xAI has released an iOS app in the US for its Grok chatbot, as spotted earlier by TechCrunch. The standalone app version of the chatbot, which xAI calls a beta, can perform the same functions as the one built into X, as it can field real-time information, answer questions, and generate images.
Technology
Over 600M cyberattacks target Windows users every day

Cyberattacks are more common than ever, and if you’re a Windows user, you’re probably feeling the impact more than others.
Hackers are always targeting Windows PCs, and you’ve probably seen reports about how system vulnerabilities let bad actors get to your personal and financial information.
However, if you want to understand just how many cyberattacks Windows users face every day, you’d be shocked to know that the number is well above 600 million. This proves that cyberattacks are on the rise now more than ever.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
Microsoft laptops (Microsoft)
What you need to know
Microsoft recently released its annual Digital Defense Report for 2024, revealing the state of the cybersecurity world.
“In the last year, the cyber threat landscape continued to become more dangerous and complex. The malign actors of the world are becoming better resourced and better prepared, with increasingly sophisticated tactics, techniques and tools that challenge even the world’s best cybersecurity defenders,“ the company said.
Microsoft says even it has been the victim of well-orchestrated attacks by determined and well-resourced adversaries, and its “customers face more than 600 million cybercriminal and nation-state attacks every day, ranging from ransomware to phishing to identity attacks.”
It’s not just everyday users getting hit by these attacks. Hackers are also going after government agencies, companies and organizations. The U.S. health care system alone has reportedly faced 389 successful cyberattacks this fiscal year, causing network shutdowns and delays in critical medical procedures.
The Redmond-based company also points out that the rising threat of cyberattacks isn’t just from regular cybercriminals anymore. Nation-states are stepping up their game in the cyber world, with more advanced techniques, thanks to bigger investments in resources and training. These state-sponsored hackers aren’t just stealing data. They’re launching ransomware, setting up backdoors for future attacks, sabotaging operations and running influence campaigns. According to Microsoft, China, Russia, North Korea and Iran are the biggest players.

A person typing on a Microsoft laptop (Kurt “CyberGuy” Knutsson)
CYBER SCAMMERS USE AI TO MANIPULATE GOOGLE SEARCH RESULTS
Most attacks target your password
Microsoft says 99% of the identity attacks are password attacks. They rely on predictable human behaviors such as selecting easy-to-guess passwords, reusing them on multiple websites and falling prey to phishing attacks. This shows the importance of using a reliable password manager.
A password manager helps you avoid common mistakes that make you an easy target for hackers. It stores all your passwords securely, generates strong, unique passwords for every site and autofills them when needed, so you don’t have to remember or reuse weak ones. Plus, it protects you from phishing attacks by ensuring you only log onto the correct sites. All of this reduces the chances of your accounts getting hacked and keeps your data safer. Get more details about my best expert-reviewed password managers of 2024 here.

Laptop on a table (Kurt “CyberGuy” Knutsson)
DON’T LET SNOOPS NEARBY LISTEN TO YOUR VOICEMAIL WITH THIS QUICK TIP
6 ways to protect yourself from cyberattacks
1. Enable two-factor authentication: Activate two-factor authentication (2FA) for an extra layer of security on all your important accounts, including email, banking and social media. Using 2FA requires you to provide a second piece of information, such as a code sent to your phone, in addition to your password when logging in. This makes it significantly harder for hackers to access your accounts, even if they have your password. Enabling 2FA can greatly reduce the risk of unauthorized access and protect your sensitive data.
2. Monitor your accounts and transactions: You should check your online accounts and transactions regularly for any suspicious or unauthorized activity. If you notice anything unusual, immediately report it to the service provider or authorities. You should also review your credit reports and scores to see if there are any signs of identity theft or fraud.
3. Contact your bank and credit card companies: If you think hackers have obtained your bank or credit card information, they could use it to make purchases or withdrawals without your consent. You should inform your bank and credit card companies of the situation. They can help you freeze or cancel your cards, dispute any fraudulent charges and issue new cards for you.
You should also contact one of the three major credit reporting agencies (Equifax, Experian or TransUnion) and request a fraud alert to be placed on your credit file. This will make it more difficult for identity thieves to open new accounts in your name without verification. You can even freeze your credit if need be.
4. Use personal data removal services: Consider investing in personal data removal services that specialize in continuously monitoring and removing your personal information from various online databases and websites. These services employ advanced tools and techniques to identify and eliminate your data from people search sites, data brokers and other platforms where your information might be exposed. By using a data removal service, you can minimize the risk of identity theft and fraud, especially after a data breach. Additionally, these services often provide ongoing monitoring and alerts, keeping you informed of any new instances of your data appearing online and taking immediate action to remove it. Check out my top picks for data removal services here.
5. Sign up for identity theft protection: Identity theft protection companies can monitor personal information like your home title, Social Security number, phone number and email address and alert you if it is being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals.
One of the best parts of using some services is that they might include identity theft insurance of up to $1 million to cover losses and legal fees and a white glove fraud resolution team through which a U.S.-based case manager helps you recover any losses. See my tips and best picks on how to protect yourself from identity theft.
6. Have strong antivirus software: The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android and iOS devices.
WINDOWS FLAW LETS HACKERS SNEAK INTO YOUR PC OVER WI-FI
Kurt’s key takeaway
Cyberattacks are getting more dangerous, and hackers are way better equipped to pull off the perfect attack. They’re even using artificial intelligence and deepfakes to make everything seem more legit. Add in the fact that many of these attacks are backed by nation-states, and it’s clear we need to step up our cybersecurity game — more investment is definitely needed. On the bright side, Microsoft managed to block around 1.25 million DDoS attacks, which is four times more than last year. That shows they’re working hard to give users a safer experience.
Do you think AI and deepfakes will make it harder to spot cyberthreats? Let us know by writing us at Cyberguy.com/Contact
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you’d like us to cover
Follow Kurt on his social channels
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2024 CyberGuy.com. All rights reserved.

Technology
This wildfire evacuation alert accidentally went out to everyone in LA
/cdn.vox-cdn.com/uploads/chorus_asset/file/25824936/Image_from_iOS__2_.jpg)
After two days of dealing with wildfires that have burned thousands of acres, residents across Los Angeles County received a wildfire evacuation alert on Thursday afternoon that was a mistake. Shortly after, officials sent a follow-up alert saying that the notice was intended only for people near the Kenneth Fire in Woodland Hills.
Los Angeles County shared a message on X explaining what happened: “An evacuation order for residents near the Kenneth Fire currently burning in West Hills was mistakenly issued Countywide. This alert was only intended for residents of Calabasas and Agoura Hills.”
CBS News quotes a local official who said that the alert, which included a broken URL, was sent “due to a technical error.”
Many wildfires are burning in the LA area, and officials have confirmed at least six deaths, CNN reports. LA County has a population of nearly 10 million people, which is the “largest population of any county in the nation,” according to the county’s website.
Technology
Solar device transforms used tires to help purify water so that it's drinkable

Imagine a world where clean drinking water is readily available even in the most remote areas.
This vision is becoming a reality thanks to innovative research from scientists in Canada.
A team of scientists at Dalhousie University in Halifax, Nova Scotia, has developed a groundbreaking device that could revolutionize water desalination, offering hope to millions facing water scarcity worldwide.
I’M GIVING AWAY THE LATEST & GREATEST AIRPODS PRO 2
Floating solar still process (Dalhousie University)
The power of plasmonic solar stills
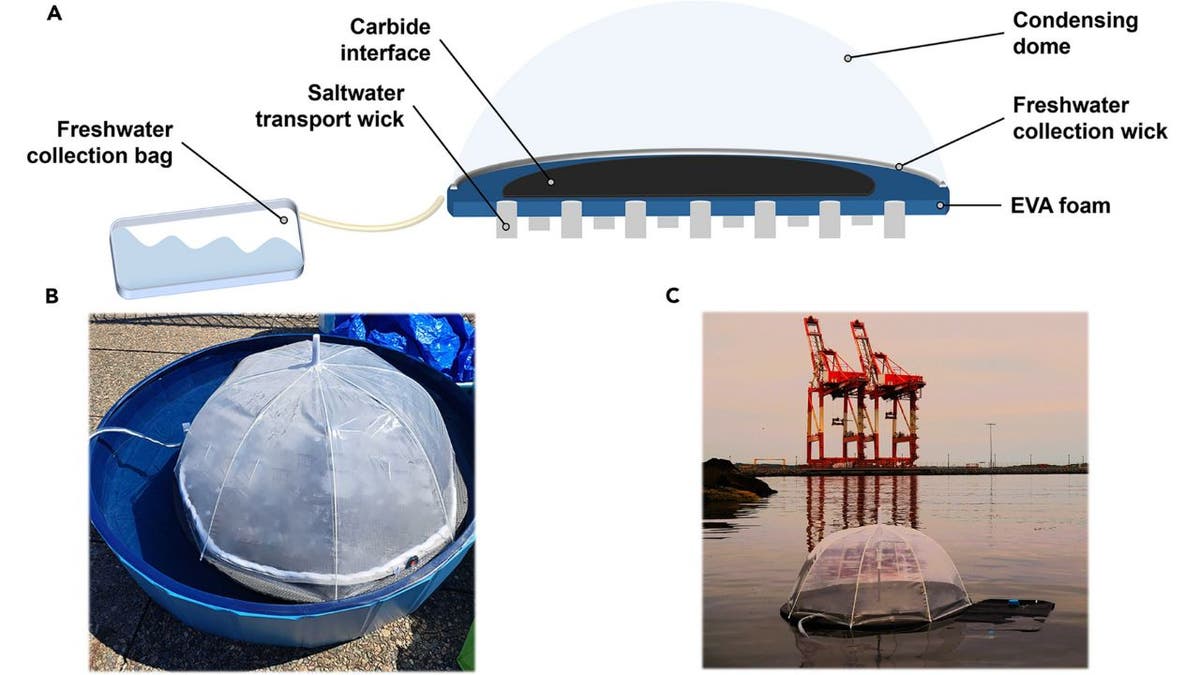
At the heart of this innovation is a floating solar still, a device that harnesses the sun’s energy to purify seawater.
Dr. Mita Dasog, an associate professor of chemistry and Killam Memorial chair at Dalhousie, explains the science behind it: “Refractory plasmonic nanomaterials are very good at capturing light and converting that light into heat.”
This principle forms the foundation of their ingenious design. The solar still, conceptualized by Dr. Matthew Margeson during his Ph.D. studies, addresses challenges that have long plagued similar devices. It minimizes thermal losses, prevents salt buildup and can withstand harsh maritime conditions.

Researcher pictured next to floating solar still (Matthew J. Margeson)
A BREAKTHROUGH GADGET COULD HELP YOU DETECT MICROPLASTICS IN YOUR DRINKING WATER
How it works
The floating solar still operates through an elegantly simple yet highly effective process. First, ocean water is drawn up to the device’s foam surface through a wicking system. Once the water reaches the surface, it is evaporated by solar-heated plasmonic materials. As the water vapor rises, the salt is left behind, ensuring that only purified water is collected. The vapor then recondenses on a clear plastic dome situated above the device. Finally, the purified water is funneled down the sides of the dome and collected in a sealed bag for easy access.
The results of this process are impressive. In real-world tests conducted in Halifax Harbour, the device produced up to 0.97 gallons of clean water daily, which was a record-breaking yield for passive floating solar stills.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
Floating solar still process (Dalhousie University)
AUTONOMOUS TRASH-GOBBLING ROBO BOAT WAGES WAR ON WATERWAY WASTE
Upcycling for sustainability
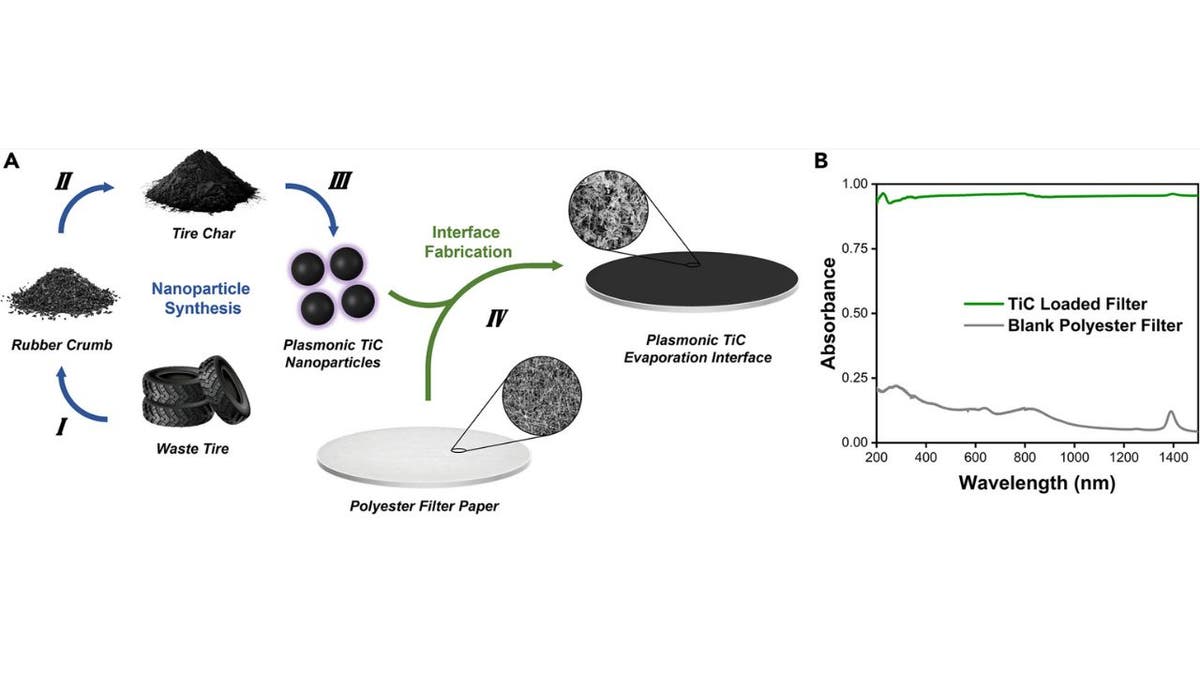
What sets this device apart is its use of unconventional materials. Instead of relying on expensive precious metals, the team turned to an unlikely source: used tires. Through a process called pyrolysis, carbon waste from tires is transformed into a crucial component of the desalination unit.
Dr. Dasog emphasizes the importance of accessibility: “We shouldn’t be making an expensive or very complicated device. It has to be easy to manufacture, last for a long time and be easy to take apart and move.” This approach not only makes the technology more affordable but also addresses the environmental issue of tire waste.
Floating solar still process (Dalhousie University)
THE SHAPE-SHIFTING UNDERWATER ROBOT PIONEERING THE DEPTHS OF THE SEA
Affordable water purification and energy generation in one device
The device’s capabilities extend beyond water purification. It can simultaneously desalinate, disinfect and decontaminate water at a remarkably low cost: less than one cent per liter. It can also generate a small amount of thermoelectricity, potentially powering onboard water quality sensors.
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES
Looking ahead
The team’s next step is to conduct further testing in South Asia, with the ultimate goal of making the device available worldwide. Dasog, nominated for the Emerging Leader award at the Water Canada Summit, envisions the device as a lifeline for communities displaced by war or climate change.
Kurt’s key takeaways
As we tackle the growing challenges of water security, innovations like the plasmonic solar still shine a light of hope. By blending cutting-edge science with sustainable materials, the researchers at Dalhousie University are doing more than just purifying water; they’re paving the way for a future that is both equitable and resourceful. This device not only makes clean drinking water accessible but also highlights how we can use renewable energy sources to address pressing global issues.
If the sun could power one solution to improve human life, what would you want it to be? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.
Technology
X launches Grok’s iPhone app in the US
/cdn.vox-cdn.com/uploads/chorus_asset/file/25330839/STK262_GROK_B.png)
xAI started testing Grok’s standalone iOS app in December in a handful of countries. There’s no word on when it may come to Android.
Though Grok was initially only available to X Premium subscribers, the platform started letting all users access the chatbot last month, bringing it in line with other free-to-use chatbots like OpenAI’s ChatGPT, Anthropic’s Claude, Google Gemini, and Microsoft Copilot.
As pointed out by TechCrunch, it seems xAI is also working on a dedicated Grok.com website that currently has a “coming soon” message on it. After raising $6 billion in June, xAI reported another $6 billion funding round, including from “strategic investors” like Nvidia and AMD.
-

 Business1 week ago
Business1 week agoThese are the top 7 issues facing the struggling restaurant industry in 2025
-

 Culture1 week ago
Culture1 week agoThe 25 worst losses in college football history, including Baylor’s 2024 entry at Colorado
-

 Sports1 week ago
Sports1 week agoThe top out-of-contract players available as free transfers: Kimmich, De Bruyne, Van Dijk…
-

 Politics1 week ago
Politics1 week agoNew Orleans attacker had 'remote detonator' for explosives in French Quarter, Biden says
-

 Politics7 days ago
Politics7 days agoCarter's judicial picks reshaped the federal bench across the country
-

 Politics5 days ago
Politics5 days agoWho Are the Recipients of the Presidential Medal of Freedom?
-

 Health4 days ago
Health4 days agoOzempic ‘microdosing’ is the new weight-loss trend: Should you try it?
-

 World1 week ago
World1 week agoIvory Coast says French troops to leave country after decades















