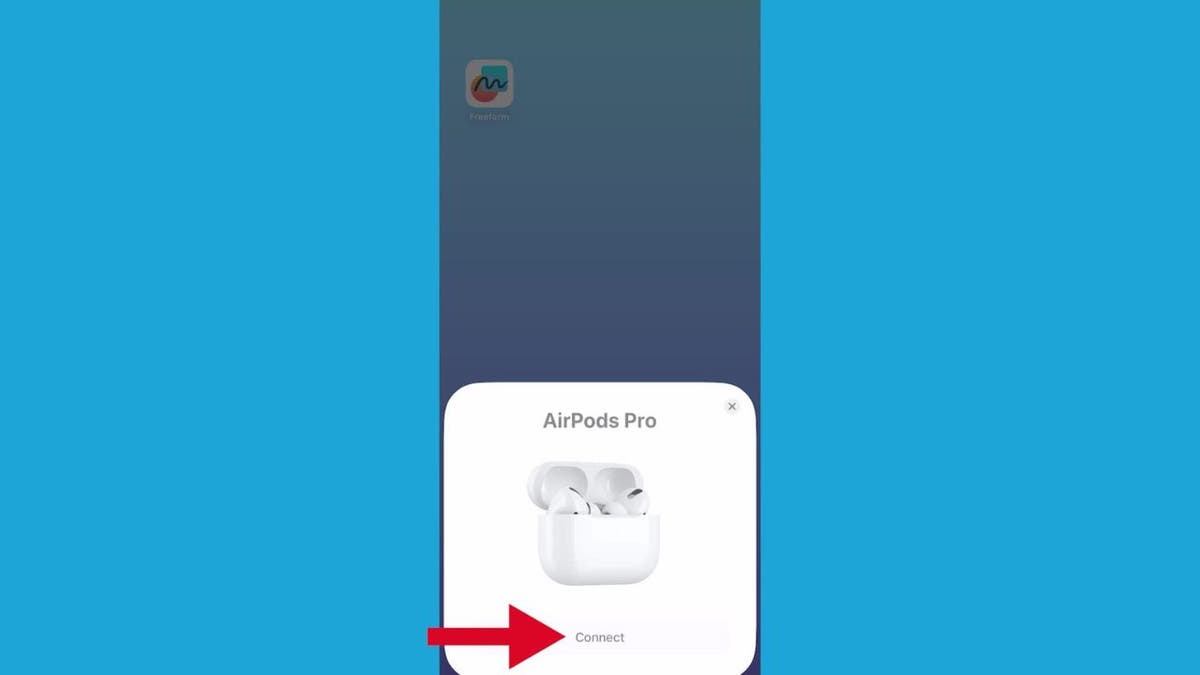
- At this point, a setup animation will show up on your iPhone screen.
- Tap Connect and you should be ready to listen.
Steps to connect your AirPods to your iPhone (Kurt “CyberGuy” Knutsson)
MORE: 8 INCREDIBLY USEFUL THINGS YOU CAN DO WITH AIRPODS
How to connect your AirPods to your iPad
Before you start, make sure you’ve installed the latest version of iOS on your iPhone and be sure your AirPods are charged and in their case. If you’ve connected your AirPods to your iPad already, it should connect automatically if you are signed in with the same Apple ID you used to sign onto your Mac. If not, here’s how to connect them to your iPad.
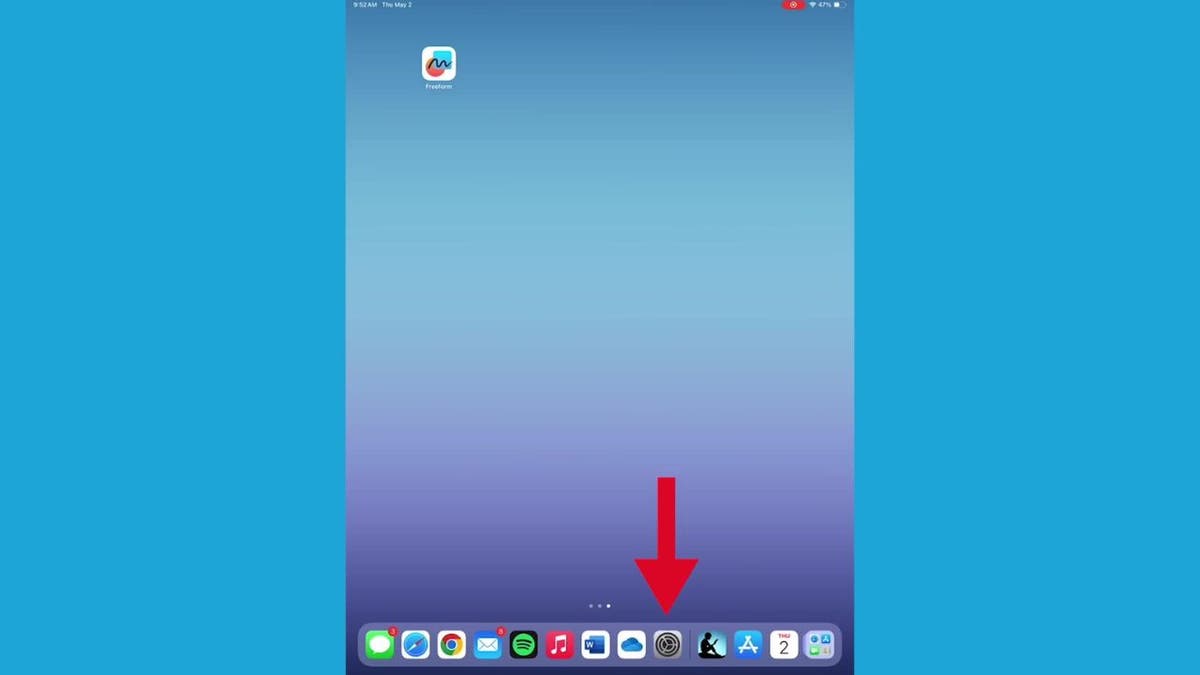
- Open up your iPad and go to Settings.
Steps to connect your AirPods to your iPad (Kurt “CyberGuy” Knutsson)
- From Settings, scroll down and tap Bluetooth.
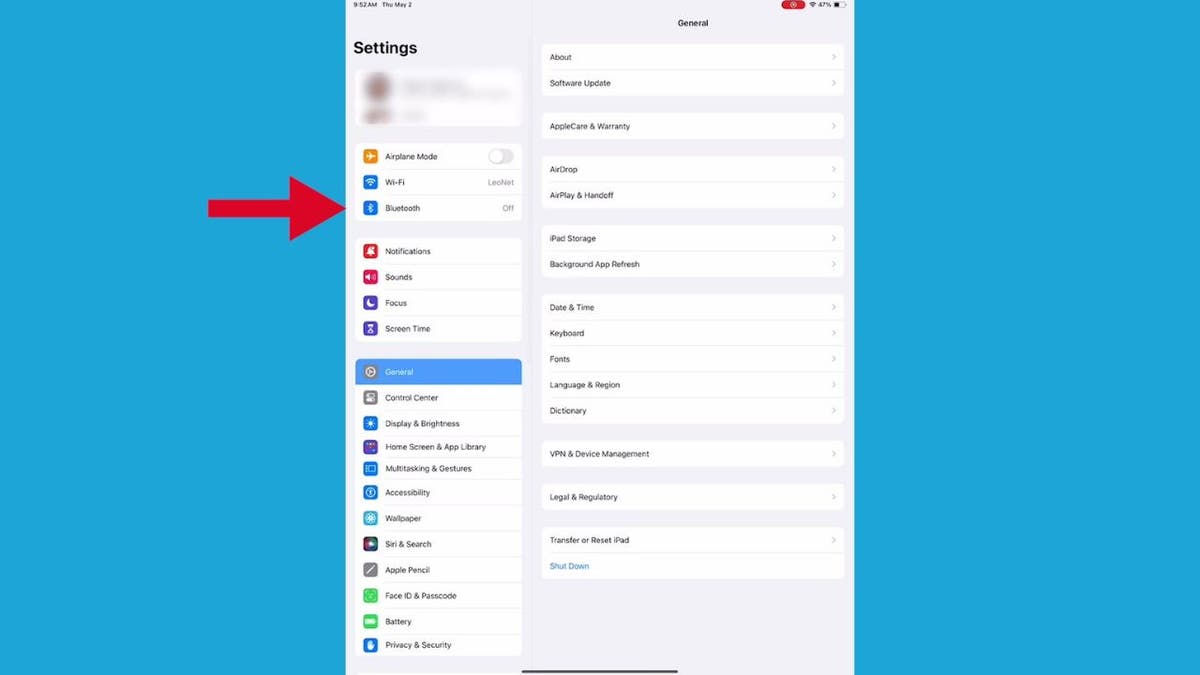
Steps to connect your AirPods to your iPad (Kurt “CyberGuy” Knutsson)
- Then, tap the button on the right once so that it turns green.
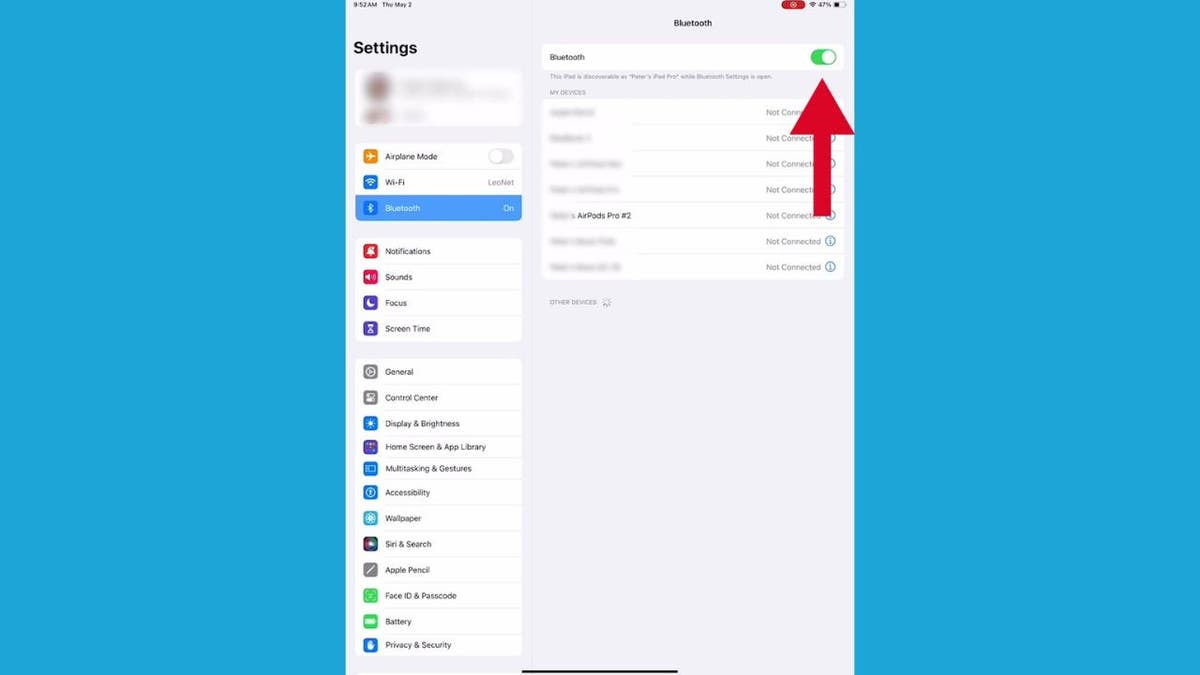
Steps to connect your AirPods to your iPad (Kurt “CyberGuy” Knutsson)
- Keep your iPad open to this screen and take out your AirPods.

Steps to connect your AirPods to your iPad (Kurt “CyberGuy” Knutsson)
- From here, a setup animation will appear on the iPad. Tap Connect.
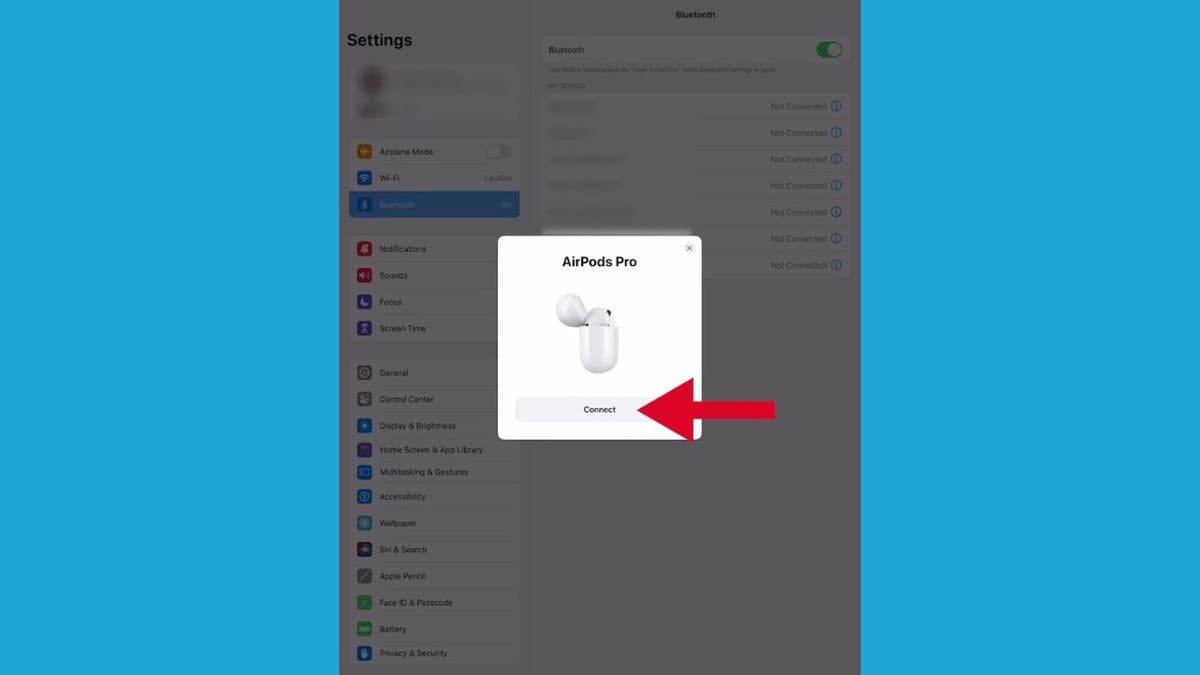
Steps to connect your AirPods to your iPad (Kurt “CyberGuy” Knutsson)
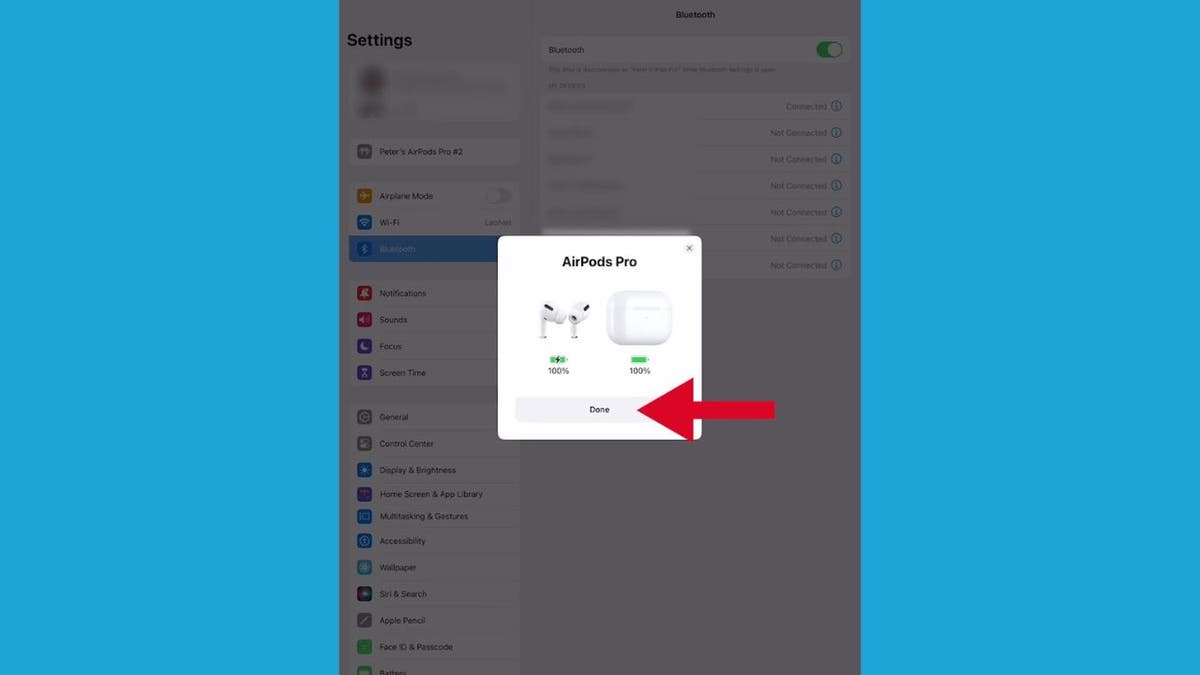
Steps to connect your AirPods to your iPad (Kurt “CyberGuy” Knutsson)
- Your AirPods should appear under the list of available devices in your Bluetooth settings on the iPad. Now tap your AirPods, and there you go.
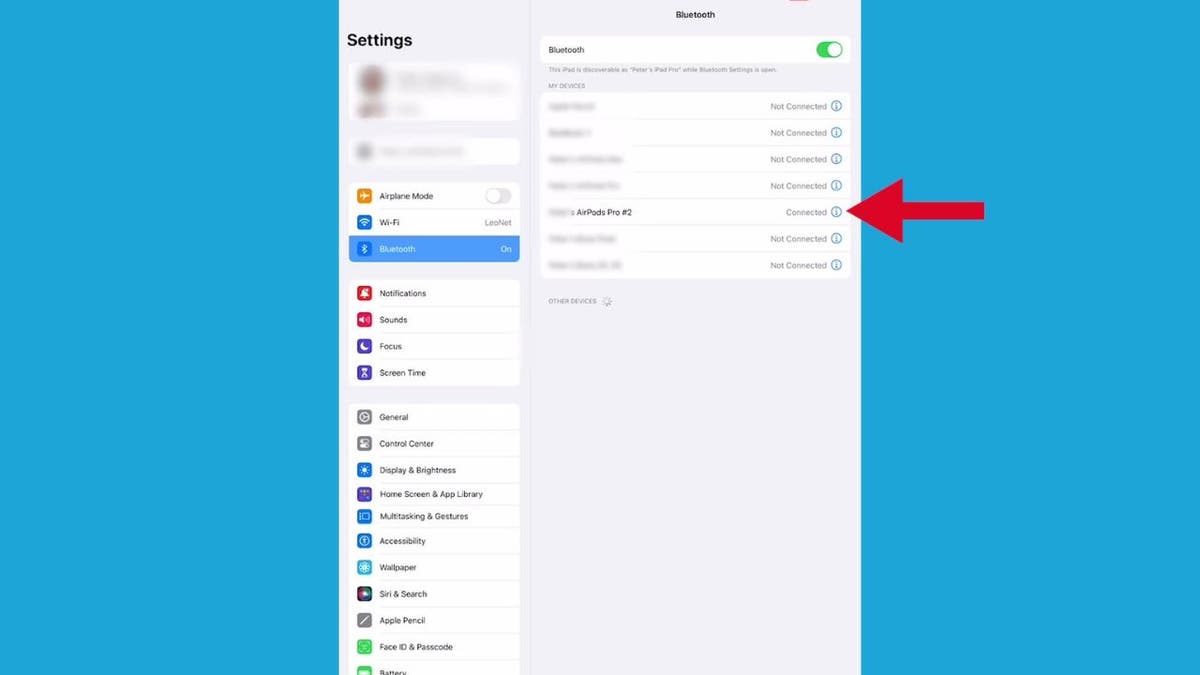
Steps to connect your AirPods to your iPad (Kurt “CyberGuy” Knutsson)
Kurt’s key takeaways
In a nutshell, AirPods are popular because they’ve got great performance, reliability and are easy to use, especially if you’ve already got other Apple products in your life. They just get you, you know? They move between your iPad to your iPhone without a hitch – it’s like they’ve got a mind of their own. And setting them up is super simple. It’s like tap, tap, boom – you’re connected.
In what ways do you think the AirPods’ features could be further enhanced when paired with Apple devices? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on Facebook, YouTube and Instagram.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
-

 News1 week ago
News1 week agoSkeletal remains found almost 40 years ago identified as woman who disappeared in 1968
-

 World1 week ago
World1 week agoIndia Lok Sabha election 2024 Phase 4: Who votes and what’s at stake?
-

 Movie Reviews1 week ago
Movie Reviews1 week ago“Kingdom of the Planet of the Apes”: Disney's New Kingdom is Far From Magical (Movie Review)
-

 World1 week ago
World1 week agoUkraine’s military chief admits ‘difficult situation’ in Kharkiv region
-

 Politics1 week ago
Politics1 week agoTales from the trail: The blue states Trump eyes to turn red in November
-

 World1 week ago
World1 week agoBorrell: Spain, Ireland and others could recognise Palestine on 21 May
-

 World1 week ago
World1 week agoCatalans vote in crucial regional election for the separatist movement
-

 Politics1 week ago
Politics1 week agoNorth Dakota gov, former presidential candidate Doug Burgum front and center at Trump New Jersey rally













