Crypto
NJ man hired hitman for $20K in Bitcoin to kill a 14-year-old

A New Jersey man who admitted to paying a hitman $20,000 in cryptocurrency to have a 14-year-old youngster murdered could withstand 10 years behind bars.
John Michael Musbach, 31, pleaded responsible to an indictment charging him with one rely of “knowingly and deliberately utilizing and inflicting one other to make use of a facility of interstate and international commerce, that’s the web, with the intent {that a} homicide be dedicated,” the Division of Justice stated Thursday.
The Haddonfield man is accused of exchanging sexually specific pictures and movies with the then-13-year-old sufferer throughout the summer season of 2015. The sufferer lived in New York on the time.
After the sufferer’s dad and mom realized of the “inappropriate contact,” they notified legislation enforcement, who recognized Musbach within the case.
In March 2016, Musbach was arrested on youngster pornography fees, the DOJ stated.
Prosecutors allege that Musbach determined to have the sufferer killed in order that the sufferer couldn’t testify towards him within the pending legal case.
Musbach repeatedly contacted the administrator of a murder-for-hire web site on the darkish internet, which purported to supply contact killings or different acts of violence in alternate for cryptocurrency, from Might 7, 2016, to Might 20, 2016.
“Musbach requested if a 14-year-old was too younger to focus on, and upon listening to that the age was not an issue, paid roughly 40 bitcoin (roughly $20,000 on the time) for the hit,” prosecutors stated.
Following his cost, Musbach repeatedly messaged the web site’s administrator to inquire about when the homicide would happen. The administrator then requested a further $5,000, which prompted Musbach to try to cancel the hit and get his $20,000 returned.
The web site’s administrator then revealed to Musbach that the operation was a sham, and threatened to show Musbach over to legislation enforcement.
Musbach faces a most potential penalty of 10 years in jail and a high quality “of the larger of $250,000, twice the gross earnings to Musbach or twice the gross losses to the sufferer of his offense.”
He’s scheduled to be sentenced on June 13.

Crypto
Bitget Launchpool to List DeLorean (DMC), Offering 66 Million Tokens in Rewards – Branded Spotlight Bitcoin News

Crypto
CoinMarketCap briefly hacked to drain crypto wallets via fake Web3 popup

CoinMarketCap, the popular cryptocurrency price tracking site, suffered a website supply chain attack that exposed site visitors to a wallet drainer campaign to steal visitors’ crypto.
On Friday evening, January 20, CoinMarketCap visitors began seeing Web3 popups asking them to connect their wallets to the site. However, when visitors connected their wallets, a malicious script drained cryptocurrency from them.
The company later confirmed threat actors utilized a vulnerability in the site’s homepage “doodle” image to inject malicious JavaScript into the site.
“On June 20, 2025, our security team identified a vulnerability related to a doodle image displayed on our homepage. This doodle image contained a link that triggered malicious code through an API call, resulting in an unexpected popup for some users when visited our homepage,” reads a statement posted on X.
“Upon discovery, We acted immediately to remove the problematic content, identified the root cause, and comprehensive measures have been implemented to isolate and mitigate the issue.”
“We can confirm all systems are now fully operational, and CoinMarketCap is safe and secure for all users.”
Cybersecurity firm c/side explained that the attack worked by the threat actors somehow modifying the API used by the site to retrieve a doodle image to display on the homepage. This tampered JSON payload now included a malicious script tag that injected a wallet drainer script into CoinMarketCap from an external site named “static.cdnkit[.]io”.
When someone visited the page, the script would execute and display a fake wallet connect popup showing CoinMarketCap branding and mimicking a legitimate Web3 transaction request. However, this script was actually a wallet drainer designed to steal connected wallets’ assets.
“This was a supply chain attack, meaning the breach didn’ target CMC’s own servers but a third-party tool or resource used by CMC,” explains c/side.
“Such attacks are hard to detect because they exploit trusted elements of a platform.”
More details about the attack came later from a threat actor known as Rey, who said that the attackers behind the CoinMarketCap supply chain attack shared a screenshot of the drainer panel on a Telegram channel.
This panel indicated that $43,266 was stolen from 110 victims as part of this supply chain attack, with the threat actors speaking in French on the Telegram channel.
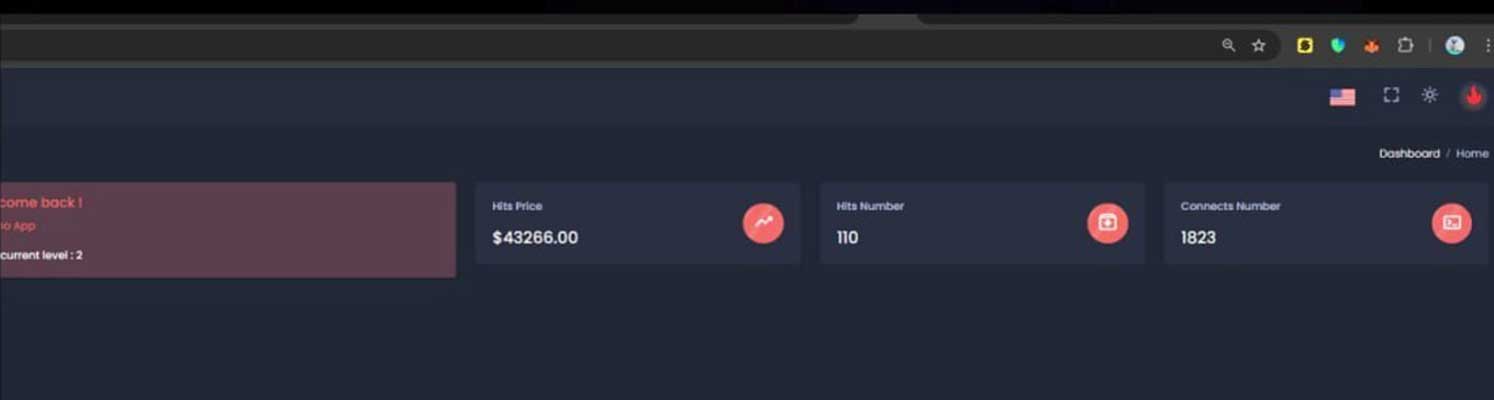
Source: Rey
As the popularity of cryptocurrency has boomed, so has the threat from wallet drainers, which are commonly used in attacks.
Unlike traditional phishing, these types of attacks are more often promoted through social media posts, advertisements, spoofed sites, and malicious browser extensions that include malicious wallet-draining scripts.
Reports indicate that wallet drainers stole almost $500 million in 2024 through attacks targeting more than 300,000 wallet addresses.
The problem has become so pervasive that Mozilla recently introduced a new system to detect wallet drainers in browser add-ons uploaded to the Firefox Add-on repository.

Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work — no complex scripts required.
Crypto
Meta Earth Network 2.0: Pioneering Web3 Innovation With Rewards and Global Events – Press release Bitcoin News

-

 Arizona5 days ago
Arizona5 days agoSuspect in Arizona Rangers' death killed by Missouri troopers
-

 News1 week ago
News1 week agoAt Least 4 Dead and 4 Missing in West Virginia Flash Flooding
-

 News1 week ago
News1 week agoOakland County sheriff urging vigilance after shootings of 2 Minnesota lawmakers
-

 Culture1 week ago
Culture1 week agoBook Review: “The Möbius Book, by Catherine Lacey
-

 Technology1 week ago
Technology1 week agoTanks, guns and face-painting
-

 News1 week ago
News1 week agoVideo: Trump's Military Parade Met With Nationwide Protests
-
 World1 week ago
World1 week agoAt least 100 people killed in gunmen attack in Nigeria: Rights group
-

 Mississippi1 week ago
Mississippi1 week agoMiss Mississippi 2025: Who won in the third night of preliminary rounds? Find out here



















