Technology
OnePlus says select 2023 phones will get four major Android updates
/cdn.vox-cdn.com/uploads/chorus_asset/file/23918372/op_10t_johnson_4.jpg)
OnePlus is committing to an extended help interval for some upcoming telephones, with an announcement that “choose gadgets launched in 2023 and past” will obtain 4 main Android updates and 5 years of safety updates. However an organization spokesperson declined to present an on-the-record reply about which of its telephones will profit from this prolonged help interval, which means it’s unclear whether or not it’ll simply apply to OnePlus’ flagship telephones or additionally the midrange Nord lineup.
The size of help OnePlus has given to its telephones has traditionally different between gadgets however, generally, has began to lag behind what’s supplied by different Android producers. Each the OnePlus 10T and OnePlus 10 Professional are on account of get three main OS model upgrades and 4 years of safety updates, whereas the midrange OnePlus Nord 2T will get simply two main Android updates and three years of safety patches. Worst of all, the corporate has dedicated to only one OS improve for the inexpensive Nord N300 and two years of safety updates.
No matter what its opponents are providing, providing 4 years of OS upgrades and 5 years of safety patches is an efficient factor for OnePlus patrons, particularly given individuals are utilizing their telephones for longer and longer earlier than changing them. Maintaining telephones usable for longer ought to imply fewer gadgets should be recycled or head to landfills prematurely, which is a win for the surroundings regardless of the way you slice it.

Technology
Google fires 28 employees after sit-in protest over Israel cloud contract
/cdn.vox-cdn.com/uploads/chorus_asset/file/24016887/STK093_Google_02.jpg)
Serious consequences for disruptive behavior
Googlers,
You may have seen reports of protests at some of our offices yesterday. Unfortunately, a number of employees brought the event into our buildings in New York and Sunnyvale. They took over office spaces, defaced our property, and physically impeded the work of other Googlers. Their behavior was unacceptable, extremely disruptive, and made coworkers feel threatened. We placed employees involved under investigation and cut their access to our systems. Those who refused to leave were arrested by law enforcement and removed from our offices.
Following investigation, today we terminated the employment of twenty-eight employees found to be involved. We will continue to investigate and take action as needed.
Behavior like this has no place in our workplace and we will not tolerate it. It clearly violates multiple policies that all employees must adhere to — including our Code of Conduct and Policy on Harassment, Discrimination, Retaliation, Standards of Conduct, and Workplace Concerns.
We are a place of business and every Googler is expected to read our policies and apply them to how they conduct themselves and communicate in our workplace. The overwhelming majority of our employees do the right thing. If you’re one of the few who are tempted to think we’re going to overlook conduct that violates our policies, think again. The company takes this extremely seriously, and we will continue to apply our longstanding policies to take action against disruptive behavior — up to and including termination.
You should expect to hear more from leaders about standards of behavior and discourse in the workplace.
Technology
Nationwide alert: SMS phishing attacks target toll road customers

The FBI has issued a critical warning about a pervasive scam sweeping across the country.
Americans are being targeted by a sophisticated series of SMS phishing — or “smishing” — attacks that bait them with fictitious unpaid road toll charges.
Toll road scam text. (FBI)
A surge of fraudulent activity
The smishing scheme has been active since last month, duping thousands of people, as reported by victims to federal authorities.
The FBI’s Internet Crime Complaint Center has documented a significant influx of over 2,000 complaints detailing deceptive texts that impersonate road toll services from various states.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER

Man texting on his phone. (Kurt “CyberGuy” Knutsson)
MORE: IS THE FTC CALLING YOU? PROBABLY NOT. HERE’S HOW TO AVOID A NEW PHONE SCAM TARGETING YOU
Mechanism of the road toll scam
Investigations reveal that these messages are uniform in their deception, falsely asserting that the recipient is delinquent on road toll payments. These communications aim to manipulate individuals into clicking on links that are ingeniously designed to mimic legitimate state toll service websites, complete with fluctuating phone numbers to elude detection.
HIGH SCHOOL STUDENTS, PARENTS WARNED ABOUT DEEPFAKE NUDE PHOTO THREAT

Woman texting on her phone. (Kurt “CyberGuy” Knutsson)
MORE: THE DARK WORLD OF FACEBOOK ADS WHERE SCAMMERS ARE TRYING TO STEAL YOUR MONEY
Regional responses to the threat
The Pennsylvania Turnpike has been at the forefront of the afflicted services, proactively advising its customers to avoid interacting with these fraudulent messages. Similarly, the Pennsylvania State Police have expressed their concern, highlighting that the scam texts redirect to counterfeit websites designed to steal personal data.

Pennsylvania toll road scam text. (Kurt “CyberGuy” Knutsson)
Expanding the watch
Regional services are not the only ones affected. E-ZPass customers who use the toll service across various parts of the U.S. have been under threat since the onset of these attacks. While this detail is not directly mentioned in the FBI’s public service announcement, secondary sources tracking the issue have confirmed it.
MORE: ‘UNSUBSCRIBE’ EMAIL SCAM IS TARGETING AMERICANS
Guidance if you receive a toll scam text message
The FBI has recommended several preventive measures in light of the ongoing phishing attacks.
1. Report the phishing attempt at ic3.gov with the scammer’s contact details and the website URL from the message.
2. Verify your toll account through the official service website.
3. Reach out to the official customer service for the toll service.
4. Erase the fraudulent text message from your device.
5. Use good antivirus protection on all devices to reduce risks. The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
If you click one of these toll scam links
For individuals who have engaged in these phishing attempts, it is crucial to take immediate action to secure personal and financial information. The FBI stresses the importance of monitoring for unfamiliar charges and disputing them promptly to mitigate any potential financial harm.
Kurt’s key takeaways
As the threat landscape evolves, staying informed about these scams is paramount. By following the FBI’s advisories and maintaining a high level of skepticism toward unsolicited texts claiming to be from toll services, you can safeguard against these invasive phishing tactics. It’s really important that we all work together to spot and call out scams. By doing this, we’re joining forces to protect people from cybercriminals who try to trick them.
What role should mobile carriers and tech companies play in combating smishing scams, and how can they improve their current measures? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most-asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
Coding bootcamp Lambda School — now BloomTech — is finally getting punished
/cdn.vox-cdn.com/uploads/chorus_asset/file/19715597/acastro_200212_1777_Lambda_0001.jpg)
Why? Among other deceptive practices, the “Bloom Institute of Technology” didn’t call them loans. It advertised a way for students to get high-paying tech jobs “risk free” with “no loans” by paying 17 percent of their future income for five years — rather than the $20,000 sticker price of tuition.
But those Income Sharing Agreements (ISAs) were definitely loans, the CFPB has decided, since Bloom was earning an average finance charge of $4,000 on each one, students could default and get sent to collections if they failed to make payments, and Bloom was turning around and selling those student debts to investors for $7,000 to $10,000 a pop.
Bloom handed out more than 11,000 of these loans between 2017 and 2023, according to the CFPB consent order you can read at the bottom of this story. But it doesn’t offer them as of 2024, so the ban on future loans may be too little, too late.
That said, the agency’s also ordering Bloom to cancel all loans for students who haven’t made a payment in the last 12 months, let current students immediately quit the program with no debt, and return a small amount of money to graduates who paid Bloom a premium and yet didn’t manage to land a job making $70,000 or more. That last group of students will still have loans, but retroactively capped at the sticker price of tuition.
BloomTech has already agreed to the order; company CEO Austin Allred signed his consent last Friday. He’ll personally be paying $100,000 out of the $164K penalty, and is banned from student lending activities for 10 years.
None of this puts BloomTech out of business, by the way — it can keep operating with third-party loans instead.
In 2020, Lambda students told us their fears weren’t just about the worrying financial terms of the loan, but also how the company didn’t seem to be hiring professional instructors to provide students with the skills to actually land jobs despite promising “world class” industry experts. The CFPB’s report backs this up:
BloomTech’s curricula frequently changed and relied in part on teaching assistants paid $15 per hour with limited programming backgrounds. As a result, many students complained that they had to teach themselves the course content.
Allred tweeted that the school achieved a 100 percent job placement rate in one of BloomTech’s cohorts. In a private message, he later acknowledged that the sample size was just one student.
From 2019 forward, BloomTech touted job placement rates of at least 71 percent. But BloomTech’s non-public reporting to investors, which relied on more accurate methodologies, has consistently shown placement rates closer to 50 percent.
There’s more in the full consent order, which you can read below.
-

 News1 week ago
News1 week agoVideo: Election Officials Continue To Face Violent Threats
-

 Movie Reviews1 week ago
Movie Reviews1 week agoSasquatch Sunset (2024) – Movie Review
-

 World1 week ago
World1 week agoHope and anger in Gaza as talks to stop Israel’s war reconvene
-
Fitness1 week ago
This exercise has a huge effect on our health and longevity, but many of us ignore it
-

 Science1 week ago
Science1 week agoThe Eclipse Across North America
-
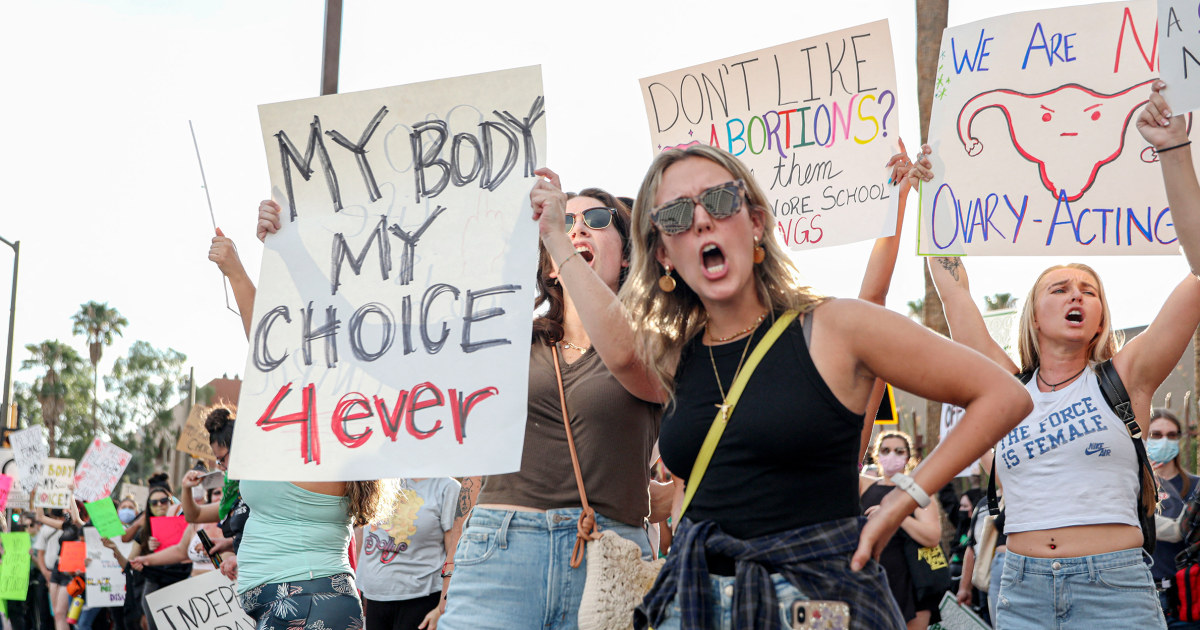
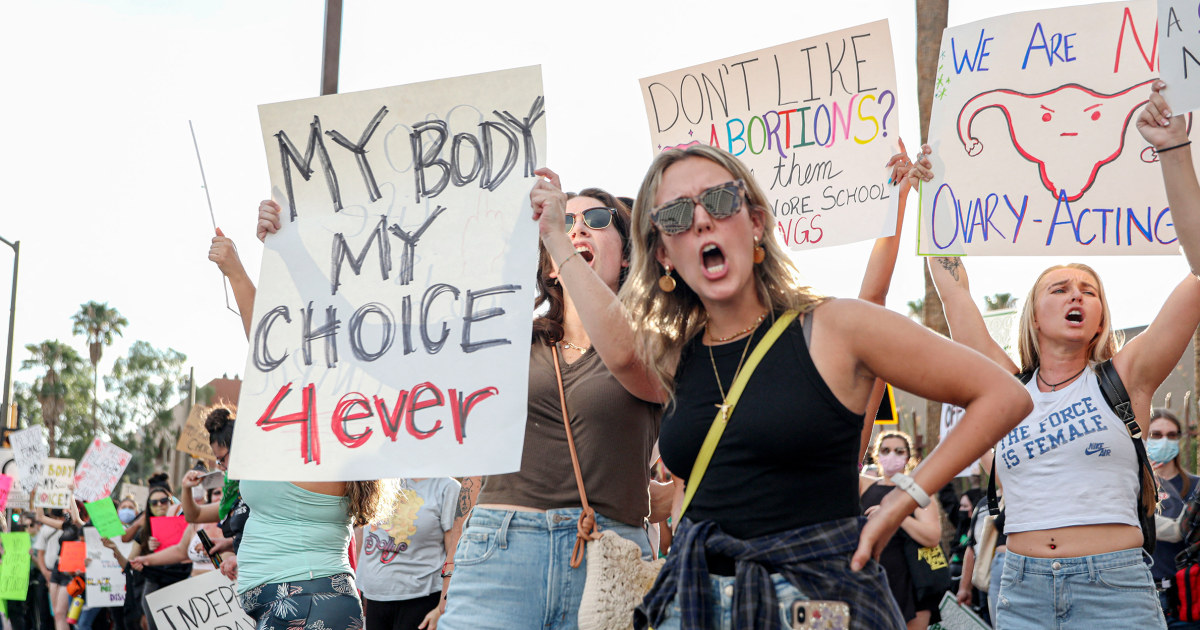 News1 week ago
News1 week agoArizona Supreme Court rules that a near-total abortion ban from 1864 is enforceable
-

 Uncategorized1 week ago
Uncategorized1 week agoANRABESS Women’s Casual Loose Sleeveless Jumpsuits Adjustbale Spaghetti Strap V Neck Harem Long Pants Overalls with Pockets
-

 Finance1 week ago
Finance1 week agoSponsored: Six Ways to Use Robinhood for Investing, Retirement Planning and More













