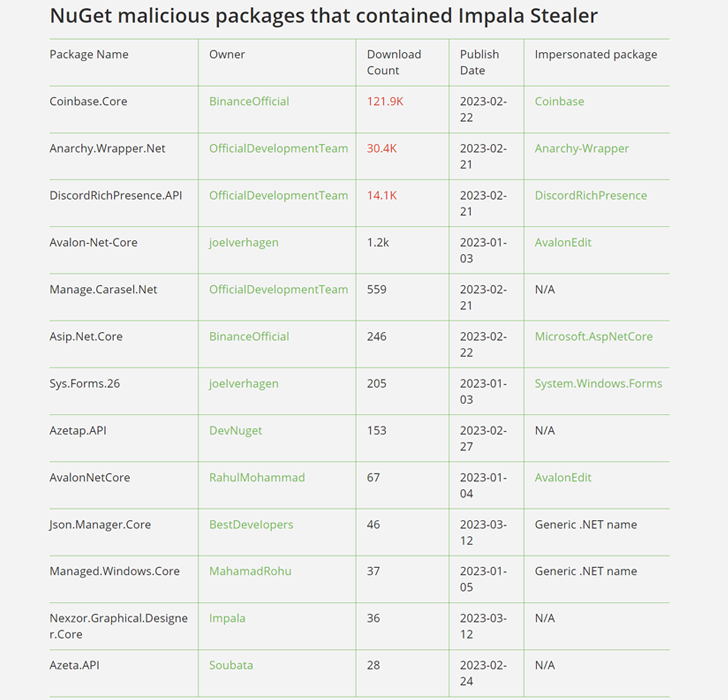
Cybersecurity researchers have detailed the interior workings of the cryptocurrency stealer malware that was distributed through 13 malicious NuGet packages as a part of a provide chain assault focusing on .NET builders.
The subtle typosquatting marketing campaign, which was detailed by JFrog late final month, impersonated reliable packages to execute PowerShell code designed to retrieve a follow-on binary from a hard-coded server.
The 2-stage assault culminates within the deployment of a .NET-based persistent backdoor, known as Impala Stealer, which is able to gaining unauthorized entry to customers’ cryptocurrency accounts.
“The payload used a really uncommon obfuscation approach, known as ‘.NET AoT compilation,’ which is much more stealthy than utilizing ‘off the shelf’ obfuscators whereas nonetheless making the binary arduous to reverse engineer,” JFrog advised The Hacker Information in a press release.
.NET AoT compilation is an optimization approach that enables apps to be ahead-of-time compiled to native code. Native AOT apps even have sooner startup time and smaller reminiscence footprints, and might run on a machine with out .NET runtime put in.
The second-stage payload comes with an auto-update mechanism that permits it to retrieve new variations of the executable from a distant location. It additional achieves persistence by injecting JavaScript code into Discord or Microsoft Visible Studio Code apps, thereby activating the launch of the stealer binary.
The binary then proceeds to seek for the set up of the Exodus Pockets desktop utility and inserts JavaScript code into varied HTML recordsdata so as to harvest and exfiltrate delicate knowledge to a hard-coded Discord webhook.
The JavaScript snippet, for its half, is fetched from a web-based paste web site from the place it is already been deleted. That stated, it is suspected that the code could have been used to steal person credentials and entry different info of curiosity.
“The unhealthy actors used typosquatting methods to deploy a customized malicious payload […] which targets the Exodus crypto pockets and leaks the sufferer’s credentials to cryptocurrency exchanges, by utilizing code injection,” Shachar Menashe, senior director at JFrog Safety Analysis, stated.
Study to Safe the Id Perimeter – Confirmed Methods
Enhance your corporation safety with our upcoming expert-led cybersecurity webinar: Discover Id Perimeter methods!
Do not Miss Out – Save Your Seat!
“Our investigation proves no open supply software program repository is totally trust-worthy, so security measures needs to be taken at each step of the software program growth lifecycle to make sure the software program provide chain stays safe.”
The findings come as Phylum unearthed a malicious npm package deal named mathjs-min that was uploaded to the repository on March 26, 2023, and located to harbor a credential stealer that grabs Discord passwords from the official app in addition to net browsers like Google Chrome, Courageous, and Opera.
“This package deal is definitely a modified model of the broadly used Javascript math library mathjs, and was injected with malicious code after being forked,” the software program provide chain safety agency stated. “The modified model was then printed to NPM with the intention of passing it off as a minified model of the real mathjs library.”
