Technology
Beware of a new Android threat targeting your photos and texts without even opening them

What is malware?
Kurt ‘CyberGuy’ Knutsson discusses how to protect yourself from malware and ransomware.
Another day, another malware threat is trying to get your data.
Well, brace yourself, because there’s a virus that’s been around for a while that’s out there that’s gotten even worse.
It’s called XLoader, and it’s after your photos and texts on your Android device. Yes, you heard that right.
Your precious memories and messages are in danger of being snatched by this malicious software.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS, AND EASY HOW-TO’S TO MAKE YOU SMARTER
Android phone. (Kurt “CyberGuy” Knutsson)
What is malware?
Malware is technically any software that’s designed to disrupt the system of its intended target. With malware, the person or entity behind the attack can gain access to your data, leak sensitive information, block you out and take control of other aspects of your privacy and security.
MORE: TIPS TO FOLLOW FROM ONE INCREDIBLY COSTLY CONVERSATION WITH CYBERCROOKS
What is the XLoader malware strain?
According to McAfee, the XLoader malware — also known as MoqHao — has been around since 2015, targeting Android users in the U.S., Europe and Asia. Once it’s on your device (which it’s gotten much better at doing), it’s able to run in the background, taking your sensitive data, whether it be photos, text messages, contact lists, hardware details and more.

Hacker typing on a laptop. (Kurt “CyberGuy” Knutsson )
MORE: BEWARE OF NEW ANDROID MALWARE HIDING IN POPULAR APPS
How does XLoader get onto your device?
One of the reasons XLoader is such a major threat is because, unlike its previous strains and other malware, it can get on your device that much easier than before. Generally, malware gets onto your device via a phishing scam. However, because people are more skeptical about opening or clicking on suspicious files or links — and because there are integrated apps that help warn you of these files — it’s more difficult for these traditional phishing scams to be effective, but XLoader has gotten clever.
First, you receive a text from an unknown sender
Like ordinary malware, XLoader often spreads through malicious links sent via text messages. This is a unique type of phishing scam known as “smishing.” However, scammers are aware that most people don’t click on texts from people they don’t know. So, another way they attempt to be successful at this is by first gaining access to a phone number that has your number in their contacts, and they target you that way. You won’t think twice when you receive a text from someone you know. Once it gets past this step, XLoader can get onto your Android device in two ways:
1: You click on the link which leads to downloading the APK file
Next, the unsuspecting victim would see a link in the text message. The link may look less suspicious than typical malware links because they are typically shortened and look less spammy and more legitimate, like a link that someone you know would send you.
A RANSOMWARE REALITY CHECK AS US IS A TOP TARGET OF ATTACKS
If you end up clicking on this link, it will direct you to download an Android APK file (standard file format for Android), which are files that are used to sideload apps outside the official Google Play Store. This method, therefore, bypasses Google’s security measures and increases the risk of malware infections. It can happen in a matter of seconds, and if you click “install,” then the XLoader malware will be on your phone before you know it.
Once the malicious APK is downloaded and installed, XLoader can launch on its own without any further action from the user, silently running in the background and performing its malicious activities.
2: You launch the app yourself, but fall for a Google Chrome decoy
If you decide you want to launch the app directly on your own, XLoader is already there waiting for you by impersonating Google Chrome. When you click “launch,” the XLoader malware displays a very familiar-looking Chrome pop-up that will first ask you to grant it permissions by clicking “allow” or “deny.” If you click “Allow” (thinking it’ll lead you to the “app”), you’ll be unknowingly giving it access to your SMS.
Afterward, it will even display a pop-up that says, “Choose Chrome to prevent spam,” giving you two options — your default SMS app or Chrome. Because these decoy pop-ups replicate Google’s style completely, it gives the user a false sense of security that it can be trusted.
Once it’s there, it can grab your photos, texts and other sensitive data on your Android, most of the time, without you even realizing it.
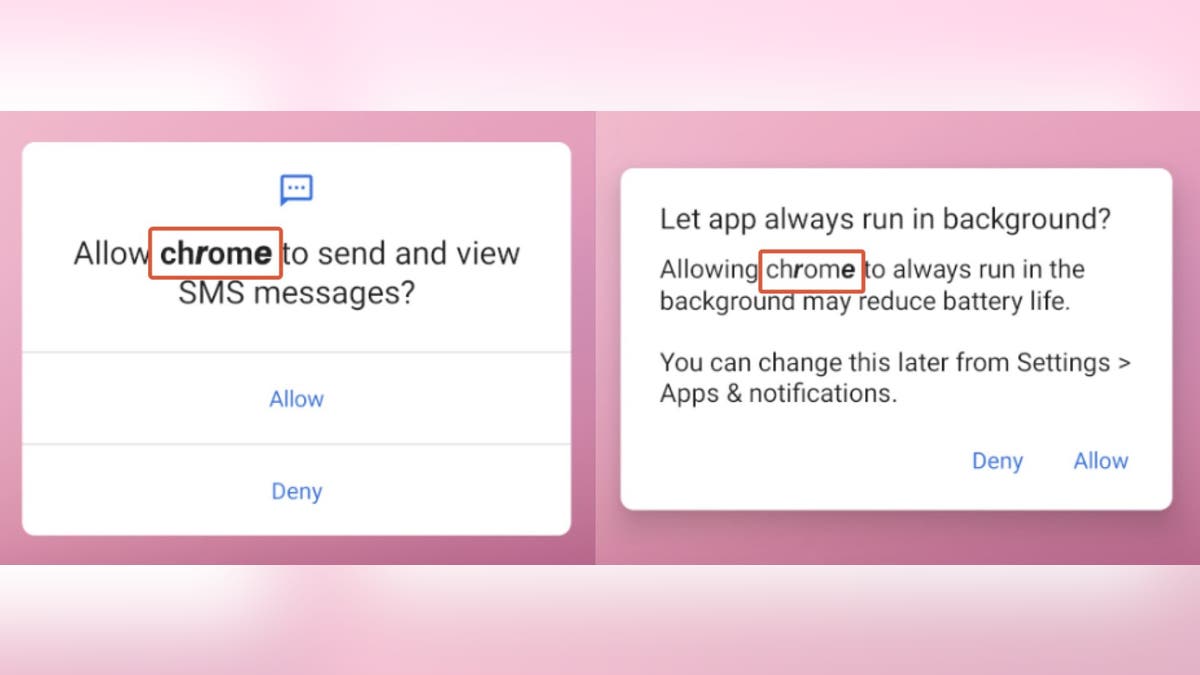
Google Chrome decoy. (McAfee)
6 ways to protect your Android from XLoader and other malware
Now that you know what XLoader is and how it gets onto your Android device, be sure not to click on any links in text messages that are unusual. If the text came from someone in your contacts, reach out to them directly (via phone call or messaging on another app) and confirm that they meant to send you it before clicking on it. Here are some other ways to protect yourself from XLoader and other malware attempts.
1. Avoid sideloading apps and shortened URLs: Refrain from sideloading apps (installing apps from unofficial sources) and clicking on shortened URLs in messages, as these are common vectors for malware distribution.
2. Be careful granting permissions: Exercise caution when granting permissions to apps. The question is whether an app truly needs access to certain device functions or data.
3. Limit the apps you have on your phone: Sometimes, having a lot of apps on your phone can make it easy for you to be exposed to malware. These apps can let in malicious code over time, and the more apps you have to keep track of and update, the more likely your Android will be vulnerable.
4. Only download reputable apps: Additionally, when you download apps, make sure they are from reliable and legitimate developers. Check reviews and do some research before just hitting “install.”
5. Don’t neglect software updates: Your phone has a way of keeping itself safe with software and security updates. Don’t forget to do them.
6. Have good antivirus software on all your devices: The best way to protect yourself from malware like this Xloader virus is to install antivirus protection on all your devices. Having antivirus software on your devices will make sure you are stopped from clicking on any potential malicious links that may install malware on your devices, allowing hackers to gain access to your personal information. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
Kurt’s key takeaways
Malware is, unfortunately, inevitable. As we become more educated about how to prevent these threats, the hackers creating them are always working on ways to outsmart us, while the malware itself becomes more sophisticated. This new strain of XLoader is just one example of that. And, while it’s currently focused on targeting Android users, it’ll likely be just a matter of time before it begins targeting Macs and other devices.
The best way to protect yourself, therefore, is to stay up-to-date with the latest cybersecurity trends and ensure your devices have good antivirus protection. Additionally, continue best practices for protecting yourself from suspicious links and downloads.
How stressed are you these days with malware like XLoader or other types of viruses trying to steal your data? Should more be done to stop these crooks? Let us know by writing us at Cyberguy.com/Contact
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.

Technology
Junji Ito’s terrifying Uzumaki hits Adult Swim in September
/cdn.vox-cdn.com/uploads/chorus_asset/file/25547597/Screen_Shot_2024_07_26_at_3.55.30_PM.png)
Adult Swim’s long-awaited adaptation of Uzumaki finally has a premiere date — and an appropriately creepy trailer. The series, based on the classic horror manga from Junji Ito, will start airing on September 28th. Episodes will hit Adult Swim first, and then stream on Max the following day.
Uzumaki follows a cursed town that is — and I promise it’s scarier than it sounds — plagued by spirals. Here’s the full synopsis:
“Let’s leave this town together,” asks Shuichi Saito, a former classmate of Kirie Goshima, a high school girl who was born and grew up in Kurouzu-cho. Everything from a strange whirlwind, billowing smoke from the crematorium, and the residents is turning into spirals. People’s eyes spin in whirls, a tongue spirals, and the…
Continue reading…
Technology
New prosthetics restore natural movement via nerve connection

In the world of prosthetics, a groundbreaking advancement is changing the game for individuals with lower-limb amputations.
Researchers at MIT, in collaboration with Brigham and Women’s Hospital, have developed a neuroprosthetic system that allows users to control their prosthetic legs using their own nervous systems.
This innovative approach could bring us closer to a future of fully integrated, naturally controlled artificial limbs.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
A person wearing the neuroprosthetic system (Hugh Herr and Hyungeun Song)
The AMI: A surgical game-changer
At the heart of this breakthrough is a surgical procedure known as the agonist-antagonist myoneural interface, or AMI. Unlike traditional amputation methods, the AMI reconnects muscles in the residual limb, preserving the natural push-pull dynamics of muscle pairs. This seemingly simple change has profound implications for prosthetic control and function.
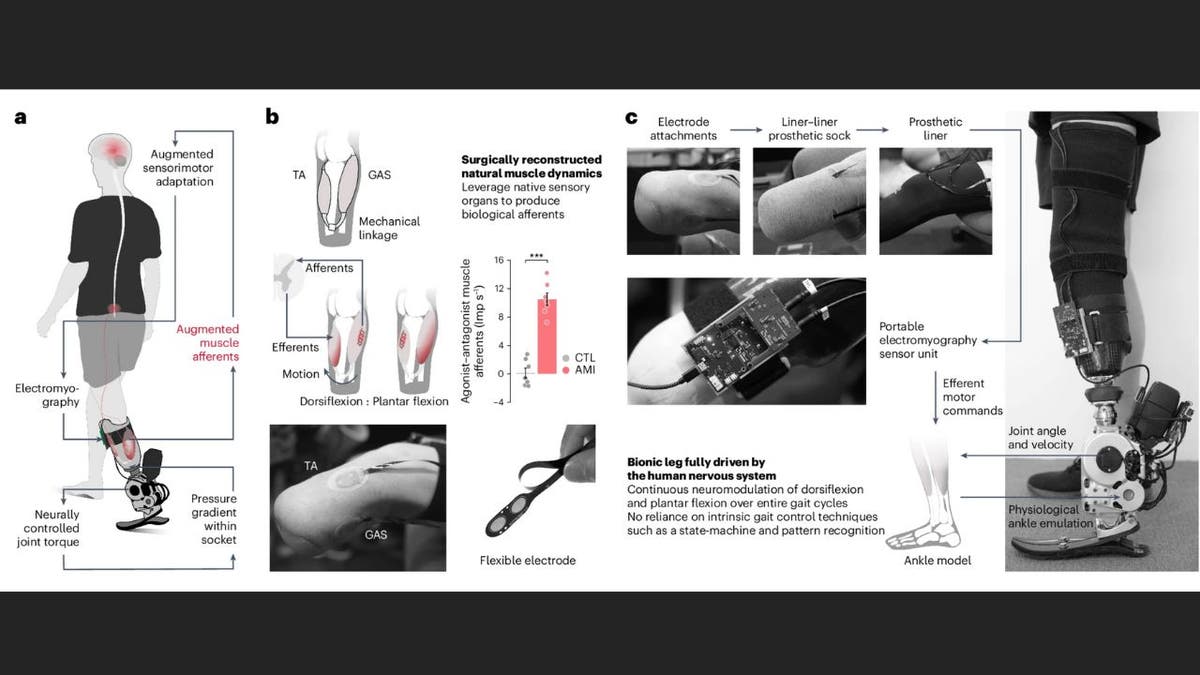
Illustration of how the neuroprosthetic system works (MIT Media Lab)
Dr. Hugh Herr, a professor at MIT and senior author of the study, explained the significance: “This is the first prosthetic study in history that shows a leg prosthesis under full neural modulation, where a biomimetic gait emerges. No one has been able to show this level of brain control that produces a natural gait, where the human’s nervous system is controlling the movement, not a robotic control algorithm.”
HOW TO STOP ANNOYING ROBOCALLS

Dr. Hugh Herr pictured with the neuroprosthetic system (Jimmy Day, MIT Media Lab)
AI-DRIVEN EXOSKELETON LIGHTENS YOUR LOAD AND ELEVATES PERFORMANCES
The power of proprioception
The key advantage of the AMI system is its ability to provide users with proprioceptive feedback, the sense of where their limb is in space. This sensory information, often taken for granted by those with intact limbs, is crucial for natural movement and control. With the AMI, patients regain a portion of this vital feedback, allowing them to walk more naturally and confidently.
In the study, seven patients with AMI surgery were compared to seven with traditional amputations. The results were striking. AMI patients walked faster, navigated obstacles more easily and climbed stairs with greater agility. They also demonstrated more natural movements, such as pointing their toes upward when stepping over obstacles, a subtle but important aspect of a natural gait.
CYBERCRIMINALS TAKING ADVANTAGE OF CROWDSTRIKE-LINKED GLOBAL COMPUTER OUTAGE

A person wearing the neuroprosthetic system (Hugh Herr and Hyungeun Song)
CLICK HERE FOR MORE US NEWS
Adapting to real-world challenges
One of the most impressive aspects of the AMI system is its versatility. Patients were able to adapt their gait to various real-world conditions, including walking on slopes and navigating stairs. This adaptability is crucial for everyday life, where terrain and challenges can change rapidly.
The system’s responsiveness was put to the test in an obstacle-crossing trial. AMI patients were able to modify their gait to clear obstacles more effectively than those with traditional prosthetics. This ability to rapidly adjust to unexpected challenges is a hallmark of natural limb function and represents a significant leap forward in prosthetic technology.
A person wearing the neuroprosthetic system (Hugh Herr and Hyungeun Song)
AI WEARABLE CONTRAPTION GIVES YOU SUPERHUMAN STRENGTH
The science of sensory feedback
The success of the AMI system hinges on its ability to augment residual muscle afferents, which are the sensory signals sent from muscles to the nervous system. Remarkably, even a modest increase in these signals allows for significantly improved control and function. This finding highlights the incredible adaptability of the human nervous system and its ability to integrate and utilize even partial sensory information.
Dr. Hyungeun Song, lead author of the study, notes: “One of the main findings here is that a small increase in neural feedback from your amputated limb can restore significant bionic neural controllability, to a point where you allow people to directly neurally control the speed of walking, adapt to different terrain and avoid obstacles.”

A person wearing the neuroprosthetic system (Hugh Herr and Hyungeun Song)
Looking to the future
While this research represents a significant step forward, it’s just the beginning. The team at MIT is exploring ways to further enhance sensory feedback and improve the integration between the human nervous system and prosthetic devices. The AMI procedure has already been performed on about 60 patients worldwide, including those with arm amputations, suggesting broad applicability across different types of limb loss.
As this technology continues to evolve, we may see even more natural and intuitive control of artificial limbs. The ultimate goal is to create prosthetics that feel and function like a natural part of the user’s body, blurring the line between human and machine.
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES

A person wearing the neuroprosthetic system (Hugh Herr and Hyungeun Song)
Kurt’s key takeaways
The development of prosthetic limbs controlled by the nervous system marks the beginning of a new era in bionics. It offers hope for improved mobility, independence and quality of life for millions of people living with limb loss. Moreover, it provides valuable insights into the plasticity of the human nervous system and our ability to integrate with advanced technology.
As we continue to push the boundaries of what’s possible in merging biology and technology, we open up new frontiers in human augmentation and rehabilitation. The implications extend far beyond prosthetics, potentially influencing fields such as neurology, robotics and even our understanding of human consciousness and embodiment.
How comfortable would you be with technology that directly interfaces with your nervous system? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Here’s your first look at Amazon’s Like a Dragon: Yakuza
/cdn.vox-cdn.com/uploads/chorus_asset/file/25547838/YAKZA_3840_2160_A_Elogo.jpg)
Amazon says that the show “showcases modern Japan and the dramatic stories of these intense characters, such as the legendary Kazuma Kiryu, that games in the past have not been able to explore.” Kiryu will be played by Ryoma Takeuchi, while Kento Kaku also starts as Akira Nishikiyama. The series is directed by Masaharu Take.
Like a Dragon: Yakuza starts streaming on Prime Video on October 24th with its first three episodes.
-

 World1 week ago
World1 week agoOne dead after car crashes into restaurant in Paris
-

 Midwest1 week ago
Midwest1 week agoMichigan rep posts video response to Stephen Colbert's joke about his RNC speech: 'Touché'
-

 News1 week ago
News1 week agoVideo: Young Republicans on Why Their Party Isn’t Reaching Gen Z (And What They Can Do About It)
-

 Movie Reviews1 week ago
Movie Reviews1 week agoMovie Review: A new generation drives into the storm in rousing ‘Twisters’
-

 News1 week ago
News1 week agoIn Milwaukee, Black Voters Struggle to Find a Home With Either Party
-
 Politics1 week ago
Politics1 week agoFox News Politics: The Call is Coming from Inside the House
-

 News1 week ago
News1 week agoVideo: J.D. Vance Accepts Vice-Presidential Nomination
-

 World1 week ago
World1 week agoTrump to take RNC stage for first speech since assassination attempt