Technology
Shortcuts, Hotkeys, Macros, Oh My: How to Remap Your Keyboard

The usual Home windows keyboard structure hasn’t modified a lot up to now few many years, however there’s an opportunity you do not use each key in your keyboard. When you suppose the Caps Lock key would work higher as one thing else, or want you might open up Home windows’ Job Supervisor with one keystroke as a substitute of three, there are a number of methods to remap these instructions.
Because of quite a lot of free software program choices, you’ll be able to set particular person keys to new features or remap complicated button combos into simplified single-button presses. The choice you select comes all the way down to your consolation degree coping with third-party software program and the way complicated your resolution must be.
Remap Keys and Shortcuts With PowerToys
Do not belief a third-party developer? The simplest strategy to remap your keyboard is thru Microsoft PowerToys, a set of utilities (together with keyboard customization) designed for energy customers. Set up this system from its GitHub web page(Opens in a brand new window) and open the Energy Toys Settings web page from the Home windows System Tray.
Click on Keyboard Supervisor, then choose Remap a key to re-assign particular person keys or Remap a shortcut to assign hotkey combos to a single key. Click on the + button, then set the important thing and map it to a selected motion. So as a substitute of hitting Ctrl + C to repeat, you’ll be able to assign that shortcut to the left Alt button in your keyboard.
Add as many remapped keys or shortcuts as you want, then click on OK on the prime of the web page to save lots of the modifications. When you ever wish to take away any, simply click on the trash can icon subsequent to the itemizing and delete it.
Swap Particular person Keys With SharpKeys

SharpKeys
When you merely wish to remap one key to a different, SharpKeys(Opens in a brand new window) is a straightforward, open-source program that makes use of the Home windows registry. This makes it the best choice for these sorts of one-to-one key remappings. You needn’t depend on another software program as a intermediary, and you will run into the fewest compatibility points, since Home windows itself is deciphering the keystrokes.
Obtain this system from the Microsoft Retailer(Opens in a brand new window) and begin it up. To remap a key, click on the Add button and select your keys from the 2 columns. The left column denotes the important thing you will press (for instance, the Caps Lock key) and the fitting column denotes the motion that key will take (for instance, appearing because the Home windows key).
You may as well press the Sort Key button and press a key in your keyboard if in case you have hassle looking it down within the record. If you’re accomplished, click on OK. Repeat this course of for some other remappings, then click on the Write to Registry button. For example, I exploit SharpKeys to make my Alt key act because the Ctrl key, and my Caps Lock act because the Home windows key.
Shut this system, restart your laptop, and you must discover your keys have taken on their new roles. You may even delete SharpKeys once you’re accomplished; this system is merely a user-friendly interface for the Home windows registry, so as soon as the modifications are made, you do not want it anymore.
Customise Hotkeys With Your Keyboard’s Software program

Logitech’s Gaming Software program
In case your keyboard comes with superior software program, like Logitech’s Gaming Software program(Opens in a brand new window), Corsair’s iCUE(Opens in a brand new window), or Razer’s Synapse(Opens in a brand new window), you’ll have some key-remapping options already current in your system.
Not solely are you able to remap keys, however many of those packages allow you to create multi-key shortcuts, insert blocks of textual content, or create totally different profiles for every of your video games. Some will even allow you to report macros, permitting you to create complicated shortcuts simply by recording your actions and assigning them to a hotkey.
Every of those packages are a bit totally different, so we won’t go into all of them right here, however the gist ought to be the identical throughout producers: Obtain the software program, choose your keyboard, and search for the choice to create new hotkeys, macros, or actions. When unsure, test the assist web page to your particular keyboard to search out tutorials on the right way to get it accomplished.
Your mileage might fluctuate with these, as I’ve discovered sure packages to be jankier than others up to now. But when you have already got it in your system, it could possibly do precisely what you need with out putting in some other software program, so give it a shot.
Create Advanced Scripts With AutoHotkey

AutoHotkey
If neither of the above choices fit your wants, you’ll be able to create highly effective hotkeys with AutoHotkey(Opens in a brand new window), a free program that comes with its personal little scripting language so that you can describe the actions you need your hotkeys to take. It’s kind of tougher to make use of than the software program you get with gaming keyboards, but when your keyboard would not include its personal remapping program, it is your subsequent finest guess.
After putting in AutoHotkey, create your hotkeys by right-clicking wherever in File Explorer and selecting New > AutoHotkey Script. Proper-click on the ensuing file and open it in Notepad. Create primary hotkeys by including a line like this:
Capslock::LWin
This remaps Caps Lock to the fitting Home windows key. You may add a remark above it utilizing a semicolon (;) to remind you of what that hotkey does or why.
SharpKeys is a more sensible choice for a easy remapping like this, however as an example you needed to do one thing barely extra difficult, like remap remap Ctrl + Shift + Esc to Caps Lock, so you’ll be able to see the Job Supervisor with one keypress. You’d create a line in your script like this:
Capslock::^+Escape
The place ^ corresponds to Ctrl and + to Shift, as described right here(Opens in a brand new window).
That is the place AutoHotkey turns into extra highly effective. You may create hotkeys to sort sure strains of textual content(Opens in a brand new window), run a program or batch file(Opens in a brand new window), or create shortcuts for particular packages(Opens in a brand new window). You may even have one hotkey carry out a number of actions in a collection, providing you with sturdy management over your shortcuts.
As soon as you have completed including your hotkeys to the script, save the file and double-click on it. It will launch AutoHotkey within the system tray, and it’ll run within the background deciphering your hotkeys for you. Simply stop this system at any time to set your keys again to their default actions.
(I like to recommend including your .ahk script to Home windows’ startup folder, situated at %APPDATApercentMicrosoftWindowsStart MenuProgramsStartup, so it is going to mechanically run each time you flip in your laptop.)
There’s extra to AutoHotkey than we might ever match into one small article, so try the AutoHotkey documentation(Opens in a brand new window) and boards(Opens in a brand new window) for extra superior directions and concepts. When you can think about it, there’s virtually definitely a strategy to make AutoHotkey do it.
Reassign Easy Shortcuts on a Mac Keyboard

If you wish to customise current keyboard shortcuts on a Mac, open System Preferences > Keyboard > Shortcuts. You may then flick thru current shortcuts for taking a screenshot, displaying the desktop, utilizing accessibility choices, and extra. To make a change, double-click on the present keys for a selected motion, then press the brand new configuration in your keyboard.
Your new motion should use the Management, Possibility, or Command key. So as an example, if you wish to change the way you open the screenshot menu, choose Screenshots and double-click the keyboard shortcut subsequent to Screenshot and recording choices. You may then change the Shift + Command + 5 shortcut to one thing easier like Possibility + Z.
For one-button shortcuts, flip to the operate key. Examine the field subsequent to Use F1, F2, and so forth. keys as customary operate keys on the Keyboard settings web page, then open the Shortcuts tab and set a operate key to carry out a sure motion with a single button. As an alternative of utilizing Perform + F1, now you can simply press F1 to take screenshots.
In case your new shortcut is being utilized by a unique motion, macOS will warn you about a problem. You may as well disable actions by unchecking the field subsequent to it. Sadly, you will not have the ability to flip one key into one other or create customized shortcuts like you’ll be able to with some Home windows packages. For extra highly effective choices, you’ll be able to flip to the free packages Karabiner-Components(Opens in a brand new window) and FunctionFlip(Opens in a brand new window).
Like What You are Studying?
Join Suggestions & Methods publication for knowledgeable recommendation to get essentially the most out of your know-how.
This article might include promoting, offers, or affiliate hyperlinks. Subscribing to a publication signifies your consent to our Phrases of Use and Privateness Coverage. You could unsubscribe from the newsletters at any time.

Technology
Google is shutting down Android Instant Apps over ‘low’ usage

Google has confirmed that it plans to shut down Android’s Instant Apps later this year, attributing the decision to “low” usage of the functionality.
Instant Apps were introduced in 2017, and allow developers to create mini versions of Android apps that load, well, instantly. Users can try apps and demo games from the click of a link, without having to fully install them. That makes the experience easier for users to navigate and provides developers with more ways to find new audiences.
Android Authority first reported that Google is moving on from the feature, which came to light after developer Leon Omelan spotted a warning about the change in Android Studio:
“Instant Apps support will be removed by Google Play in December 2025. Publishing and all Google Play Instant APIs will no longer work. Tooling support will be removed in Android Studio Otter Feature Drop.”
Google spokesperson Nia Carter confirmed the decision to The Verge, explaining that Instant Apps simply haven’t been popular enough to continue supporting.
“Usage and engagement of Instant Apps have been low, and developers are leveraging other tools for app discovery such as AI-powered app highlights and simultaneous app installs,” Carter says. “This change allows us to invest more in the tools that are working well for developers, and help direct users to full app downloads to foster deeper engagement.”
Technology
11 easy ways to protect your online privacy in 2025

NEWYou can now listen to Fox News articles!
Privacy is getting harder to protect in a world where everything is connected.
Whether you’re chatting with an AI, checking your email or using your smartphone, your personal information is constantly being collected, tracked and sometimes even sold.
But protecting your privacy in 2025 doesn’t have to be overwhelming. With a few practical steps, you can take back control of your data and make your online life safer. This guide walks you through 11 easy ways to get started.
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide free when you join.
Scrabble pieces form the word “SCAM.” (Kurt “CyberGuy” Knutsson)
1. Don’t overshare: Even with AI tools like ChatGPT
AI chatbots like ChatGPT are useful, but they’re not private journals. The platform owners may have privacy policies and use the latest security measures, but that doesn’t mean you should let your guard down. When using these tools, refrain from sharing any personal information, such as your name, address, birthdate, passwords, financial details or sensitive conversations. Remember that AI systems store and process your inputs, and despite security promises, data breaches can occur.
SCAMMERS CAN EXPLOIT YOUR DATA FROM JUST 1 CHATGPT SEARCH
Tip: Treat all online forms of AI interaction like public forums. Keep your examples generic and use caution with anything that could identify you.
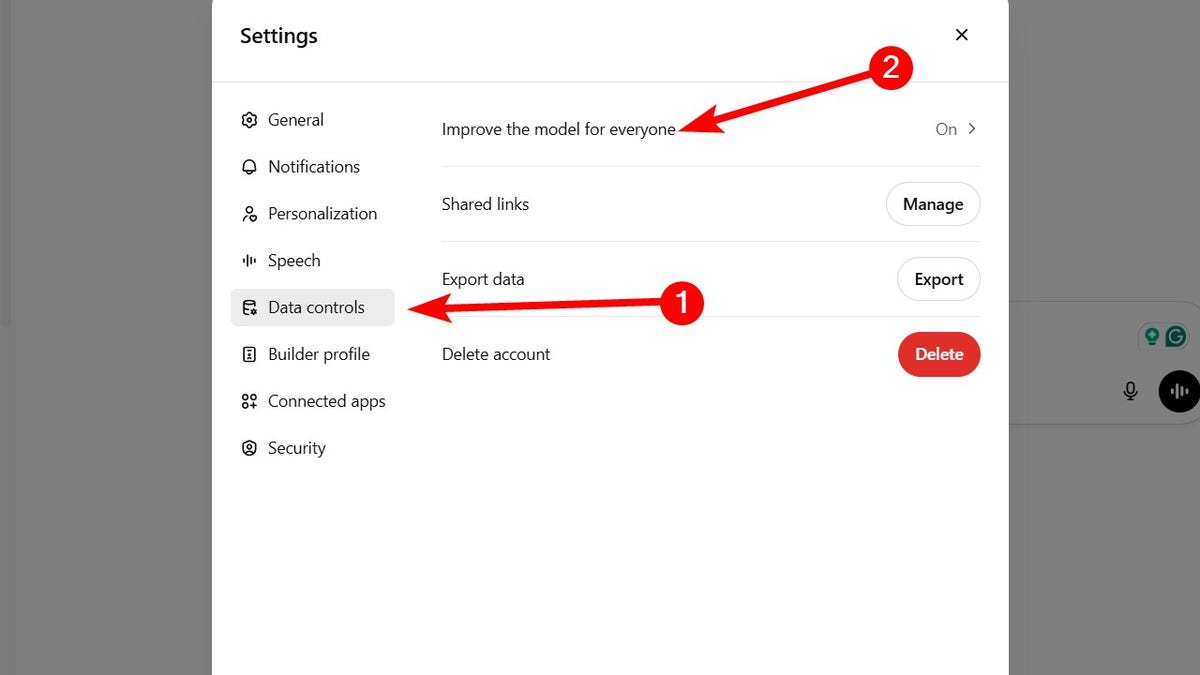
If you’re going to input your personal information while using these AI tools, ensure there is an option to prevent them from sharing it. On ChatGPT, for instance, do the following:
- Go to Settings.
- Click Data controls.
- Tap Improve the model for everyone.
Steps to prevent ChatGPT from sharing your personal information (Kurt “CyberGuy” Knutsson)
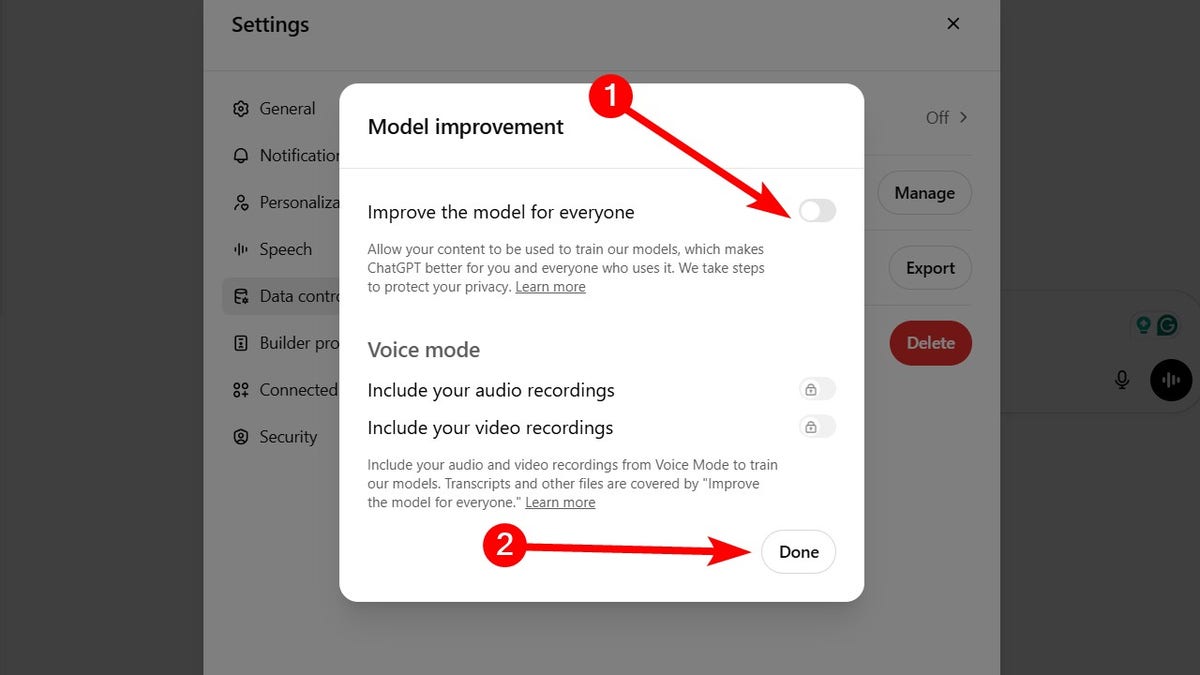
- Toggle off Improve the model for everyone.
- Click Done.
Steps to prevent ChatGPT from sharing your personal information (Kurt “CyberGuy” Knutsson)
Why it matters: AI tools may seem personal, but they’re not secure vaults. Guarding what you share helps prevent misuse, identity theft or data leaks from breaches.
CLEAN UP YOUR PHONE: SPEED, STORAGE AND PRIVACY BOOST IN MINUTES
2. Use alias email addresses
Your email is often the key to your online identity and a common target for spam. By creating disposable email aliases that forward messages to your main inbox, you can keep your real address hidden from websites and services. These unique aliases act as shields, so if one starts getting spammed or is involved in a data breach, you can simply deactivate it without affecting your main email account.
My top recommendation to avoid being inundated with spam emails is to use an alias email address. An alias email address is an additional email address that can be used to receive emails in the same mailbox as the primary email address. It acts as a forwarding address, directing emails to the primary email address.
In addition to creating throwaway email accounts for online sign-ups and other circumstances where you would not want to disclose your primary email address, alias email addresses are helpful for handling and organizing incoming communications.
Sometimes, it’s best to create various email aliases so that you don’t have to worry about getting tons of spam mail or having your information taken in a data breach. An alias email address is a great way for you to stop receiving constant spam mail by simply deleting the email alias address. See my review of the best secure and private email services here.
Why it matters: You stay anonymous, avoid data leaks and never have to change your main email address again.
BEST ANTIVIRUS FOR MAC, PC, IPHONES AND ANDROIDS – CYBERGUY PICKS
3. Take advantage of Facebook’s privacy checkup
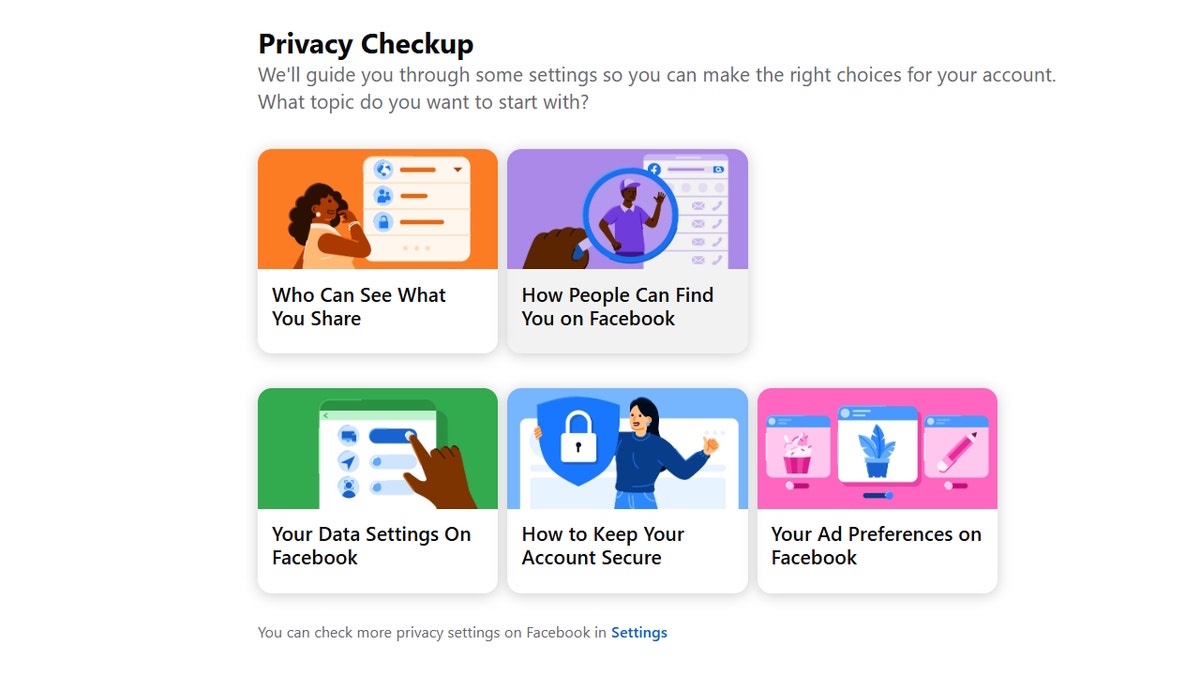
Meta frequently updates its privacy settings, so it’s best to check regularly to see how you can improve your privacy. Use Facebook’s Privacy Checkup tool to review and adjust crucial settings, including post visibility, app permissions, search visibility and friend-request settings. This comprehensive tool helps ensure your profile remains as private as you want it to be. You can find the tool by following these steps:
- Log in to your Facebook app on your phone.
- Then click the menu icon in the bottom right.
- Tap Settings.
- Click Privacy Checkup.
Once you open the Privacy Checkup, you’ll be guided through several key areas to customize your privacy preferences and better control your information.
- Who can see what you share: Adjust who can view your posts, photos and profile details to limit access to only people you trust.
- How people can find you on Facebook: Manage who can send you friend requests, look you up using your email or phone number, and decide whether your profile appears in search engines.
- Your data settings on Facebook: Review which apps and websites have access to your Facebook data and remove any you no longer use or trust.
- How to keep your account secure: Set up two-factor authentication, update your password and monitor login alerts to protect your account from unauthorized access.
- Your ad preferences on Facebook: Control how Facebook uses your activity to show you personalized ads and opt out of categories that feel too intrusive.
Quick tip: Set a reminder to run a privacy checkup every few months, especially after major Facebook updates. This way, you’ll always be in control of your information.
Why it matters: Social media platforms thrive on your personal data. Adjusting your settings regularly puts you back in control of what others and Facebook can see and use.
Facebook’s privacy checkup (Kurt “CyberGuy” Knutsson)
HOW TO PROTECT YOUR ONLINE PRIVACY AND SECURITY ON YOUR NEXT CRUISE VACATION
4. Scrub yourself off the internet automatically
Your name, phone number and home address may already be listed on people-search sites like Spokeo, Whitepages and BeenVerified. These data brokers collect and sell your personal information without you even knowing it. Fortunately, personal data removal services are available to protect your privacy. They automatically send legal removal requests to hundreds of data brokers. They also go above and beyond by continuously monitoring them in case these third parties happen to get your information again.
While no service can guarantee the complete removal of your data from the internet, a data removal service is really a smart choice. They aren’t cheap and neither is your privacy. These services do all the work for you by actively monitoring and systematically erasing your personal information from hundreds of websites. It’s what gives me peace of mind and has proven to be the most effective way to erase your personal data from the internet. By limiting the information available, you reduce the risk of scammers cross-referencing data from breaches with information they might find on the dark web, making it harder for them to target you. Check out my top picks for data removal services here.
Get a free scan to find out if your personal information is already out on the web.
Why it matters: The less personal information available about you online, the harder it is for scammers and identity thieves to target you and the more peace of mind you’ll have.
10 SIMPLE STEPS TO IMPROVE YOUR SMARTPHONE’S SECURITY AND PRIVACY
5. Use a privacy-focused messaging app
If you’re still using standard texting apps or platforms like Facebook Messenger, it’s time to upgrade to a more secure option. Apps like Signal and Session offer end-to-end encryption, no ads and no metadata tracking, meaning they can’t see who you’re talking to or what you’re saying. Both apps support disappearing messages, giving you more control over how long your conversations stick around.
Why it matters: Your messages stay private and can’t be accessed by hackers, advertisers or the app developers themselves.
6. Stop Google from tracking your every move
Google collects a massive amount of data from your searches, YouTube views, Gmail activity and location history, all of which fuels targeted advertising. You can stop much of this tracking by turning off Ad Personalization and deleting your activity history. Here’s what to do:
- Go to Google’s My Ad Center.
- Find the Ad Personalization section.
- Toggle the switch to turn off ad personalization. This stops Google from using your activity to tailor ads.
Manage activity history
- In My Ad Center or via your Google Account, go to Data & Privacy.
- Under History Settings, review and pause or delete: Web & App Activity, YouTube History and Location History (if applicable).
Delete existing activity data
- Select Manage all Web & App Activity, Manage all YouTube History, etc.
- Delete past activity by choosing a time range (e.g., “All time”) and confirming deletion for each category.
Opt out of third-party ad personalization
- Scroll to Ad settings and look for third-party ad personalization options.
- Opt out of partner sites’ ad personalization if available.
- If you have multiple Google accounts, repeat these steps for each account.
Why it matters: Cutting down on ad tracking reduces how much of your online behavior is used to build a profile on you, often without your knowledge.
7. Turn off location tracking on your smartphone
Apps don’t need to know your every move. Disabling or limiting location tracking is one of the simplest ways to protect your physical privacy. Here’s what to do:
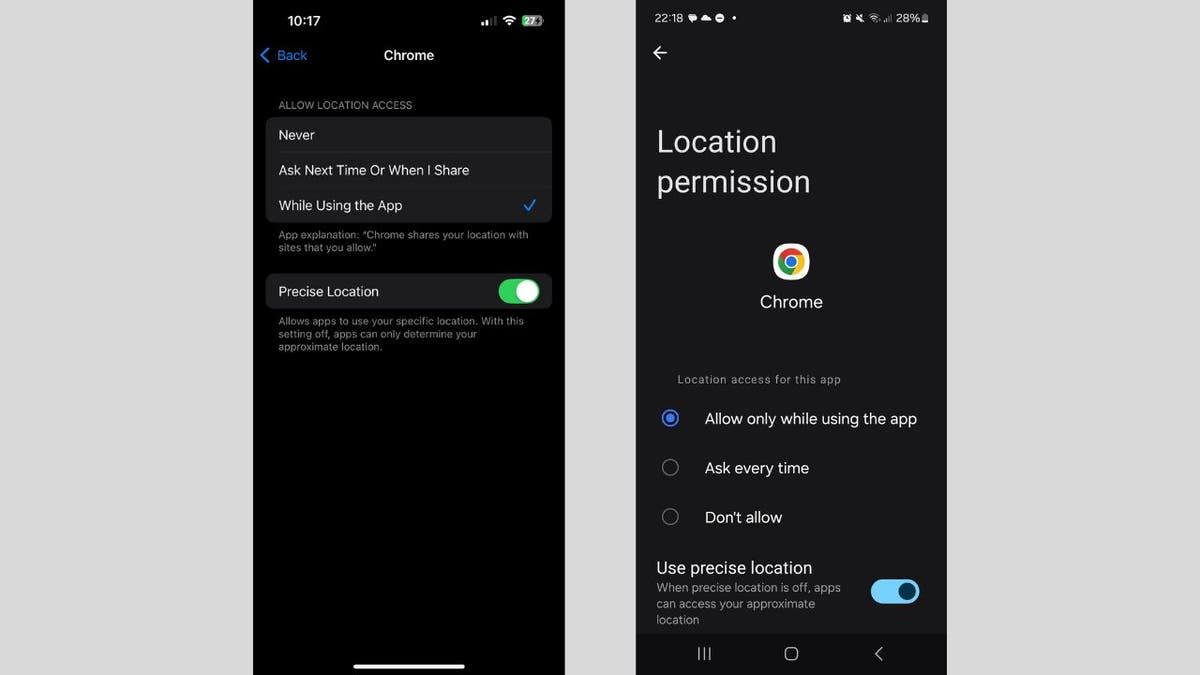
iPhone:
- Go to Settings.
- Tap Privacy & Security.
- Click Location Services.
- Scroll down and tap the app you want to manage.
- Choose your preferred setting: Never to block location access completely; Ask Next Time Or When I Share to allow location only with your permission; While Using the App to allow location only when the app is open.
For apps like Maps, toggle Precise Location off to prevent pinpoint tracking.
To disable location tracking entirely, toggle Location Services off at the top of the Location Services page (this will stop all apps from using your location).
Android:
Settings may vary depending on your Android phone’s manufacturer.
- Go to Settings.
- Tap Location.
- Tap App permissions or App location permissions.
- You will see a list of apps grouped by their location access: Allowed all the time; Allowed only while in use; Ask every time; Not allowed.
- Tap any app to change its location permission. Choose from: Allow all the time; Allow only while using the app; Ask every time; Don’t allow.
For apps that have location access, you can also turn Precise location on or off if you want to limit accuracy. Repeat for each app you want to manage.
Tip: If you want to stop all apps from accessing your location, you can turn off Location at the top of the Location settings page.
Why it matters: Prevents apps, advertisers and even your OS from building a detailed map of your daily routines.
Steps to turn off location tracking on your smartphone (Kurt “CyberGuy” Knutsson)
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
8. Change the default admin password on your router
Most routers ship with default admin usernames and passwords like “admin” or “1234,” and these are publicly available online. Hackers know this and often scan networks looking for unprotected routers. Here’s what to do:
- Log in to your router’s settings via its IP address (often 192.168.1.1 or 192.168.0.1).
- Change the admin username and password to something strong and unique.
- Consider using a password manager to generate and store complex passwords. Get more details about my best expert-reviewed password managers of 2025 here.
Why it matters: Prevents intruders from hijacking your home network and spying on your devices.
9. Enable WPA3 encryption on your Wi-Fi router
WPA3 is the newest wireless encryption protocol and offers much stronger protection than WPA2. If your router supports WPA3, enabling it is a no-brainer. How to check:
- Log into your router settings and look under Wireless Security.
- If WPA3 is available, enable it.
- If not, consider upgrading to a newer, security-focused router. Check out our top routers for best security 2025.
Why it matters: Stronger encryption means hackers can’t easily intercept or crack your Wi-Fi traffic.
10. Set up a guest network for visitors and smart devices
Your friends don’t need access to your entire home network and neither do your smart lights and doorbells. Creating a guest network adds a safety barrier between your personal devices and less trustworthy ones. Steps to take:
- Log into your router settings.
- Create a separate guest network with its own password.
- Connect smart devices, TVs and guests to this network only.
- Keep your main network just for personal computers and phones.
Why it matters: Even if a smart device gets compromised, the attacker won’t have access to your main network or sensitive devices.
11. Use a secure, private browser for sensitive browsing
Not all browsers treat your privacy equally. Switching to a browser designed for privacy like Brave, Firefox or DuckDuckGo’s browser can drastically cut down on the amount of data collected about you while you browse. Also, use incognito/private mode for sensitive searches.
Why it matters: Reduces digital fingerprints and helps stop advertisers and data brokers from building a profile on you based on your browsing behavior.
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES
Kurt’s key takeaways
Staying private online isn’t about being paranoid; it’s about making smart, intentional choices. With the right tools and a few small changes, you can take back control of your data in 2025. Digital privacy is always changing, so it’s a good idea to check your settings and habits every so often. The upside is that for every new privacy challenge, there’s usually a way to push back and keep your information safe.
If you’d like a printable checklist or want this content turned into a shareable infographic, just let me know.
What privacy tools and methods do you use to protect your data online? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most-asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.
Technology
Anker is recalling over 1.1 million power banks due to fire and burn risks

The recall covers about 1,158,000 units that were sold online through Amazon, Newegg, and eBay between June 2016 and December 2022. The affected batteries can be identified by the Anker logo engraved on the side with the model number A1263 printed on the bottom edge. However, Anker is only recalling units sold in the US with qualifying serial numbers. To check if yours is included, you’ll need to visit Anker’s website.
Anker is offering affected consumers their choice of either a $30 gift card (the recalled battery cost around $27) that can be used on Anker.com, or a free 10,000mAh Anker power bank as a replacement (model A1388) featuring upgrades including a charge level display and a USB-C charging cable lanyard.
To receive the gift card or the replacement, Anker requires a “photo of the power bank with the submission date and the word ‘recall’ or ‘recalled’ written clearly in permanent marker,” to be submitted, and a “photo showing the model number and serial number (SN) printed on the bottom of the device.” The company is also requesting a purchase receipt, but it’s not mandatory to participate in the recall.
After confirming that your power bank is one of the recalled units, Anker says it should be taken to a facility that can safely dispose of lithium-ion batteries due to the risk of fire. Those facilities can be found through the Environmental Protection Agency’s website or other organizations in the US that specialize in processing e-waste. Do not throw them in the trash, recycling bins, or used battery boxes provided at various retail locations.
The recall is also a reminder that power banks and backup batteries can potentially develop severe issues over time, as these particular units are almost a decade old. If you’ve been regularly using devices featuring lithium-ion batteries for a while, you’ll want to be mindful of issues like overheating or visible swelling and dispose of them properly if you think there’s a potential problem. And while the technology is currently more expensive than lithium-ion batteries, you can also consider upgrading to solid-state batteries which are more powerful, safer, and longer lasting than what we commonly use now to power our devices.
-

 West7 days ago
West7 days agoBattle over Space Command HQ location heats up as lawmakers press new Air Force secretary
-

 Technology1 week ago
Technology1 week agoiFixit says the Switch 2 is even harder to repair than the original
-

 World1 week ago
World1 week agoEU-Ukraine trade reset: What comes after tariff-free access expires?
-

 Technology1 week ago
Technology1 week agoThe single best wireless controller I’ve ever used
-

 Politics1 week ago
Politics1 week agoHawley clashes with UPenn law professor over judicial injunctions
-

 Business1 week ago
Business1 week agoHow Hard It Is to Make Trade Deals
-

 Movie Reviews1 week ago
Movie Reviews1 week agoPredator: Killer of Killers (2025) Movie Review | FlickDirect
-

 News1 week ago
News1 week agoTrump’s Higher Steel Tariffs Sour Mood at Deal-Making Table













