Technology
A beginners guide to cookies

Cookies could sound deliciously interesting on the floor. Permitting cookies in your units and browser have a candy facet and occasional bitter aftertaste if not managed correctly.
First, the fundamentals of how cookies work with browsers will go a protracted strategy to serving to know when to simply accept or reject them.
Whereas cookies are designed within the hopes of supplying you with a extra pleasurable looking or browsing expertise, many have feared that accepting cookies means that you’re willingly gifting away your private info, and making your self susceptible to hackers and malware. However is that this true?
SPAM TEXTS ARE OUT OF CONTROL, SAY ALL 51 ATTORNEYS GENERAL
Cookies are textual content recordsdata, that are used to gather information.
What precisely are cookies?
In a nutshell, cookies are textual content recordsdata which might be used to gather information. Cookies start storing info upon your connection to the web site, labeling your information with an ID uniquely associated to your laptop. This enables the web site to collect info distinctive to you and your earlier exercise on the web site.
Web sites use cookies primarily to make your internet looking expertise extra pleasurable by monitoring the way you used the web site. Should you return, they will promote and show issues based mostly in your earlier go to by recognizing your laptop.
For instance, should you visited a web based retailer, in your subsequent go to, the web site can promote objects they suppose you would possibly like based mostly on what you beforehand considered or bought. Most web sites additionally use cookies as a way of creating their web site extra navigable and accessible to the broader public.
How precisely do cookies work
10 TRICKS FOR DOING AN EFFECTIVE GOOGLE SEARCH
- As soon as you go surfing to a web site, your internet server transfers the cookie to your browser
- Your laptop then shops the cookie in your exhausting drive.
There are three main kinds of cookies you’ll probably come throughout whereas browsing the web:
- Persistent Cookie
- These cookies retailer information for an prolonged interval
- They arrive with an expiration date, wherever from just a few days to some years after your first go to
Session Cookies
- Session cookies final solely so long as your browser is open
- When you shut your browser, all your info might be deleted.
Third-Get together Cookies
- Also referred to as “monitoring cookies”, these cookies monitor your wider on-line conduct
- Data collected from a single web site go to is shared with advertisers
- This advertiser will then be capable of promote objects in your social media based mostly in your looking historical past.

Cookies are textual content recordsdata, that are used to gather information.
(Cyberguy.com)
When cookies develop into issues
TECH TIP: THE 6 TOP-EXPERT-REVIEWED MODEMS
The potential to your looking historical past and different delicate info to be simply tracked poses a privateness and safety threat. Specifically, they gather numerous your private info, together with your IP deal with, looking historical past, and may you’ve gotten been tracked by third-party cookies, your info may be bought to advertisers who will then goal you.
Cookies aren’t resistant to cyberattacks. A extra harmful situation is when your laptop or machine is just not secured with sturdy passwords and up-to-date safety software program. This info might doubtlessly be accessed by cybercriminals who’re expert at prying into cookies that retailer bank cards, monetary login credentials, and different delicate info.
If privateness and safety weren’t regarding sufficient, there’s additionally a threat {that a} cookie might trigger issues with web site efficiency. This will occur when you’ve gotten a lot of cookies saved in your machine inflicting the browser you employ to expertise a slowdown.
When ought to I not permit cookies?
Many web sites won’t permit you to entry them with out accepting cookies. And so long as it’s a safe, trusted web site, permitting cookies enabled ought to pose no menace. If a web site you go to appears unusual or untrustworthy, you shouldn’t permit cookies. One simple method of figuring out that is by checking the web site deal with in your browser. Ensure that there’s a lock originally of the URL deal with. Which means all information on the web site is encrypted.
You could at occasions be prompted to allow or settle for third-party cookies. These are the kind of cookies that concentrate on you essentially the most. It is most likely greatest to say no to simply accept third-party cookies if you wish to be further cautious since you don’t have any management over the place your info would possibly find yourself.
SEND A FUN MESSAGE WITH THESE IPHONE TRICKS
Is it doable for me to handle my cookies?
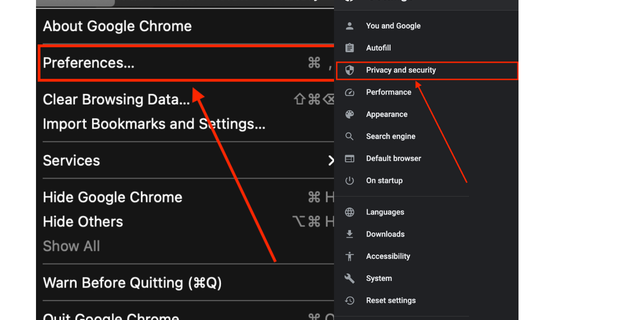
Fortunately, Google Chrome like many browsers has a straightforward method so that you can handle saved cookies:
- Click on the Chrome Menu
- Click on Preferences
- Click on Privateness And Safety
Cookies are textual content recordsdata, that are used to gather information.
(Cyberguy.com)
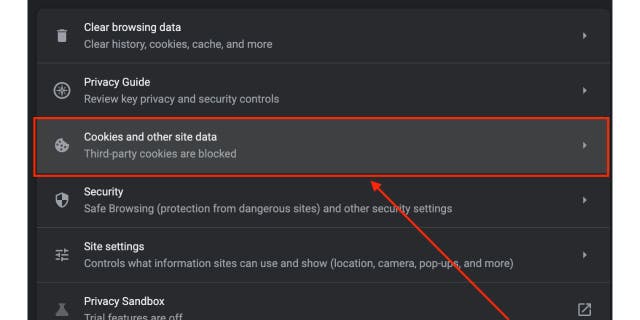
- Click on Cookies and Different Web site Knowledge
Cookies are textual content recordsdata, that are used to gather information.
(Cyberguy.com)
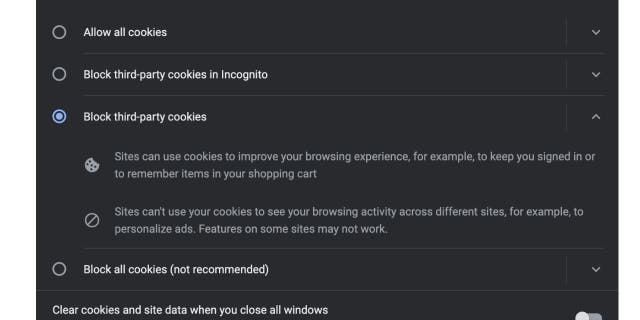
Right here you should have a number of choices, together with whether or not to dam all cookies.
Cookies are textual content recordsdata, that are used to gather information.
(Cyberguy.com)
HOW TO FIND YOUR LOST MACBOOK
Blocking all cookies is not really helpful as it would make accessing sure web sites unimaginable and make logging into web sites you go to continuously much less handy. Blocking third-party cookies prevents your looking exercise throughout a number of websites to be recorded simply.
Methods to maintain your personal info secure
Whereas your info on encrypted websites is the most secure, significantly when you’ve got third-party cookies blocked, we nonetheless would possibly discover ourselves unintentionally permitting cookies on an unsafe web site. That immediately places our on-line security in danger. There are two perfect methods to maintain your self protected ought to this occur to you.
Use a VPN
A digital personal community, or VPN, hides your IP deal with by re-routing your information by an encrypted tunnel. This makes your on-line and browser historical past subsequent to unimaginable to trace. I select ExpressVPN as the perfect VPN. Advantages of a VPN embody:
CLICK TO GET KURT’S CYBERGUY NEWSLETTER WITH QUICK TIPS, TECH REVIEWS, SECURITY ALERTS AND EASY HOW-TO’S TO MAKE YOU SMARTER
- provides a layer of enhanced safety
- prevents Web service suppliers from monitoring your on-line exercise
- affords a method round geo-fencing blocks
- will help enhance your connection speeds
Restricted time deal for CyberGuy readers for extra of my evaluation go to CyberGuy.com/VPN
Set up trusted antivirus software program for safer looking
Having dependable antivirus safety operating in your laptop is greatest at warning you if a web site you might be visiting is reliable or not earlier than you might be even in a position to give your private info to an untrustworthy website.
One of many high antivirus apps for all units together with each Android and iPhone is TotalAV. Their product is filled with options to maintain you secure from malware and defend you when looking the web together with ransomware safety, real-time antivirus safety, elimination of viruses and malware, a device to unencumber your laptop’s house, plus extra.
It is price a small worth to pay to maintain your private info, information, and all your units secure from hackers.
See my skilled evaluation of the perfect antivirus safety by looking out ‘Finest Antivirus’ at CyberGuy.com.

Technology
Twitter is officially X.com now
/cdn.vox-cdn.com/uploads/chorus_asset/file/24805888/STK160_X_Twitter_006.jpg)
The social network formerly known as Twitter has officially adopted X.com for all its core systems. That means typing twitter.com in your browser will now redirect to Elon Musk’s favored domain, or should. At the time of publication, we’re seeing a mix of results depending upon browser choice and whether you’re logged in or not.
A message also now appears at the bottom of the X login page that reads, “We are letting you know that we are changing our URL, but your privacy and data protection settings remain the same.”
Musk has a long history with the x.com URL, launching a business under the name in 1999 that eventually merged with what would become PayPal. For this modern-day version of the company, Musk envisions that it will become a WeChat-like “everything app.”
Maybe, but one thing’s for sure: it’s not Twitter anymore.
Technology
Keyless car theft is on the rise. This is how to protect yourself.

- Using a relay device, car thieves can amplify the signal from your wireless key fob, even if it is inside your house, and use it to unlock your car.
- Storing your key fob in a Faraday bag or using a physical steering wheel lock can help guard you from car theft.
- As technology evolves, so do criminal methods. Staying current on information is another important way to protect yourself.
They appear like ghosts in the night, standing outside your house, one holding up an antenna while the other crouches next to the car parked on the driveway. Within seconds, your car is gone, yet another victim amid a surge in auto theft enabled by the technology designed to make it easier to unlock and start vehicles.
Auto technology has evolved and many newer cars use wireless key fobs and push-button starters instead of traditional metal keys. The fob sends a short-range signal, so when the driver approaches the car, it automatically unlocks the door. This saves you the hassle of digging out your keys when you’ve got your hands full with groceries.
But that technology also makes things easier for thieves. The wireless fob will continue to emit a signal even if you’re not using it. Thieves prowl neighborhoods at night looking for cars parked outside so they can carry out so-called relay attacks. Using portable equipment that can pick up the faint signal from a fob inside the house or parking lot, they relay it back to a transmitter that can clone the signal.
NEW TREND OF ‘BURGLARY TOURISM’ ON THE RISE
Officials have urged carmakers to reduce the security vulnerabilities and warn owners about the risks.
So what can you do to reduce the odds that your car will be gone in 60 seconds? “It’s relatively easy for drivers to protect themselves,” said Steve Launchbury, principal engineer of automotive security at Thatcham Research, a U.K.-based automotive risk intelligence company. Here are some tips:
USE A SIGNAL BLOCKER
A simple but effective way to stop auto bandits from purloining your key fob signal is to use a Faraday bag or pouch. They’re lined with a conductive metal mesh that blocks the transmission of electromagnetic signals.
Metropolitan Police Department Sgt. Anthony Walsh sets out steering wheel locks at an anti-crime event in Washington on Nov. 7, 2023. A physical lock that attaches to the steering wheel can act as a visible deterrent to car thieves. (AP Photo/Amanda Andrade-Rhoades, File)
The pouches aren’t expensive, and you can also get boxes that do the same thing. But experts advise testing to make sure they work. Just put the key fob inside and approach your car. If the doors don’t automatically unlock, then the signal is being blocked.
It’s also important to remember to use it whenever you leave your vehicle, and don’t forget to put all of your key fobs inside, including any spares.
But ignore some advice making the rounds on the internet telling you to put your fob in the microwave or freezer. It doesn’t have the same effect as a Faraday bag, and you risk damaging your key.
GET AN OLD-FASHIONED LOCK
Try an old-school solution by using a physical lock. Some police forces advise car owners to use them to make your vehicle look less tempting to steal. The reasoning is that a would-be thief might be deterred by the effort needed to cut through the lock and instead turn their attention to an easier target.
Locks, in the shape of a disk or a long bar, clamp onto the steering wheel and make it difficult to steer. There are also versions that prevent the car from being put in gear. The downside is you’ll need extra time to attach or remove it whenever you aren’t driving.
CHANGE UP YOUR SETTINGS
For many cars, it’s possible to deactivate the wireless setting so that you can’t open the door remotely. For Fords, Hondas and Audis, use the touchscreen menus. If you own a Toyota, you can temporarily disable the signal by holding down the fob’s lock button and at the same time pressing the unlock button twice. If you’ve done it correctly, the fob’s indicator light should blink four times. Be aware that the next time you press any button, remote unlocking will be reactivated.
The method will vary depending on make and model so consult your owner’s manual for the exact process. If it sounds complicated, there are YouTube videos that walk you through it. Don’t forget that in most cases you’ll now have to manually press the fob’s unlock button.
Automakers have started adding motion sensors to key fobs. If the sensor doesn’t detect recent movement because it’s been, say, left on the kitchen counter after you come home, the fob goes into sleep mode and stops transmitting. If it lacks this capability, check with your dealer whether it’s possible to upgrade it.
If you buy a used car, some experts also advise getting the keys reprogrammed, just in case the previous owner kept one of the fobs.
WATCH OUT FOR NEW METHODS
Researchers have uncovered a new auto theft technique that doesn’t target radio signals. The controller area network, or CAN, is “a feature of modern cars which allows different components and systems to communicate, (and) has recently been targeted and exploited by thieves,” said Thatcham’s Launchbury.
The network allows sensors and control modules to talk to each other directly, instead of going through a central node. Thieves take advantage by accessing the network from the car’s exterior, usually by removing a headlight and connecting a device that can “inject” a signal, tricking the car into unlocking and starting.
While automakers work on improving CAN security, “there are steps drivers can take today to add layers of security and deter criminals,” such as using a physical lock, Launchbury said.
Aftermarket electronic immobilizer systems “should render a criminal’s theft tool useless,” and might even get you a discount on auto insurance, he said. Thatcham and other companies offer them but the downside is they can be quite pricey.
Technology
iMessage had an outage, but now it’s back
/cdn.vox-cdn.com/uploads/chorus_asset/file/24401979/STK071_ACastro_apple_0002.jpg)
On Thursday evening, many iPhone owners (including some here at The Verge) saw the “not delivered” flag when trying to send texts via iMessage. People reported the problem across multiple wireless carriers (Verizon, AT&T, and T-Mobile), countries, and even continents.
The Apple services status page didn’t show any indication of trouble while the problems were going on, but now it has been updated after the fact, reflecting a resolved issue where “Users were unable to use this service” for iMessage, Apple Messages for Business, FaceTime, and HomeKit. According to the note, the problems went on from about 5:39PM ET until 6:35PM ET.
Apple has not responded to inquiries or otherwise commented on the issue; however, judging by our use and reports on social media, everything seems to be up and running again. However, if your international friends are still saying, “Just use WhatsApp!” there isn’t really anything we can do about that.
Update, May 16th: Noted the issue appears to be resolved.
-

 Politics1 week ago
Politics1 week ago'You need to stop': Gov. Noem lashes out during heated interview over book anecdote about killing dog
-

 News1 week ago
News1 week agoMan, 75, confesses to killing wife in hospital because he couldn’t afford her care, court documents say
-

 Politics1 week ago
Politics1 week agoRFK Jr said a worm ate part of his brain and died in his head
-

 World1 week ago
World1 week agoPentagon chief confirms US pause on weapons shipment to Israel
-

 Politics1 week ago
Politics1 week agoHere's what GOP rebels want from Johnson amid threats to oust him from speakership
-

 World1 week ago
World1 week agoPro-Palestine protests: How some universities reached deals with students
-

 World1 week ago
World1 week agoConvicted MEP's expense claims must be published: EU court
-

 Politics1 week ago
Politics1 week agoCalifornia Gov Gavin Newsom roasted over video promoting state's ‘record’ tourism: ‘Smoke and mirrors’















