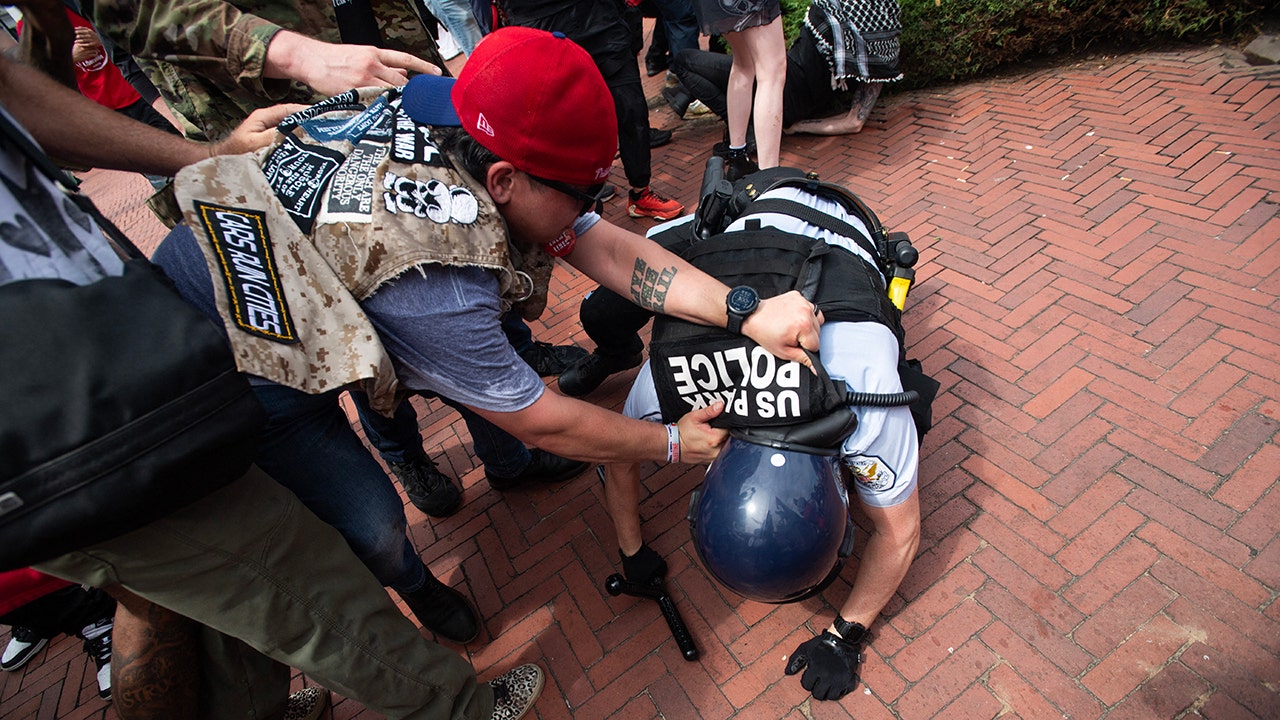Patrick Byrne, who has funded efforts to undermine the results of the 2020 election, said in an online forum Thursday that law enforcement would face “a piano wire and a blowtorch” if they did not drop a case against an ally.
Washington
Passing bills, bills, bills: Highlights from Week 5 in Washington state Legislature

FILE – The House chambers are viewed with most members attending remotely on the first day of the legislative session, Monday, Jan. 10, 2022, at the Capitol in Olympia, Wash.
Ted S. Warren / AP
The week started off with more cutoff deadlines looming — and more notable pieces of legislation were left behind Monday, before Washington state lawmakers in both the House and Senate chambers hit the floor for the rest of the week.
Policies on the move
In the House, lawmakers approved House Bill 1579, which would create a new prosecution office in the state with the authority to charge police for deadly use of force.
Legislation that could change the way cities approach their general elections, House Bill 1932, passed after lengthy debate on the proposal. Right now, cities and towns elect local officials in odd-numbered years, but the bill would allow local governments to switch their general elections to even-numbered years, when voter turnout is higher.
House lawmakers were split on the idea. Critics worry voters in cities that might make the change will be more focused on national campaigns and become fatigued with lengthy ballots.
But supporters say the change could spur civic engagement, and prompt more voters to weigh in on local issues. Only about 36% of Washington voters across the state filled out their ballots for last year’s general election — compared to a much-higher turnout of 63% in 2022.
Meanwhile, the Senate sent a few notable measures across the rotunda too.
First cutoff deadline, rent bill complications: A quick look at week 4 in the Washington Legislature
Senators signed off on Senate Bill 6009, which bans police from hog-tying people in their custody.
They also passed Senate Bill 6298, which would make members of the clergy mandatory reporters of child abuse or neglect. A similar version stalled out last year over disagreements on whether or not clergy should be required to report abuse they hear about in confession, and this year’s version attempts to strike a balance between concerns on either side.
The Senate also approved a bill that would create new safety rules for workers at strip clubs and other adult entertainment establishments, Senate Bill 6105. Interestingly, the chamber added language into the bill requiring the state’s Liquor and Cannabis Board to repeal its lewd conduct rules, in response to recent citations at gay bars in Seattle.
Lawmakers also spent a lot of time debating a controversial bill about regulating hospital mergers, Senate Bill 5241, before it passed 28 to 21. The bill would require the Attorney General’s office to oversee proposed mergers and ensure that they don’t limit peoples’ access to end-of-life, reproductive, or gender-affirming health care.
And Senate Bill 5444, which would ban the open carry of guns in some zoos, libraries and transit centers, also gained Senate approval along party lines.
Natural gas, opioids and DUIs: Highlights from week 3 of Washington’s legislative session
Nearly all the bills passed off the floor this week now go to the opposite chamber for further consideration, but the first bill of the session to make it through both sides of the Legislature also gained final approval. House Bill 1964 aims to improve enforcement of the state’s fuel tax, and passed both chambers with broad bipartisan support.
And even though Seattle’s NFL team won’t be playing during this weekend’s Super Bowl, the Senate spent a few minutes praising former Seahawks Head Coach Pete Carroll Friday morning.
The Senate passed a resolution formally congratulating Carroll for his accomplishments across his career in the NFL — including leading the Seahawks to the franchise’s first Super Bowl win in 2014. It was announced in January that Carroll would no longer be head coach after 14 years in the role. Carroll wasn’t in attendance, but Sen. Ann Rivers (R-La Center) wore a Seahawks jersey on the floor as she spoke on the resolution.
What fizzled
Republicans held a press conference Thursday condemning a proposal to raise the 1% cap on annual hikes to local property taxes. The following day, Democrats made clear that Senate Bill 5770 wouldn’t be moving forward this session. The bill would have allowed local governments to raise the amount of money they make from property taxes.
The bill’s sponsor, Sen. Jamie Pedersen (D-Seattle) told the Washington State Standard that the decision to leave the bill behind this year was in part due to “the voter mood” as several initiatives, mainly targeting taxation, are almost certain to go to ballots in November.
A proposal pitched in response to the frustration over fuel costs, Senate Bill 6052, seems to have stalled.
The measure was a priority for Gov. Jay Inslee — especially to help defend his signature Climate Commitment Act, as critics blame it for changing gas prices. The bill aimed to create more state oversight for gas companies and the way they set prices. But the bill didn’t get a hearing or a vote in the Senate Ways and Means Committee before Monday’s cutoff, with proponents of the bill attributing its demise to the policy’s complexity and financial cost.
AI, guns, and initiatives: highlights from Week 2 of Washington state’s 2024 legislative session
Another bill that would have expanded on lawmakers’ 2023 effort to provide more kids with free school meals also didn’t make it. This year’s bill, House Bill 2058, would have required any public school to offer kids free lunch and breakfast — but it also didn’t get a vote.
Lawmakers also didn’t take action on a solitary confinement reform bill, and advocates say with the lapse of House Bill 1087, the Legislature missed a critical moment to make some meaningful changes before a massive shift in leadership in the state next year.
Also of note, Rep. Spencer Hutchins (R-Gig Harbor) announced he won’t seek reelection later this year. Every member of the House of Representatives is up for reelection this fall, as well as about half of state Senators. Hutchins said in a statement announcing his decision that the demands of being a lawmaker have “taken a heavy toll” on his family and livelihood.
Lawmakers will spend more time on the floor at the beginning of next week — most bills have to make it out of their chamber of origin by Tuesday, Feb. 13, in order to keep moving forward this session. Next week lawmakers will also get a new look at the state’s revenue forecast and begin releasing their plans for changes to the state’s current two-year budget.

Washington
Trump ally who denies 2020 election results threatens law enforcement

The “Cyber Crisis: Saving Tina Peters” event was aimed at rallying support for the former clerk of Mesa County, Colo., who faces charges accusing her of tampering with election equipment three years ago. Peters has pleaded not guilty, and her case goes to trial next week.
Byrne called out law enforcement and prosecutors during the forum, saying they would face violence if they did not drop the case.
“If you have any brains at all, which I’m not sure they do, they should be throwing in the towel and just surrendering and dropping this case against Tina because those who don’t are going to end up facing a piano wire and a blowtorch before this is over if I have anything to do with it,” Byrne said. “So I know that’s probably another felony, but f— it — threatening them like that — but there we are.”
Byrne, who said he was participating in the event from Azerbaijan, accused law enforcement of committing treason and claimed he had been hacking Venezuela’s government for two years.
“I don’t care how many felonies I’ve committed, and I don’t care that I’m committing felonies by threatening you,” he said of law enforcement. “You folks do your job or when this is over, the folks who are part of this are going to be facing, you know, piano wire and blowtorches before this is over. So you start doing your job and stop worrying about me.”
Byrne said Friday that his comments were “obviously a metaphor.”
“Please be aware that my turns of phrase like that are metaphoric expressions,” he said by text message. “There’s been no one more committed to peaceful resolution of this than I.”
He said his views on peace do not extend to people like former ambassador Manuel Rocha, who pleaded guilty this year to serving as a secret agent for Cuba for decades. “The only exception to peaceful resolution will be for any who turn out of Cuba and Venezuela, such as ambassador Rocha,” Byrne said by text message.
Byrne noted it was 4 a.m. in Azerbaijan when he participated in the event on X, and he may not have spoken as carefully as he otherwise would.
Spokespeople for the Colorado attorney general’s office and Mesa County district attorney’s office did not immediately comment Friday.
Byrne’s comments come three-and-a-half months ahead of the presidential election, as scholars, law enforcement agencies and election administrators raise alarms about the risk of political violence. Election officials have faced an onslaught of threats and harassment since the 2020 election and the Jan. 6, 2021, attack on the U.S. Capitol by a mob chanting about Donald Trump’s false election claims.
Two weeks ago, Trump was injured during an assassination attempt that left one of his supporters dead at a rally in Butler, Pa. The violence fueled new warnings of the risk to public officials and ordinary Americans, regardless of their political views.
Before today’s combustible political environment, the phrases Byrne used might have prompted outreach by authorities to advise against using such language, said Paul Charlton, a former U.S. attorney under President George W. Bush. These days, state and federal officials tend to take such talk more seriously. Byrne’s language, he said, “sounds not only like a threat but a confession and an acknowledgment that it could be a felony to make such a threat.”
Words alone can be sufficient to prosecute threats against public officials if authorities can show proof of intent to do harm, he said.
“That is an instance in which, in my mind, it is very much worth law enforcement’s attention,” Charlton said.
Byrne’s repeated references to the Peters trial — and the prosecutors involved in it — are important aspects of his overall comments, said Carol Lam, a former U.S. attorney for the Southern District of California who was also appointed by Bush.
“Because he references a specific trial and he’s talking about the people who are bringing the case, that should be very troubling to law enforcement,” she said. Even if he said he was speaking metaphorically, she added, “What does that matter if someone went out and bought piano wire at his suggestion?”
Two hours after The Washington Post contacted Byrne, he posted a statement on X that reiterated what he told a reporter about meaning his comments metaphorically. He said he wanted people to remain peaceful, but added information would come out that would “test our ability to remain peaceful and my ability to contribute to that cause.”
Byrne used this week’s online forum to argue for dropping the charges against Peters, who is accused of participating in a scheme to allow a purported data expert to secretly copy files from Dominion Voting Systems equipment in 2021. She faces seven felonies and three misdemeanors in a case that is scheduled to go to trial on Wednesday.
He has long championed Peters and others who have questioned the results of the 2020 election. Four days after members of the electoral college voted to give Biden a victory in December 2020, Byrne joined other Trump allies in the Oval Office to argue Trump could use the National Guard to seize voting machines. Also in the meeting were Trump-aligned attorneys Sidney Powell and Rudy Giuliani and former national security adviser Michael Flynn.
In the years since, Byrne has used his fortune and his nonprofit America Project to bankroll efforts meant to uncover problems with how elections are run, including a partisan review of the 2020 election in Arizona. Byrne and the America Project have helped fund groups like We the People Ariz. Alliance, an Arizona-based political action committee whose co-founder in March said she would “lynch” a Republican official who helps oversee elections in the state’s largest county. She later said her comment was a joke.
Courts and independent agencies have found no evidence of widespread election fraud.
Byrne led Overstock for two decades. He resigned in 2019 after it came to light that he had been romantically involved with Maria Butina, a Russian gun activist who pleaded guilty in 2018 to conspiring with a Russian official to infiltrate conservative politics in the United States. She was deported after serving a 15-month prison sentence. Byrne published a memoir this year that included a preface by Butina.
Dominion, the voting machine company, filed a $1.6 billion defamation lawsuit against Byrne in 2021. The case is ongoing. Dominion won settlements of $787.5 million with Fox News and $243 million with Newsmax and is seeking $1 billion or more from Giuliani, Powell and MyPillow CEO Mike Lindell.
Spencer S. Hsu and Rachel Weiner contributed to this report.
Washington
Video. Protesters rally in Washington during Biden's meeting with Netanyahu

Updated:
Gaza war protesters took to the streets outside of the White House in Washington DC, where President Joe Biden met with Israeli Prime Minister Benjamin Netanyahu on Thursday.
Gaza war protesters took to the streets outside of the White House in Washington DC, where President Joe Biden met with Israeli Prime Minister Benjamin Netanyahu on Thursday.
Chanting “Arrest Netanyahu,” the protestors brought in an effigy of the Israeli leader wearing an orange jumpsuit with blood on its hands.
A label on the jumpsuit read: “Wanted for crimes against humanity.”
Protesters poured red liquid from jugs onto the street across from nearby Lafayette Park. A speaker said it “symbolised the blood of the Palestinians.” Holding up blood smeared hands, they yelled: “Shame!” and chanted: “You are stealing Gaza’s blood!”
A small number of counter-protesters wore Israeli flags around their shoulders.
Washington
Barack and Michelle Obama endorse Kamala Harris for president

“We called to say Michelle and I couldn’t be prouder to endorse you and to do everything we can to get you through this election and into the Oval Office,” the former president says to Harris.
Michelle Obama adds, “I can’t have this phone call without saying to my girl Kamala: I am proud of you. This is going to be historic.”
In a separate statement, the Obamas pledged to “do everything we can” to elect Harris and called on their legions of supporters to join the effort.
They praised Harris’s record of accomplishments, listing each of her previous roles in what could be interpreted as a rejoinder to Republicans who have labeled her a “DEI hire” — a reference to “diversity, equity and inclusion” initiatives often used derisively to suggest that Harris only reached the upper echelon of American politics because of her race and gender.
“But Kamala has more than a résumé. She has the vision, the character, and the strength that this critical moment demands,” they wrote. “There is no doubt in our mind that Kamala Harris has exactly what it takes to win this election and deliver for the American people. At a time when the stakes have never been higher, she gives us all reason to hope.”
Their call with Harris took place on Wednesday. Barack Obama said the Democrats would be “underdogs” but pledged to work hard for her election.
“Bottom line is, we are ready to get to work,” he said during the call, according to a transcript. “We are telling everybody to kick off those bedroom slippers and get off the couch and start knocking on doors and making phone calls.”
Many Republicans seized on the fact that Obama did not mention or endorse Harris in his initial statement responding to Biden’s abrupt exit from the race Sunday.
“We will be navigating uncharted waters in the days ahead,” he said in that statement. “But I have extraordinary confidence that the leaders of our party will be able to create a process from which an outstanding nominee emerges.”
On Thursday, Donald Trump’s campaign seized on Obama’s lack of an endorsement to make the case that Harris’s path to the nomination was not a done deal. Steven Cheung, a campaign spokesman, said Trump would not agree to debate Harris until she was officially the Democratic nominee, suggesting without evidence that Obama and other top Democrats were considering backing a different candidate.
“There is a strong sense by many in the Democrat Party — namely Barack Hussein Obama — that Kamala Harris is a Marxist fraud who cannot beat President Trump, and they are still holding out for someone ‘better,’” Cheung said in a statement Thursday evening. “Therefore, it would be inappropriate to schedule things with Harris because Democrats very well could still change their minds.”
The Obamas’ endorsement comes after Harris already secured enough pledges from delegates to become the likely nominee. Biden exited the race on Sunday and immediately endorsed Harris, who quickly coalesced much of the Democratic Party behind her bid.
Just before Biden dropped out of the race, Obama told allies that the president’s path to victory had greatly diminished and he thought the president needed to seriously consider the viability of his candidacy, according to multiple people briefed on his thinking, who spoke on the condition of anonymity to discuss confidential conversations. In those conversations, Obama emphasized he felt protective over Biden as a friend and was concerned about his legacy.
-

 World1 week ago
World1 week agoOne dead after car crashes into restaurant in Paris
-

 Midwest1 week ago
Midwest1 week agoMichigan rep posts video response to Stephen Colbert's joke about his RNC speech: 'Touché'
-

 News1 week ago
News1 week agoVideo: Young Republicans on Why Their Party Isn’t Reaching Gen Z (And What They Can Do About It)
-

 Movie Reviews1 week ago
Movie Reviews1 week agoMovie Review: A new generation drives into the storm in rousing ‘Twisters’
-

 News1 week ago
News1 week agoIn Milwaukee, Black Voters Struggle to Find a Home With Either Party
-
 Politics1 week ago
Politics1 week agoFox News Politics: The Call is Coming from Inside the House
-

 News1 week ago
News1 week agoVideo: J.D. Vance Accepts Vice-Presidential Nomination
-

 World1 week ago
World1 week agoTrump to take RNC stage for first speech since assassination attempt