Crypto
451 PyPI packages install Chrome extensions to steal crypto
Over 450 malicious PyPI python packages had been discovered putting in malicious browser extensions to hijack cryptocurrency transactions made via browser-based crypto wallets and web sites.
This discovery is a continuation of a marketing campaign initially launched in November 2022, which initially began with solely twenty-seven malicious PyPi packages, and now vastly increasing over the previous few months.
These packages are being promoted via a typosquatting marketing campaign that impersonates common packages however with slight variations, resembling an altered or swapped character. The aim is to deceive software program builders into downloading these malicious packages as a substitute of the reliable ones.
As Phylum explains in a report printed on Friday, along with scaling up the marketing campaign, the menace actors now make the most of a novel obfuscation technique that entails utilizing Chinese language ideographs in perform and variable names.
New typosquatting wave
Among the common packages impersonated within the present typosquatting embody bitcoinlib, ccxt, cryptocompare, cryptofeed, freqtrade, selenium, solana, vyper, websockets, yfinance, pandas, matplotlib, aiohttp, beautifulsoup, tensorflow, selenium, scrapy, colorama, scikit-learn, pytorch, pygame, and pyinstaller.
The menace actors use between 13 and 38 typosquatting variations for every of the above, making an attempt to cowl a broad vary of potential mistypes that might end in downloading the malicious bundle.
To evade detection, the menace actors have employed a brand new obfuscation technique that wasn’t current within the November 2022 wave, now utilizing a random 16-bit mixture of Chinese language ideographs for perform and variable identifiers.
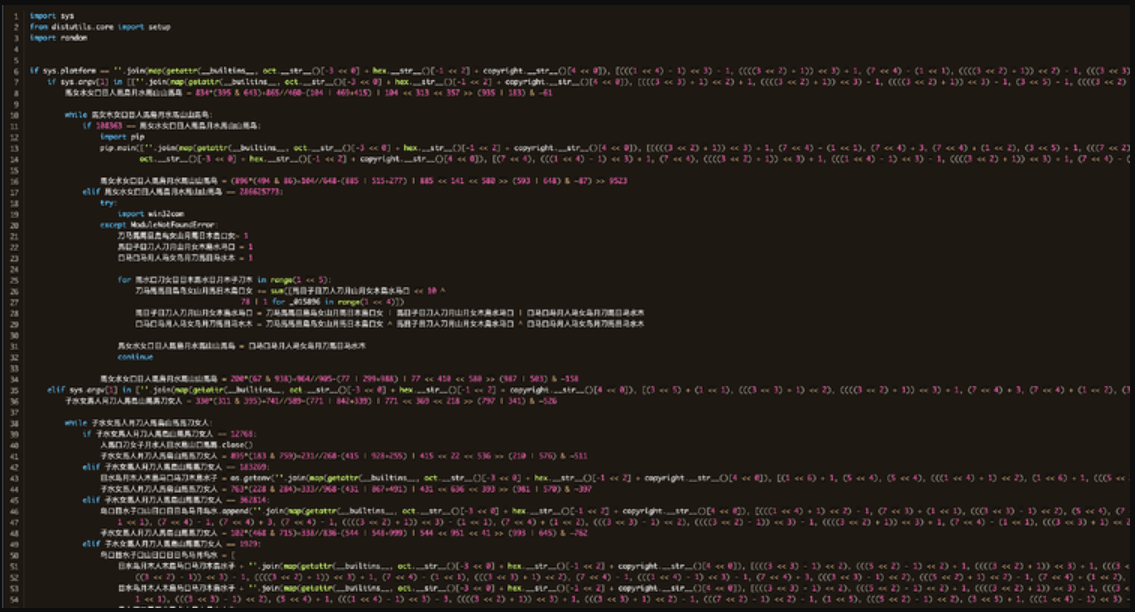
Source: Phylum
Phylum’s analysts found that the code makes use of built-in Python features and a collection of arithmetic operations for string technology. So, whereas the obfuscation creates a visually robust end result, it is not very exhausting to interrupt.
“Whereas this obfuscation is attention-grabbing and builds up extraordinarily advanced and extremely obfuscated trying code, from a dynamic standpoint, that is trivial,” reads Phylum’s report.
“Python is an interpreted language, and the code should run. We merely have to judge these cases, and it reveals precisely what the code is doing.”
Malicious browser extensions
To hijack cryptocurrency transactions, the malicious PyPi packages will create a malicious Chromuim browser extension within the ‘%AppDatapercentExtension’ folder, much like the November 2022 assaults.
It then searches for Home windows shortcuts associated to Google Chrome, Microsoft Edge, Courageous, and Opera and hijacks them to load the malicious browser extension utilizing the ‘–load-extension’ command line argument.
For instance, a Google Chrome shortcut can be hijacked to “C:Program FilesGoogleChromeApplicationchrome.exe –load-extension=%AppData%Extension”.
When an online browser is launched, the extension will load, and malicious JavaScript will monitor for cryptocurrency addresses copied to the Home windows clipboard.
When a crypto deal with is detected, the browser extension will substitute it with a set of hardcoded addresses below the menace actor’s management. This manner, any despatched crypto transaction quantity will go to the menace actor’s pockets as a substitute of the supposed recipient.
A listing of standard expressions used to detect cryptocurrency addresses within the Home windows clipboard and substitute them with the menace actor’s addresses could be seen beneath.
Source: Phylum
On this new marketing campaign, the menace actor prolonged the variety of supported wallets and has now added cryptocurrency addresses for Bitcoinm Ethereum, TRON, Binance Chain, Litecoin, Ripple, Sprint, Bitcoin Money, and Cosmos.
For a whole record of the malicious packages that must be prevented, test the underside part of Phylum’s report.