Crypto
Bitcoin exchange exec admits he ignored anti-laundering laws

A California man has admitted he failed to bake anti-money laundering protections into his cryptocurrency exchange, thus allowing scammers and drug traffickers to launder millions of dollars through the service.
Charles James Randol, 33, who is now due to be sentenced, faces a maximum of five years in federal prison and three years supervised release, plus a fine of up to $250,000 or twice the total illicit proceeds from the scams, whichever amount is greater.
According to an agreement [PDF] with prosecutors to plead guilty, Randol said he operated a virtual-currency money company called Bitcoins4Less, and later Digital Coin Strategies, between October 2017 and July 2021. The business offered cash for Bitcoin and vice versa, with Randol collecting a commission on the payouts.
Randol provided cryptocurrency exchange services in various ways, including via the post, ATMs, and occasionally in person, prosecutors told a Los Angeles federal court on Tuesday. The Santa Monica man would handle crypto-cash transactions exceeding $10,000 without knowing who his customers were – folks known only as “Puppet Shariff,” “White Jetta,” “Aaavvv,” “Aaaa,” and “Yogurt Monster,” for example – which is hardly in line with regulatory requirements.
To stay on the right side of American law, Randol should have verified and recorded their identities.
In his plea agreement, the cryptocurrency dealer admitted to three in-person transactions between October 2020 to January 2021 in which he gave an undercover FBI agent a total of $273,940 in cash for Bitcoin, and kept a four percent commission fee.
Randol “did not request a name, proof of identity, social security number, or any other information about [the undercover agent] or the source of the funds being exchanged,” the plea agreement says.
The business man also operated a network of automated kiosks in Southern California that converted cash to crypto, or Bitcoin to cash. And he used snail mail for his operation: unknown individuals mailed “large amounts of US currency” to his post office boxes, and Randol conducted Bitcoin-for-cash transactions for these shady individuals, too.
“Additionally, when defendant received the packages, the cash was often packaged in a suspicious manner, including inside hidden children’s books, concealed inside fake birthday or holiday presents, buried within puzzle pieces, or wrapped within multiple magazines,” the court documents say.
FBI agents interviewed Randol about fraud proceeds that had been mailed to his post office boxes in June 2019. Two days later, Randol told a customer he was taking a “hiatus” from converting cash parcels into cryptocurrency because he “ran into an issue” with the Feds. Shortly after, however, Randol agreed to exchange $10,000 in cash for Bitcoin for this same anonymous punter.
Regulations are what brought him down
Randol advertised his services on his website, and third-party sites like localbitcoins.com, which court documents say “falsely represented that Digital Coin Strategies was ‘a fully compliant FinCEN registered money services business.’”
FinCEN, or the Financial Crimes Enforcement Network, is the US regulatory body that ensures money services businesses comply with the Bank Secrecy Act. The federal law requires such firms develop and maintain an anti-money laundering program, file reports for exchanges of currency larger than $10,000, conduct due diligence on customers, and file suspicious activity reports intended to prevent money laundering and other financial crimes.
“In truth, and as detailed below, defendant intentionally and willfully failed to comply with his obligations under the Bank Secrecy Act,” according to the plea agreement.
Specifically, Randol failed to collect “appropriate information” about his customers, file transaction reports, and notify the government of “repeated” suspicious transactions.
His biz had a written anti-money laundering policy “to prohibit and actively prevent money laundering and any activity that facilitates money laundering or the funding of terrorist or criminal activities,” that said Digital Coin Strategies would take the above-mentioned actions to comply with the federal law.
Of course, the firm did not take any of these measures to prevent money laundering.
Randol did hire a compliance officer in September 2020, but he ignored this executive’s advice to stop using accounts labeled “test” for customer transactions on Bitcoin kiosks. This person also warned Randol that his in-person transactions increased his risk of running afoul of the law, but Randol ignored that tip, too.
Although the plea agreement was filed on Tuesday, Randol will formally plead guilty to the charge in court at some point during the next few weeks. ®

Crypto
Bitget Launchpool to List DeLorean (DMC), Offering 66 Million Tokens in Rewards – Branded Spotlight Bitcoin News

Crypto
CoinMarketCap briefly hacked to drain crypto wallets via fake Web3 popup

CoinMarketCap, the popular cryptocurrency price tracking site, suffered a website supply chain attack that exposed site visitors to a wallet drainer campaign to steal visitors’ crypto.
On Friday evening, January 20, CoinMarketCap visitors began seeing Web3 popups asking them to connect their wallets to the site. However, when visitors connected their wallets, a malicious script drained cryptocurrency from them.
The company later confirmed threat actors utilized a vulnerability in the site’s homepage “doodle” image to inject malicious JavaScript into the site.
“On June 20, 2025, our security team identified a vulnerability related to a doodle image displayed on our homepage. This doodle image contained a link that triggered malicious code through an API call, resulting in an unexpected popup for some users when visited our homepage,” reads a statement posted on X.
“Upon discovery, We acted immediately to remove the problematic content, identified the root cause, and comprehensive measures have been implemented to isolate and mitigate the issue.”
“We can confirm all systems are now fully operational, and CoinMarketCap is safe and secure for all users.”
Cybersecurity firm c/side explained that the attack worked by the threat actors somehow modifying the API used by the site to retrieve a doodle image to display on the homepage. This tampered JSON payload now included a malicious script tag that injected a wallet drainer script into CoinMarketCap from an external site named “static.cdnkit[.]io”.
When someone visited the page, the script would execute and display a fake wallet connect popup showing CoinMarketCap branding and mimicking a legitimate Web3 transaction request. However, this script was actually a wallet drainer designed to steal connected wallets’ assets.
“This was a supply chain attack, meaning the breach didn’ target CMC’s own servers but a third-party tool or resource used by CMC,” explains c/side.
“Such attacks are hard to detect because they exploit trusted elements of a platform.”
More details about the attack came later from a threat actor known as Rey, who said that the attackers behind the CoinMarketCap supply chain attack shared a screenshot of the drainer panel on a Telegram channel.
This panel indicated that $43,266 was stolen from 110 victims as part of this supply chain attack, with the threat actors speaking in French on the Telegram channel.
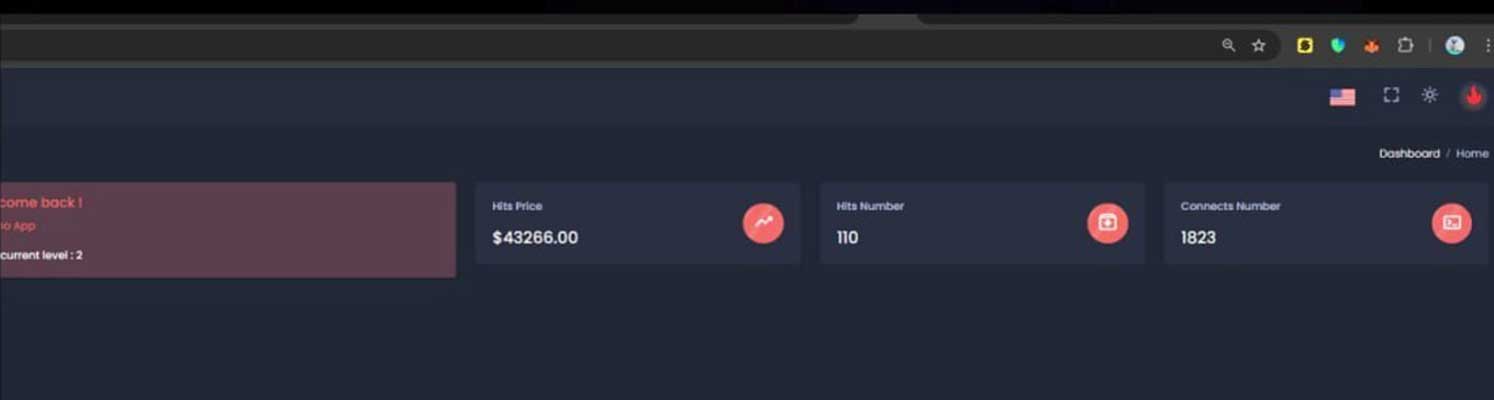
Source: Rey
As the popularity of cryptocurrency has boomed, so has the threat from wallet drainers, which are commonly used in attacks.
Unlike traditional phishing, these types of attacks are more often promoted through social media posts, advertisements, spoofed sites, and malicious browser extensions that include malicious wallet-draining scripts.
Reports indicate that wallet drainers stole almost $500 million in 2024 through attacks targeting more than 300,000 wallet addresses.
The problem has become so pervasive that Mozilla recently introduced a new system to detect wallet drainers in browser add-ons uploaded to the Firefox Add-on repository.

Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work — no complex scripts required.
Crypto
Meta Earth Network 2.0: Pioneering Web3 Innovation With Rewards and Global Events – Press release Bitcoin News

-

 Arizona5 days ago
Arizona5 days agoSuspect in Arizona Rangers' death killed by Missouri troopers
-

 News1 week ago
News1 week agoAt Least 4 Dead and 4 Missing in West Virginia Flash Flooding
-

 Movie Reviews1 week ago
Movie Reviews1 week agoTitan: The OceanGate Disaster Movie Review: A sobering deep dive into ambition, negligence, and tragedy
-

 News1 week ago
News1 week ago‘No Kings’ demonstrators to gather across Greater Cincinnati in opposition to Trump
-

 News1 week ago
News1 week agoOakland County sheriff urging vigilance after shootings of 2 Minnesota lawmakers
-

 Health1 week ago
Health1 week agoHairstylists and medical expert confirm temporary hair loss affecting Ozempic users
-

 Culture1 week ago
Culture1 week agoBook Review: “The Möbius Book, by Catherine Lacey
-

 Technology1 week ago
Technology1 week agoInside Mark Zuckerberg’s AI hiring spree














