In addition to the Surface Pro and Surface Laptop, Microsoft announced a crop of Copilot Plus PCs from all the major OEMs. Here are all the Copilot Plus PCs announced at Microsoft’s Surface event on Monday.
Technology
How the EU is fighting tech giants with Margrethe Vestager

Margrethe Vestager is among the driving forces behind tech regulation worldwide. Appointed because the European Fee’s commissioner of competitors in 2014 and an government vp in 2019, she’s pursued antitrust circumstances towards Apple, Google, Meta (previously Fb), and Amazon amongst others. Now, with the EU on the verge of implementing a brand new antitrust regulation referred to as the Digital Markets Act, Vestager is planning her subsequent strikes.
The DMA designates a class of tech “gatekeepers,” then outlines guidelines towards behaviors like giving choice to their very own companies or gaining an unfair benefit with analytics information. Vestager hopes it might probably handle systemic issues that particular person enforcement actions can’t, and that it’ll streamline circumstances the EU does carry towards firms. However after I caught up together with her on the SXSW convention in Austin, the place she was talking about disinformation and democracy, she mentioned there’s nonetheless work left to do earlier than it passes.
There’s additionally a variety of rising applied sciences that would pose new issues, like cryptocurrency and the “metaverse” — which Vestager has mentioned most likely wants regulation as soon as she figures out precisely what it’s. And we mentioned the questions that antitrust guidelines can’t reply, like how firms ought to reply to unlawful content material on their platforms.
Okay, Margrethe Vestager. Right here we go.
This transcript has been flippantly edited for readability.
Govt Vice President Margrethe Vestager, welcome to Decoder.
Nicely, thanks very a lot.
Let’s begin by laying out the sphere of antitrust enforcement proper now for the EU. May you undergo the massive circumstances which can be on the desk?
On Friday we simply opened a brand new case with Google and Fb, now Meta. It’s referred to as Jedi Blue, named after the codename for an settlement that they appear to have entered again in 2018, with the purpose, seemingly, to kill off Google rivals within the promoting ecosystem. We even have one other Google case solely specializing in Google and the ad-tech stack, a few of the behaviors that appear to be anti-competitive.
Then now we have three Apple circumstances: one regarding music streaming companies and the 30 p.c payment, then now we have a extra normal Apple App Retailer case, after which now we have an Apple Pay case about entry to the fee infrastructure or know-how in your telephone. We’ve got two Amazon circumstances: one considerations entry to information — it appears as if Amazon Retail have had entry to all the information from the smaller retailers on the Amazon market, enabling Amazon Retail to have a head begin on quite a few merchandise and costs within the market — and the second is about their success system. We even have a case regarding promoting within the Fb atmosphere. So our to-do listing is sort of full.
It’s. You even have new laws which can be going to, in concept, come into pressure moderately quickly.
Sure. One of many issues that I’ve discovered over these seven years [as a European Commissioner] is that a few of these behaviors are systemic, and then you definately want a systemic reply. Additionally, that we have to acquire pace. As a result of if unlawful habits is allowed to proceed even for a brief period of time, the chance that rivals will undergo — and due to that, customers will undergo — is admittedly large. So with the Digital Markets Act, we wish a quite simple, basic factor: we wish the market to be open and contestable. So it relies on your concepts, your work ethics, your skill to draw capital, whether or not you’ll achieve success along with your prospects or not. And sadly, due to the systemic nature of habits, that’s not essentially the case at present.
Would you be capable of undergo a few of the specifics of the Digital Markets Act?
The concept is to say that you just’re greater than welcome to achieve success within the European market, however in case you develop in market energy, you also needs to develop in duty. So now we have developed a set of goal standards, and in case you fall into these, we’ll designate you as a gatekeeper. That offers you sure prohibitions and obligations. A prohibition may very well be that you just’re not allowed to self-preference. Or in neighboring markets to the market the place you’re the gatekeeper, an obligation may very well be to share information — if you’re within the gatekeeper’s market, you’d really get information that your individual enterprise is producing, for your self and for the event of what you are promoting.
You’ve talked about enforceability being the final piece of the puzzle for the Digital Markets Act. May you speak somewhat bit extra about what meaning and what it’s going to require?
Generally it makes me really feel very previous, however having been working with laws for an enormous majority of my life, I’ve realized that laws is barely nearly as good as its enforcement. So it’s actually essential that we get the enforcement arrange in a approach that it’ll work on the bottom. As a result of now we have numerous ambitions, however they need to turn into actual in on a regular basis life, for companies that wish to be in an open, contestable market.
These usually are not trivial issues — it’s not trivial to designate a gatekeeper. It’s not trivial to have the regulatory dialogue in order that gatekeepers know what they’re purported to do. So that’s the final piece of the puzzle that we’re pushing within the late section of the negotiations of the Digital Markets Act.
You talked somewhat bit about this, however I wish to develop on it extra. What are the important thing components of creating positive that is enforceable?
One of many issues we have to preserve is that the fee is liable for the enforcement. We’ve got superb expertise working with nationwide competitors authorities, and we’d like all assets to be mobilized so as to implement our guidelines. However we also needs to preserve that it’s the fee who has the final phrase — who would take the selections and implement this piece of laws. And within the final phases of a negotiation, generally that you must take a step again to just be sure you get the basics proper, so the laws shouldn’t be challengeable. So it’s actually about staying centered within the final a part of a negotiation, in order that we all know that what’s within the regulation are issues that we even have a really clear thought of how they are going to work in actual life.
What are some examples of circumstances we would see with the Digital Markets Act that haven’t been potential up to now?
Hopefully numerous issues can be solved earlier than it turns into an actual challenge. As a result of the complete thought is that we don’t need extra markets to tip. We don’t need issues to occur due to unlawful habits within the market.
And deciding beforehand, based mostly on goal standards, that [companies] do have these obligations, issues they’ll and can’t do, will pace issues up. After we open a contest case at present, the very first thing we do is to evaluate whether or not the enterprise is dominant within the related market, and that in itself can take a surprisingly very long time. And provided that we are able to show dominance do now we have a case, as a result of a smaller enterprise that’s not dominant can do an enormous variety of issues that the dominant firm can’t.
Saying beforehand “You are actually designated a gatekeeper” ought to give us that pace — in ensuring that {the marketplace} is open, that there is no such thing as a self-preferencing, that companies get their information, that app shops are open; {that a} second app retailer could be in your telephone in case you would need it to. And that form of pace, I believe, mirrors the character of digital markets.
I believe there’s usually a way of cynicism round tech firm enforcement — that the businesses will simply choose to pay a high quality and get a financial slap on the wrist. How does the Digital Markets Act handle that?
It’s not only a concept. The Dutch competitors authorities had a case the place they requested Apple to vary a sure habits within the App Retailer, and up to now Apple has not carried out these modifications they usually pay a weekly high quality — I believe it’s 5 million euros. And that’s actually thought-provoking, as a result of the thought, in fact, from the Dutch authority is that in implementing these modifications, you’d have a extra truthful market state of affairs.
For this reason, within the Digital Markets Act, there’s a full toolbox the place the sanctions turn into increasingly more extreme. The fines will enhance if you don’t implement modifications. Ultimately, within the toolbox, there’s additionally the device that you would be able to really break up an organization if no change is going on, or if you’re a repeat offender.
What’s the interaction proper now between EU and US regulation and enforcement? The Jedi Blue case you talked about started as a state lawsuit within the US.
Sure. We took inspiration from the state legal professional normal in Texas who filed this swimsuit, and we opened our personal with the CMA [Competition and Markets Authority] of the UK. I believe it exhibits that there’s a sense of alignment. We would not have a worldwide competitors authority. We’ve got many various competitors authorities. However there’s a new sense of widespread function right here for the market to remain open. I maintain a map the place I can type of put pins in issues, like: now the Australians, they’re trying into this habits; now the Indians are into that habits; now the South Individuals, they’re trying into this. And there’s a sample exhibiting that competitors authorities all around the planet are zooming in on the digital financial system so as to ensure that markets are aggressive.
We even have very shut cooperation with our US colleagues. In parallel to the [EU-US] Commerce and Expertise Council, now we have a coverage dialogue between the US and EU on competitors in tech-driven markets; we had the primary interplay of that and that was, I believe, very profitable. It might take a while earlier than we do widespread circumstances, relying available on the market state of affairs, however I believe the alignment as to how we see these markets is rising increasingly more.
You talked about Australia, and there are different nations like Korea which can be engaged on antitrust actions. The place do you suppose probably the most attention-grabbing issues are taking place outdoors the US and Europe?
I can’t actually decide. I believe there are numerous attention-grabbing issues ongoing. In some jurisdictions they’ve the identical thought, that regulation enforcement in particular circumstances needs to be complemented with regulation. We don’t act as one competitors authority as a result of now we have completely different traditions, variations in laws, completely different instruments that we are able to use, however I discover it actually encouraging that there’s a sense of group in relation to imposing tech circumstances.
On your company particularly — as a result of there may be this totally huge swath of potential circumstances — how do you decide the place you’re going to focus enforcement actions?
Clearly it’s actually essential for us when individuals complain, as a result of that offers us entry to how they see the market state of affairs. Fairly often, they arrive with information that enables us to ask extra certified questions, to search out proof if proof is to be discovered.
We’re additionally actually cautious to scope the circumstances in order that we concentrate on what often is the most dangerous unlawful habits, and that enables us to take advantage of environment friendly use of assets. We hope that the Digital Markets Act will maintain a few of the circumstances we had earlier than, permitting us to concentrate on a few of the points that the Digital Markets Act is not going to take care of — one of many issues can be one thing just like the Jedi Blue case.
You’ve talked about the way you theoretically wish to regulate “the metaverse,” however that it’s nonetheless very early days and also you’re making an attempt to determine what it’s. What would it not take in your company to develop the experience that you’d must go after potential violations there?
Nicely, metaverse or no metaverse, we’re within the course of of adjusting the composition [of our group] so we are able to rent extra individuals who have technical capabilities. We use extra technical digital instruments than we used to — in any other case our work is solely not potential. If we ship a request for data, for instance, you might get thousands and thousands of paperwork and you may solely undergo that many with the assistance of digital instruments. So we’re already in a interval of change and have been for a while. The place that will lead us, I believe nonetheless stays to be seen, nevertheless it’s one thing that should occur earlier than we are saying “now there may be a longtime factor that we might name the metaverse.”
I’m additionally curious the way you’re trying into the cryptocurrency area.
From a contest perspective, it’s early days. My colleague Mairead McGuinness, who’s liable for monetary issues, is in fact watching this very fastidiously. The European Central Financial institution and the completely different nationwide central banks are additionally contemplating making a digital euro — mainly to take again a part of the important financial coverage that means that you can really challenge technique of fee. It’s not a cryptocurrency, it’s an actual official forex, so to talk.
Nevertheless it’s one thing that we observe very carefully, as a result of in relation to issues like fee and financing, it’s actually complicated and fairly often it’s hidden from individuals what they really pay.
Do you see there being potential competitors points within the crypto area? Decentralization is meant to be an enormous aspect of it, however there are forex exchanges and NFT marketplaces which can be turning out to be very near gatekeepers.
Nicely, we haven’t had complaints about it but. So it nonetheless stays to be seen what particular circumstances could develop sooner or later.
I wished to speak in regards to the Digital Providers Act, which is the counterpart to the Digital Markets Act — I’m particularly within the legal responsibility of platforms for unlawful content material. To start out, might you lay out how that works?
The Digital Providers Act addresses each content material and merchandise. In relation to merchandise, platforms would have an obligation to know their enterprise prospects — to ensure that your merchandise are secure, that individuals can come again and complain about them, that they’ve their customers’ rights.
In relation to content material, there are two obligations. First can be to take down issues which can be thought of to be unlawful if flagged, whereas on the similar time ensuring that you would be able to complain if content material of yours is taken down. Second, that firms do a horizontal danger evaluation as as to whether or not their companies could be misused to undermine democracy or put individuals’s psychological well being in danger. If these dangers are being discovered, that you must mitigate them.
In relation to liabilities for the platform themselves, that will solely kick in if individuals could make the belief that it’s really the platform that was behind this. I believe it’s simpler to grasp when it’s bodily merchandise — in case you don’t notice that you just’re coping with a enterprise that’s on a platform, however suppose that it’s really the platform that you just’re coping with, then the platform could assume legal responsibility.
The query about eradicating unlawful content material is a extremely popular matter within the US. There’s a concern that including this requirement goes to guide platforms to over-moderate and take down content material indiscriminately — to say, look, we’d slightly be secure than sorry — and that this would possibly notably have an effect on susceptible teams. And folks won’t absolutely perceive the method of making an attempt to get that content material put again up. How do you see the Digital Providers Act addressing that?
That is precisely why individuals ought to get notified and have an opportunity of getting their put up put again up once more. It’s a tough factor to do, as a result of there’s a grey zone right here the place issues usually are not unlawful, however they might be hurtful for individuals. There could also be conflicts coming from it, nevertheless it’s your proper to say no matter you need, so long as it’s not unlawful. So this is the reason now we have crafted this stability. We expect this may work — due to course over-removal is one thing we are attempting to keep away from.
If one thing just like the Digital Markets Act efficiently reduces the ability of massive gatekeepers and large tech platforms, what impact do you see that having on the opposite tech points like disinformation?
I believe completely different instruments are wanted. My colleague Věra Jourová has been liable for working with platforms based mostly on the EU code of conduct. We’ve simply strengthened the code of conduct and the entire large platforms have signed up for it — TikTok, Google, all the massive ones. I believe the cooperation is sort of good, and it has been important in the course of the pandemic. It’s actually essential for us to not suppose that there’s one silver bullet. To make the digital world a completely built-in a part of our world, many issues must occur on the similar time. And I believe the code of conduct mixed with the regulation creates a stability and that’s most likely the simplest approach to go about it.
I believe there’s a broad understanding that individuals wish to reduce the ability of gatekeepers and have fewer central choke factors for the web, however on the similar time, as we’ve seen with the struggle in Ukraine, the identical individuals depend on these large central gatekeepers to chop off issues they wish to see taken offline, like Russian propaganda. It appears theoretically potential that in case you reduce the ability of those firms, you all of the sudden don’t have these factors the place you possibly can train management over one thing like disinformation. Is that one thing that you just’ve considered?
It’s fairly a particular state of affairs that we’re in, as a result of we see the actions right here as a part of the sanctions — as a result of Russia Right now and Sputnik, they’re fully state-controlled media. So we see them as a part of the struggle machine. And the sanctions are why it really works all around the European Union on the similar time. However I don’t see that there’s a want simply to have a couple of gatekeepers for that to be efficient, as a result of even when there have been many extra shops for these media, they might even be on board to do that.
What are the broader classes that we are able to draw from the digital response to the struggle in Ukraine?
I believe it’s a really previous fact that the primary sufferer in a struggle is fact, as a result of it turns into more and more tough to belief what you’re being instructed. Having social media, in fact, amplifies propaganda and misinformation to a totally completely different diploma than what it was simply 10 years in the past. As horrible as it’s on the bottom for the people who find themselves being shelled, for individuals being bombed, it’s also a struggle about the way you see the struggle. For this reason it’s so essential that now we have good cooperation with the platforms to ensure the propaganda shouldn’t be allowed to stay on them.
For the previous few years, we’ve been going by means of what individuals are dubbing the “techlash.” I’m curious in case you suppose this can be a non permanent second, or if there’s been a everlasting shift that’s put public opinion on a distinct trajectory.
I believe it’s a everlasting shift, as a result of from the very early days of digitization, possibly we didn’t actually discover that it grew to have such an significance in our lives. However the factor was that as our digital world grew, it pushed again on the place our democracy has a say — as a result of the bodily world turned of much less and fewer significance in many individuals’s lives, and what they do on-line takes up numerous hours every single day.
What is going on proper now could be that democracy is coming again in to say, properly, no. Democracy counts within the digital world in addition to the bodily one. It should be that what we agree is illegitimate really is unlawful and is handled as such. And what’s authorized is authorized and handled as such. And that, I believe, is a everlasting factor — that democracy is coming again to have the ability to govern our society when it’s digital.
Thanks, it’s been fantastic speaking to you.
Thanks very a lot for doing this. I admire it.

Technology
A lot of new Copilot Plus PCs will hit shelves starting in June
/cdn.vox-cdn.com/uploads/chorus_asset/file/25456799/lcimg_2c03ed43_c1df_414a_9e67_8100cdf3d526.jpeg)
Acer Swift 14 AI
Not to be confused with the other Swift 14 laptops with AI chips, the Swift 14 AI is the only one with a Qualcomm Snapdragon X series processor. This one comes with either the base 12-core Snapdragon X Elite chip or the 10-core X Plus chip and goes up to 32GB of memory and 1TB of M.2 SSD storage.
Asus Vivobook S 15
Asus is starting its Copilot PC adventure with its Vivobook S 15. It will have two Qualcomm processor options — the base 12-core Snapdragon X Elite and 10-core Snapdragon X Plus — and both options will support 32GB onboard memory and 1TB of PCIe 4.0 SSD.
Dell XPS, Inspiron, and Latitude
Dell is releasing five Copilot Plus PCs with Snapdragon this year, starting with the XPS 13 and Inspiron 14 Plus (7441). The XPS will be configured with a midtier Snapdragon X Elite chip and up to 64GB of memory and 2TB of PCIe SSD storage and will have three display options: two IPS, one touch-enabled; and one OLED that’s also a touchscreen. The OLED will have the highest resolution — but lowest refresh rate — out of the display options.
Meanwhile, the Inspiron will have the Snapdragon X Plus, support up to 32GB of memory and up to 1TB of M.2 2230 SSD storage, and only one display option, an IPS touchscreen. The Dell Latitude 7455 will have both Snapdragon X Elite and Plus options with support for up to 32GB of memory and 1TB of M.2 2230 SSD storage.
HP OmniBook and EliteBook Ultra
Along with HP’s ProBook, its OmniBook and Elitebook have replaced its now-former Envy, Pavilion, and Dragonfly series in a huge renaming effort to clean up and organize HP’s laptop portfolio. The Omibooks will be the consumer-focused devices, while the Elitebooks will be commercial, or business-focused.
HP will start shipping its new OmniBook X AI and EliteBook Ultra AI next month, and their configurations will include a 12-core Snapdragon X Elite processor. The Elitebook only goes up to 16 GB of memory, but the OmniBook can handle up to 32GB.
Lenovo Yoga Slim and ThinkPad
The Lenovo Yoga Slim 7x 14 and ThinkPad 14s will come with Snapdragon X Elite processors. The Yoga Slim will be the cheaper of the two due to the lack of Enterprise features that come with the business-oriented ThinkPad. Both will have OLED displays, but the ThinkPad will support up to 64GB of memory, while the Yoga Slim will support up to only 32GB.
Microsoft Surface Pro and Surface Laptop 6
The first Microsoft device to get its own Copilot Plus treatment is the Surface Pro. You’ll be able to get it with either the Snapdragon X Elite or X Plus processor, optional 5G connectivity, and either an IPS or OLED display.
There’s also the Surface Laptop 6, which also comes with either the Elite or Plus Snapdragon chips, and up to 64GB of memory and 1TB of SSD storage.
Samsung Galaxy Book4 Edge
Samsung’s first three Copilot Plus PCs are all under the name Galaxy Book4 Edge. There’s one 14-inch model and two 16-inch models, all with Snapdragon X Elite processors, 2880 x 1800 AMOLED touchscreens, and 16GB of RAM.
All of these PCs are available for preorder now and will start shipping on June 18th.
Technology
How to know if your computer got hacked, what to do next

Have you ever had that sinking feeling that something’s not quite right with your computer? Maybe it’s running slower than usual or there are new icons on your desktop that you don’t recognize. Well, you might not be just imagining things; you could have been hacked.
While the first reaction may be to panic, the best possible first step if you think you’ve been hacked is to disconnect your computer from the internet and take a deep breath. If you’ve got antivirus software already installed, run the scan immediately. But don’t worry just yet. Before you start fretting about cyberthieves and lost data, let’s take a moment to walk through some crucial steps together. From running a trusty antivirus scan to the nitty-gritty of browser settings and remote access – this is your go-to guide for outsmarting those pesky hackers.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
A woman grabbing her computer in frustration (Kurt “CyberGuy” Knutsson)
Were you hacked?
1. Run antivirus software ASAP
When you’re running any antivirus scans or troubleshooting, start from the actual antivirus software program. Don’t follow pop-ups or notifications. If there is indeed a compromise, it should show up on the dashboard of the antivirus software program.
Preventative:
- Keep your antivirus software updated. Hackers are coming up with new viruses often, so if you are up to date, you’re less likely to be compromised. Or the virus is more likely to get caught.
- Be familiar with your antivirus software notifications and alerts, so if you ever get a pop-up or notification, you’ll be more apt to notice fake ones.
- Write down the contact information of the antivirus software you’ve installed and have it near the computer.
If you feel pretty confident that you’ve unfortunately been hacked, but your antivirus scan comes up empty, take a break and call customer service of antivirus software directly. Do not follow links to have a rep call you. Use the number you’ve written down, and call them directly so you know you’re not being duped.
If you don’t have antivirus software installed, make sure to install one and do a computer scan. You can find our top recommendations here.
ASK ANY TECH QUESTION AND GET KURT’S FREE CYBERGUY REPORT NEWSLETTER HERE

A man typing on keyboard (Kurt “CyberGuy” Knutsson)
HOW TO RECOVER A HACKED FACEBOOK ACCOUNT
2. Reformat or reset to factory settings
Sometimes a virus or other nefarious entities have overrun the computer so badly that you might need to simply reformat or reset it to factory settings. If you’ve uninstalled or deleted suspicious programs or applications only to have them reload upon restarting your computer, you may simply need to start from scratch. This is why it is crucial to have recent backups of your data. Our article, “How to securely get rid of your old PC or Mac,” outlines how to reset to factory settings or reformat your computer.
EXPERT TIPS, LEGIT REVIEWS. GET THE FREE CYBERGUY REPORT NEWSLETTER
3. Delete settings or extensions on browsers or uninstall and reinstall browsers completely
There have been many times I have gone to help my mom with her online accounts, only to be inundated with pop-ups, redirects or random links on her browser bar or menu. It turned out that she had either accidentally downloaded extensions that embedded themselves in the browser or, worse, changed the browser setting to open a spammy website as her main search engine or landing page. You can go to settings or preferences and delete extensions you do not recognize. But if these settings or extensions keep reappearing after deleting and restarting the browser, it is likely a bigger problem. Then, uninstall the browser and see if you can reinstall it. If that brings up the same settings again, then it could be a much more invasive virus or malware that needs to be addressed with an antivirus scan or assistance from a professional.
HOW TO OUTSMART CRIMINAL HACKERS BY LOCKING THEM OUT OF YOUR DIGITAL ACCOUNTS
4. Turn off or restrict remote access
While it is harder for hackers to access your computer if it is completely turned off, if you have allowed remote access, a hacker just needs your computer to be hooked up to a network or the internet in order to take over your device and turn it on.
To prevent remote access to your PC:
- Click the Windows Start button
- Input Remote Desktop settings in the search bar
- In the Remote Desktop settings, ensure that the slider under “Enable Remote Desktop” is set to Off.
- Review your current processes in Task Manager (Ctrl+Alt+Del) for any unusual or suspicious activities
To prevent remote access on Macs:
- Click the Apple logo icon in the top left corner.
- Click System Settings
- Tap General
- Click the Sharing icon
- Scroll down and uncheck the boxes next to Remote Login and Remote Management to prevent unauthorized remote access.

A woman on her laptop (Kurt “CyberGuy” Knutsson)
HOW HACKERS CAN CRAFT AN ATTACK FROM YOUR SOCIAL MEDIA PROFILE
5. Review your activity monitor on your computer and network traffic patterns
Periodically, checking your computer’s activity monitor to check which programs are running and what is using up the most bandwidth is a healthy practice. It will teach you to spot any programs or traffic that is unusual or if someone else is connecting to your computer remotely.
To review this activity on your PC:
- Go to Control Panel
- Click Administrative Tools
- In Event viewer, look for the events that are related to startup and shutdown. Any shutdown will be listed there and which program or user-initiated that startup or shutdown. This way, you can see if these actions are that of a virus or an update process.
To review this activity on your Mac:
- Go to the menu bar on the top left when you first log on to your account.
- Select Go
- In the drop-down menu, select Utilities
- When a menu pops up, one of the first options should be Activity Monitor.
Or:
- Go to your Applications folder on your dock (usually located on the bottom or right-hand side of the screen)
- Go to Utilities folder
- Select Activity Monitor

A man putting in his username and password on tablet (Kurt “CyberGuy” Knutsson)
Top 3 preventative measures to not get hacked
1. Turn on 2-factor authentication
While it may seem like a pain to enter a code received via email or text each time you sign in, this extra step is crucial for security. By activating two-factor authentication, you create a barrier against unauthorized access. Even if a hacker discovers your email or username, they won’t get far without the unique code.
Each login attempt triggers a notification, alerting you to potential threats. Repeated failed attempts will secure your account by either locking it or sending you an alert. In the event of suspicious activity, you can swiftly use a trusted device to reset your password and inform the service provider. It’s a small price to pay for significant protection against cyberthreats.

A man backing up his computer (Kurt “CyberGuy” Knutsson)
2. Have strong antivirus software
The best way to protect yourself from clicking malicious links that install malware in an attempt to get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams. Plus, think of it like having a digital bodyguard – always on the lookout, always ready to defend you from cyberthreats. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
3. Configure your email settings
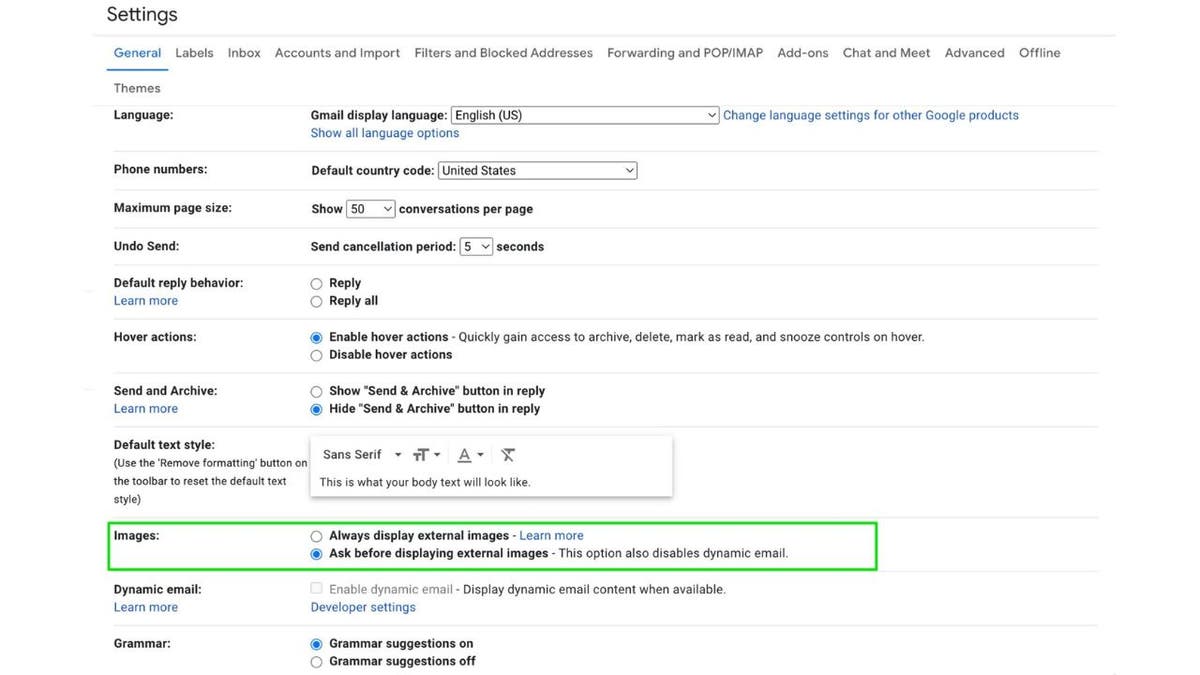
Configure email settings to not automatically images or attachments (Kurt “CyberGuy” Knutsson)
If you configure your email settings to not automatically load content such as images or attachments, then it is harder for viruses or other malware to be automatically downloaded or accidentally opened. If you also have emails received first in rich text format, you can choose which emails load fully with images once you realize it is from a trusted source.
Gmail desktop:
- Click the settings gear icon
- Choose See all settings
- Under the General tab, scroll to the Images section.
- Select Ask before displaying external images
- Scroll to the bottom of the page and click Save Changes
Gmail mobile:
- Tap the hamburger menu (3 horizontal lines)
- Select Settings
- Choose the account you want to manage
- Scroll to the Images section and select Ask before displaying external images.
Apple mail:
- First, click on Mail in your dock at the bottom of your screen
- Then click on Mail in the upper left of your screen
- Click Settings
- Go to the Viewing tab
- Uncheck Load remote content in messages
Outlook desktop (PC):
- Click File
- Choose Options
- Select Trust Center
- Click Trust Center Settings
- Under Automatic Download, check the option that says Don’t download pictures automatically in standard HTML email messages or RSS items.
Outlook desktop (Mac):
- Open Outlook
- Click Preferences
- Under Email select Reading
- Choose Security
- Select Never to prevent image downloads
Yahoo Mail desktop:
- Click Settings.
- Choose More Settings.
- Click Viewing email.
- Under Show images in messages, select Ask before showing external images.
Start Mail desktop:
Please note that the exact wording of the menu items and options can vary based on the version of Start Mail you are using.
- Open Start Mail
- Click on the Settings icon
- Navigate to the Email section
- Look for the Images or Privacy settings
- Choose the option to Ask before displaying external images or a similar setting that controls the automatic downloading of pictures.
These steps should help enhance your email security by giving you control over which images are displayed, thereby reducing the risk of malware being automatically downloaded or opened. Always ensure your email application is updated to the latest version for the best security practices.
Looking for private and secure email solutions? See Best Private and Secure Email Providers 2024
QUICK TIPS. EXPERT INSIGHTS. CLICK TO GET THE FREE CYBERGUY REPORT NEWSLETTER
Data recovery: Protecting your information against loss
This may not seem relevant to an article about hacking, but having your data off your computer and safely on an external hard drive or the cloud will give you more options if you think you’ve been hacked. If you need help deciding what type of data backup would be best for you, please take a look at these articles:
If a hack is bad enough, sometimes a complete wipe of your system is the only way to salvage your computer. If you have a safe copy of your data, while it might be inconvenient, you will not lose all your data. Also, if you keep more sensitive data off your more frequently used computer, then your data is less likely to be compromised if you get hacked.
Kurt’s key takeaways
At the end of the day, being hacked is a massive inconvenience and can potentially lead to data loss or theft. But don’t lose hope. There are steps you can take to outsmart those pesky hackers and keep your devices secure. The key is staying vigilant and taking preventative measures like using strong antivirus software, enabling two-factor authentication and regularly backing up your data. That way, if you do get hacked, you’ll have a recent backup to rely on and can simply wipe your device clean without losing everything.
It’s also crucial to keep an eye out for any suspicious activity on your computer or network. If something seems off, don’t hesitate to run a full antivirus scan and review your activity monitor for any unauthorized access or programs running in the background. Remember, hackers are always coming up with new tricks, so it’s an ongoing battle to stay one step ahead. But by following the tips outlined here, you’ll be well on your way to keeping your digital life secure and hack-free. Stay vigilant, my friends.
Can you share a personal story where being proactive about computer security paid off or, conversely, where neglecting it led to issues? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on Facebook, YouTube and Instagram.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Apple’s next AirTag could arrive in 2025
/cdn.vox-cdn.com/uploads/chorus_asset/file/22461385/vpavic_4547_20210421_0067.jpg)
You may not have even thought about replacing your AirTag yet, but Bloomberg reports that Apple is working on a new one that could arrive in mid-2025. The new AirTag will reportedly feature an updated chip with better location tracking — an improvement it might need as competition among tracking devices ramps up.
By the time Apple rolls out its refreshed AirTag, the Bluetooth tracking landscape will look a lot different on both Android and iOS. Last month, Google revealed its new Find My Device network, which lets users locate their phones using signals from nearby Android devices. Even Life360, the safety service company that owns Tile, is creating its own location-tracking network that uses satellites to locate its Bluetooth tags.
In last week’s iOS 17.5 update, Apple finally started letting iPhones show unwanted tracking alerts for third-party Bluetooth tags. If an unknown AirTag or other third-party tracker is found with an iPhone user, they’ll get an alert and can play a sound to locate it. The feature is part of an industry specification created to prevent stalking across iPhones and Android devices. Several companies that make Bluetooth tracking devices, including Chipolo, Pebblebee, and Eufy are on board with the new standard.
-

 News1 week ago
News1 week agoSkeletal remains found almost 40 years ago identified as woman who disappeared in 1968
-

 World1 week ago
World1 week agoIndia Lok Sabha election 2024 Phase 4: Who votes and what’s at stake?
-

 Movie Reviews1 week ago
Movie Reviews1 week ago“Kingdom of the Planet of the Apes”: Disney's New Kingdom is Far From Magical (Movie Review)
-

 World1 week ago
World1 week agoUkraine’s military chief admits ‘difficult situation’ in Kharkiv region
-

 Politics1 week ago
Politics1 week agoTales from the trail: The blue states Trump eyes to turn red in November
-

 World1 week ago
World1 week agoBorrell: Spain, Ireland and others could recognise Palestine on 21 May
-

 World1 week ago
World1 week agoCatalans vote in crucial regional election for the separatist movement
-

 Politics1 week ago
Politics1 week agoNorth Dakota gov, former presidential candidate Doug Burgum front and center at Trump New Jersey rally













