Technology
In Ukraine, hacktivists fight back with data leaks

The video opens in typical Nameless type, with 3D-rendered textual content and grainy Man Fawkes masks flickering over photographs of road protest.
“Greetings, world! We’re Nameless,” a distorted voice says. “We see the clouds of battle … and it angers us.”
Uploaded to YouTube and shared to the 7.8 million followers of @YourAnonNews on Twitter, this video was cited because the second that Nameless “declared battle on Russia.” It’s a deceptive declare since Nameless is much less of a standing military than an all-purpose hacktivist nom de guerre, however the transfer was nonetheless vital. Loads of web bystanders have been on the point of make hassle for Russia — they usually have been going to make use of the mantle of Nameless to do it.
Many anticipated a extra organized cyber-offensive from Russia, nevertheless it hasn’t materialized for causes which can be tough to pin down. The fact has been extra chaotic, with little oversight or coordination. These smaller incidents are extra favorable for Ukraine, however they’re additionally qualitatively completely different from army operations like Stuxnet or Sandworm. And whereas standard warfare continues to devastate Ukraine, the Nameless marketing campaign has been working extra quietly within the background, with penalties which can be exhausting to foretell.
On February twenty sixth, Ukraine’s deputy prime minister Mykhailo Fedorov — who can also be minister for digital transformation — introduced the creation of a volunteer-led cyber military, enlisting the assistance of any and all expert employees from the IT sphere to take part in a spread of digital actions in opposition to Russia.
The cyber volunteers have been already venturing into uncharted territory. Coordinated by means of a Telegram channel of, at current, greater than 300,000 customers, membership of the so-called “IT Military” was each globally distributed and centrally directed, plotting a brand new line between decentralized digital activism and state-sponsored hacking. However whereas the IT Military launched into a brand new sort of cyberwarfare, Nameless’s #OpRussia represented a special, altogether extra chaotic tendency.
The IT Military has leaned closely on DDoS assaults — carried out on targets like fuel, oil and infrastructure corporations, the Moscow Inventory Alternate, and even the Kremlin web site utilizing an app known as disBalancer — however essentially the most impactful actions have come from stealing knowledge and posting it to the general public. In a single case, teams working beneath the names Nameless Liberland and the Pwn-Bär Hack Crew obtained over 200GB of emails from Belarusian protection weapons producer Tetraedr, which have been made obtainable by means of the leak web site Distributed Denial of Secrets and techniques.
In one other incident, a hacking group breached a web site belonging to Russia’s Area Analysis Institute and leaked information on-line that appeared to incorporate descriptions of lunar missions. Days earlier than, one other group known as In opposition to The West (ATW) — which was beforehand recognized for leaking knowledge obtained from the Chinese language Communist Get together — launched a trove of information purportedly obtained from energy company PromEngineering, together with energy station blueprints and schematics.
The most recent main leak occurred on March tenth, when Distributed Denial of Secrets and techniques printed greater than 800GB of leaked knowledge from Roskomnadzor: the Federal Service for Supervision of Communications, Info Expertise, and Mass Media, or Russia’s major censorship company. Although the actor that obtained the information isn’t but unknown, the character of the leaks is at minimal extremely embarrassing to Roskomnadzor and probably extra damaging relying on the precise data launched.
In trying to strike blows in opposition to Russia, hacktivist teams aligned with Ukraine have successfully been leaking no matter delicate data they will discover in opposition to Russian targets. However as soon as this data is launched, it’s exhausting to comprise — and there could also be unintended penalties. DarkOwl, a darkish net intelligence firm, is one group that has been monitoring knowledge leaks tied to the Ukraine invasion in a weblog. A DarkOwl analyst informed The Verge that data contained in company leaks may very well be worthwhile for spear phishing or surveillance campaigns, particularly for essentially the most subtle actors.
“You’ve bought delicate company data right here. You already know, you’ve bought delivery addresses and account numbers and issues like that,” the analyst mentioned. “There’s additionally pictures and screenshots which were taken. As we’ve got seen, that can be utilized in additional strategic espionage exercise by a nation state actor sooner or later.”
However lots of the leaks additionally comprise giant volumes of details about corporations’ shoppers, most of that are extraordinary Russians with little connection to the elite pursuits which have waged the battle. That data may put them in danger at a later date.
“This flurry of motion that we see proper now could be mainly to vandalize and create as a lot chaos as potential,” says Jeremiah Fowler, an American cybersecurity researcher primarily based in Ukraine. “However having names, person particulars, credit score data, any of that on the market long run, you understand that we don’t know what they’re going to do with that. There’s sadly a lot anger about all this that lots of harmless Russian individuals could also be focused by default.”
The loosely coordinated, typically beginner nature of hacktivist help for Ukraine has additionally meant that it’s more durable to confirm precisely what’s going down at a given second. Some well-publicized Nameless actions have been patently false: in a single instance, an Nameless data channel claimed that an affiliated group had shut down the main control system for Russian satellites; in one other, debunked by the Verify Level cybersecurity agency, a gaggle that claimed to have hacked into CCTV cameras inside a nuclear energy plant was discovered to be reusing years-old footage from YouTube.
Different believable hacks have been exhausting to verify. On February twenty sixth, some social media customers shared footage that allegedly confirmed Russian TV channels hacked to broadcast pro-Ukrainian messages and inform watchers of the reality in regards to the Ukraine invasion. (Information media in Russia is closely censored, much more so after Putin signed a “pretend information” regulation that threatened as much as 15 years in jail for individuals who unfold unapproved details about Russian battle losses.)
Fowler says his analysis associate had straight noticed a hijacked Russian TV broadcast and that it was potential that it had occurred many extra instances. Fowler mentioned that he had encountered unsecured file programs when researching Russian media companies and that somebody with the technical talent to find them may simply change broadcast footage:
“Let’s say you had administrative entry,” Fowler mentioned. “You are taking a video of a few of this horrific [war] footage that we’re seeing, and also you title that the identical because the supply materials. So subsequent time the software program pulls from that supply, as an alternative of getting no matter information they’re offering, the viewers goes to see one thing else. And the system doesn’t know any completely different as a result of the file has the identical title.”
Somebody hacked into Russian state TV channels. They function Ukrainian music and nationwide symbols.
Web customers suspect that this can be one other motion by the hacker group #Anonymous, which declared a cyber battle to Russia in reference to the assault on #Ukraine. pic.twitter.com/XaoclymVTs
— BECZKA ✌️ (@beczka_tv) February 26, 2022
Fowler mentioned that he had additionally seen proof of quite a few Russian firm databases that had been accessed by outsiders, with knowledge deleted, or information rewritten en masse to say “Putin cease this battle” — to the extent that in a pattern of 100 publicly uncovered databases, 92 appeared to have been tampered with. Many of those databases contained names, account particulars, and different personally figuring out data, Fowler mentioned; and there’s no method to know precisely who may need had entry to it.
Some people who act now as “cyber patriots” supporting Ukraine may additionally be concerned in prison exercise, mentioned Jon Clay, vp of menace intelligence at Pattern Micro — and laptop programs which can be compromised now as protest may later be exploited for monetary acquire.
“Loads of these cyber patriots could also be a part of a cybercriminal group,” Clay mentioned. “In order that they’re being given cowl by the nation state to focus on these different teams, or companies in a special nation. And that’s the place it’s going to be tough to attract the road as a result of, you understand, in a short time they will pivot to only turning on the cybercrime part of their enterprise.”
Teams concerned in pro-Ukraine hacks may implant backdoors into laptop programs that they might reactivate for future exploits, Clay mentioned, with stealthier actors in a position to stay undetected for months and even years. Additional down the road, these teams may promote person knowledge for revenue or deploy ransomware, he mentioned.
So long as the battlefield continues to be blanketed in what has been known as “the fog of cyberwar,” there may be additionally a chance that a number of the most subtle cyber menace actors are working beneath cowl of hacktivism.
In a webinar Thursday, Kaspersky’s director of worldwide analysis and evaluation Costin Raiu mentioned that some cyber exercise in Ukraine had the hallmark of Superior Persistent Risk teams (APTs) — essentially the most elevated stage of cyber menace group, and normally one that’s directed by a army company or backed by a nation state — and may need been hidden beneath “false flag” cybercrime or hacktivist operations.
Nonetheless, the haphazard nature of the hacktivist actions may cause actual harm — typically to individuals or infrastructure with no connection to the invading forces. “It’s very harmful for individuals when you’ll be able to’t see three steps down the road to be taking offensive actions,” mentioned Chester Wisniewski, principal analysis scientist at Sophos. “An indicator of what we might take into account acceptable offensive hacking on behalf of the British, the Israelis, the People, even the Russians and the Chinese language, is to know what the potential impacts of your actions are going to be and to reduce collateral harm by being very exact and focused in these actions.”
“Civilians aren’t ready to do this successfully,” Wisniewski provides. “And I’m very involved about that.”

Technology
Samsung mocks Apple’s crushing iPad Pro ad with its own ‘UnCrush’ pitch
/cdn.vox-cdn.com/uploads/chorus_asset/file/25450390/videoframe_33450.png)
On one side, responses included creatives like Hugh Grant and anyone who spotted a slightly-too-on-the-nose representation of Big Tech’s steamroller approach to art, copyright, and the past, powered by the might of generative AI tools. On the other there were the people ticked off by the knowledge that there was any backlash at all.
In response, the Samsung Mobile account on X posted this video with the hashtag “UnCrush,” which Ad Age reports was created by BBH USA and directed by Zen Pace. It shows a woman stepping over debris and spilled paint reminiscent of the end of Apple’s big hydraulic press incident and taking a seat to hum and play notes on a guitar assisted somehow by notes displayed on her Galaxy Tab S9 and the power of Galaxy AI.
No matter which side you’re on when it comes to the great iPad ad political divide, it’s a little fun to see Samsung trying to find a weak point in Apple’s armor again. Samsung’s marketing department used to practically specialize in this stuff, which the company’s lawyers’ argued: “drove Apple crazy,” but it seemed to run out of gas after deleting ads about iPhones dropping the in-box charging adapted. More recent attempts, like a browser-based Galaxy test drive for iPhone owners, just haven’t had the same punch as mocking that distinctive notch.
Technology
How to change camera zoom levels on your iPhone

‘CyberGuy’: A zoom with a view
The iPhone 15 Pro and Pro Max offer customizable camera zoom settings to easily switch between standard, ultrawide and precise zoom levels. Kurt Knutsson shows you how.
Have you ever gone to take a photo and wished you could capture it with just the right amount of zoom on your iPhone? Well, if you’re the proud owner of an iPhone 15 Pro or Pro Max, you’re in luck because these devices have an amazing camera setup.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER
iPhone 15 Pro (Apple) (Kurt “CyberGuy” Knutsson)
iOS17 and later allows you to change camera zoom levels
Let’s talk about the main camera first. It offers a standard 1x zoom, perfect for crisp, clear shots that capture life as it happens. But wait, there’s more. The ultrawide camera brings a whole new perspective with a 0.5x zoom, allowing you to soak in more of the scene in a single frame. Now, here’s where it gets exciting: with iOS 17 and later, you can tweak your zoom levels directly from the menu. That’s right, no more fiddling around.
MORE: THE HIDDEN CAMERA APP ON YOUR PHONE UNLOCKING AN AMAZING PERK
How to set up default zoom for main camera
Want to jump straight to your preferred zoom level every time you open the camera? It’s a breeze. Just follow these steps:
- Open your Settings app
- Tap on Camera
- Then scroll down to Main Camera and tap it.
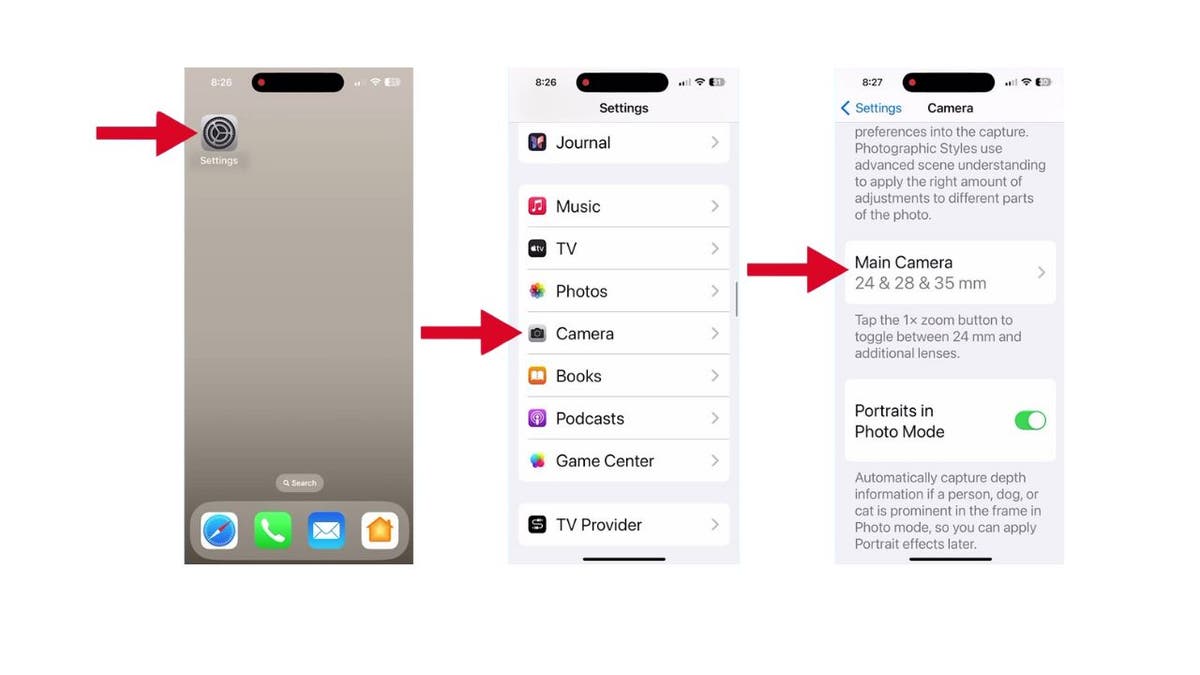
Steps to set up default zoom for main camera (Kurt “CyberGuy” Knutsson)
- Here, you’ll find options to adjust your camera zoom. You can set it to Default to 24 mm – 1x, Default to 28 mm – 1.2x, or Default to 35 mm – 1.5x.
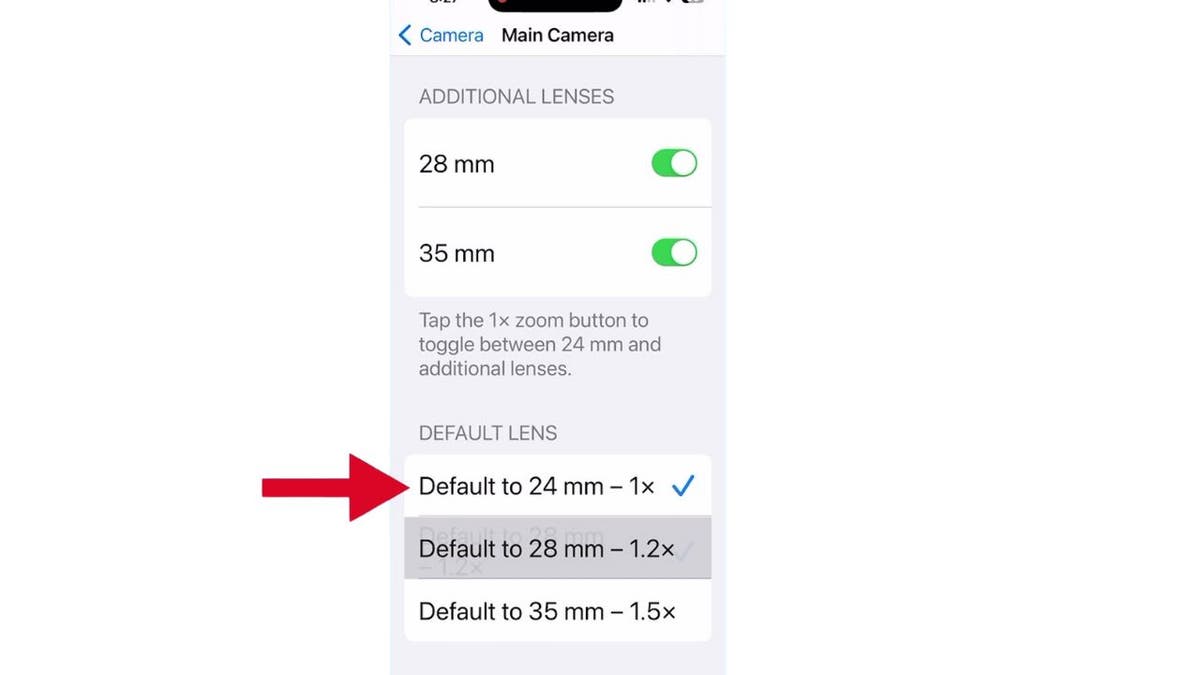
Steps to set up default zoom for main camera (Kurt “CyberGuy” Knutsson)
MORE: HOW TO SNAP PERFECT SHOT TAKING PHOTOS WITH YOUR CAMERA’S BURST MODE
How to adjust the zoom on the camera app for a specific moment
For those times when you need to quickly adjust the zoom for a specific moment, the Camera app makes it a breeze.
- Open the Camera app
- Press and hold down the 1x button
- A wheel will appear, allowing you to dial in the zoom level for that specific moment.
- Spin it to your desired magnification and snap away with precision from ultrawide to telephoto.
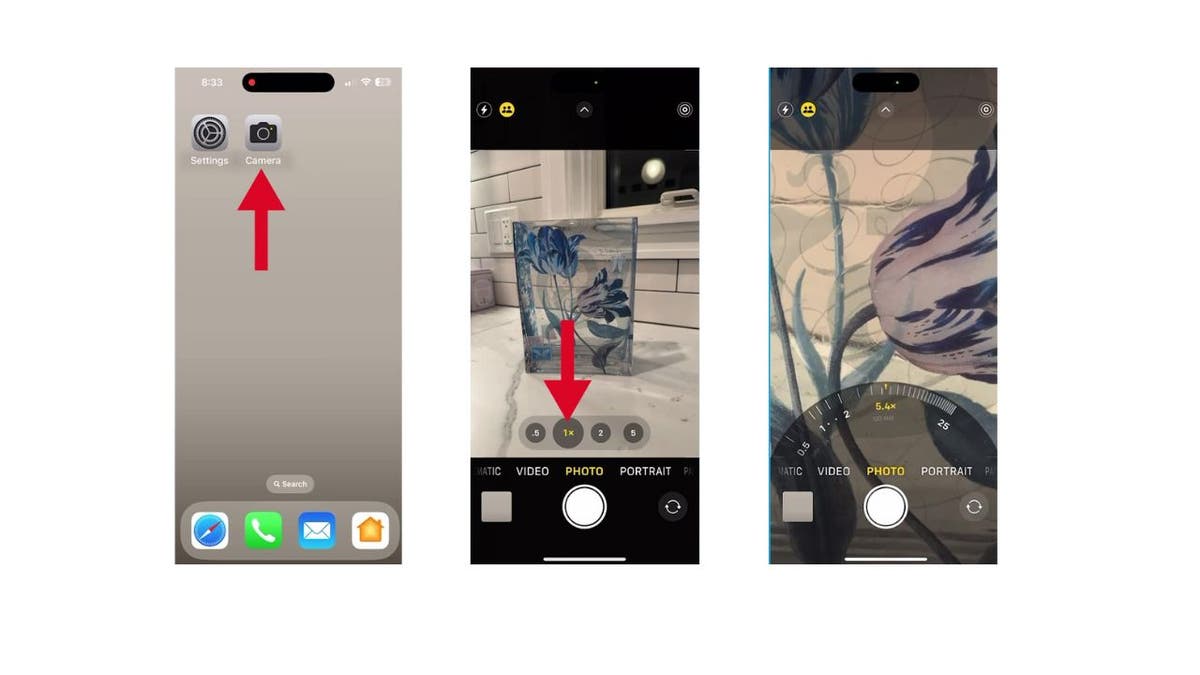
Steps to adjust the zoom on the camera app (Kurt “CyberGuy” Knutsson)
With these simple steps, you’ve just unlocked the secrets to becoming a zoom master on your iPhone 15 or later. So go ahead, give it a spin and capture those perfect shots that’ll make your friends go, “Wow.”
MORE: THE AI CAMERA STRIPPING AWAY PRIVACY IN BLINK OF AN EYE
Kurt’s key takeaways
So, whether you’re looking to capture sweeping landscapes or get up close with your subject, the zoom features on the iPhone 15 Pro and Pro Max make it easy to frame the perfect shot every time.
How has the evolution of smartphone cameras, particularly with the iPhone 15 Pro or Pro Max, changed how you capture and share your life’s moments? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Microsoft’s AI obsession is jeopardizing its climate ambitions
/cdn.vox-cdn.com/uploads/chorus_asset/file/25449864/2150504820.jpg)
Microsoft’s producing a lot more planet-heating pollution now than it did when it made a bold climate pledge back in 2020. Its greenhouse gas emissions were actually around 30 percent higher in fiscal year 2023, showing how hard it could be for the company to meet climate goals as it simultaneously races to be a leader in AI.
“In many ways the moon is five times as far away as it was in 2020”
Back in 2020, Microsoft set a target of becoming carbon negative by the end of the decade. To translate the jargon, it pledged to slash greenhouse gas emissions by more than half and then capture a greater amount of carbon dioxide emissions than it would produce. It was an audacious commitment to make at the time, considering carbon capture technologies were barely coming into existence. The company would also have to spur the deployment of way more renewable energy onto power grids where it operates.
“In 2020, we unveiled what we called our carbon moonshot. That was before the explosion in artificial intelligence,” Microsoft president Brad Smith said in an interview with Bloomberg. “So in many ways the moon is five times as far away as it was in 2020, if you just think of our own forecast for the expansion of AI and its electrical needs.”
Diving into the data in Microsoft’s sustainability report, you can see just how far it’s gone in the wrong direction. It pumped out 15.357 million metric tons of carbon dioxide over the last fiscal year, comparable to the annual carbon pollution of Haiti or Brunei.
Data centers used to train AI are even more energy-intensive than traditional data centers that already gobble up a lot of electricity to run servers and cooling systems to prevent overheating. And Microsoft has plans to build a whole lot more of those data centers now that it’s all in on AI. The company planned to spend $50 billion over the past fiscal year in order to meet its AI ambitions — a figure it’s expected to surpass in the following year, Bloomberg reports.
-

 Politics1 week ago
Politics1 week agoHouse Dems seeking re-election seemingly reverse course, call on Biden to 'bring order to the southern border'
-

 World1 week ago
World1 week agoStand-in Jose Raul Mulino wins Panama presidential race
-

 News1 week ago
News1 week agoCompass Direct LLC’s 2024 Registration in North Carolina
-
News1 week ago
UCLA to resume in-person classes after Gaza protest crackdown
-

 World1 week ago
World1 week agoTech compliance reports, Newsletter
-

 News1 week ago
News1 week agoColumbia University cancels its main commencement ceremony after weeks of turmoil
-

 News1 week ago
News1 week agoMan, 75, confesses to killing wife in hospital because he couldn’t afford her care, court documents say
-

 World1 week ago
World1 week agoPentagon chief confirms US pause on weapons shipment to Israel














