For those who prefer to grind gravel and bound over boulders while surrounded by luxurious napa leather — and can’t imagine emitting even a single molecule of carbon dioxide while doing so — the fully electric Mercedes G-Wagen is for you.
Technology
How to Remove Bloatware From Your New PC

A brand-new Windows computer should be pristine. After all, you haven’t gummed it up yet with software, right?
Leave that to the computer manufacturers who load your new PC with “free” software you don’t want. You might call it bloatware, crapware, shovelware, or crudware, since it’s basically useless to you. There’s a reason for doing it, of course—bloatware offsets the price of super-cheap PCs on retail shelves, even if only by pennies.
I’ve had few major problems with bloatware when buying PCs directly from a vendor. But in retail, it’s a whole other world of garbage. For example, a few years ago, my 75-year-old technophobic father got a new PC to replace his dying Windows Vista system, which he mainly used to print pictures. I couldn’t really recommend spending a lot of money to get it fixed. “Just go find an off-the-shelf PC for under $400; it’ll be fine,” I said.
Hardware-wise, that Acer Aspire X (Model AXC-605G-UW20) he purchased at Walmart was sufficient. The specs all qualified as an upgrade.

(Credit: PCMag, Walmart)
To sell this PC for $399, however, Acer sold out my parents and wasted hours of my family’s lives.
Using TeamViewer remote-control software, I could see that the system was a mess, though all my father had done was install the software for his beloved (but dying) Kodak printer. The desktop was awash with at least 15 icons for needless, worthless crap. Opening up the Uninstall a Program control panel revealed even more. We tried to uninstall the obvious things, but they persisted.
With many of the uninstall routines, the dialog boxes had giant buttons that would say “Uninstall and Get PC XXXXXX” or something similar. If we just wildly clicked where the button was, the uninstall might work—but something else was installed in its place. We had to look carefully for the fine print on the dialog boxes that read “Delete Only” or similar. Tricks and traps abounded.
Back then, I turned to Slim Computer from Slimware Utilities, which kept a database of bloatware and helped identify it on a new Windows PC. It has since been discontinued, but current options include Bulk Crap Uninstaller(Opens in a new window) and Should I Remove It?(Opens in a new window) (The excellently named PC Decrapifier was another favorite, but has also been discontinued.)

(Credit: Reason Cybersecurity)
These utilities point out some bloatware but might not automate removal—in which case you still have to go through the normal uninstall process, which might be filled with tricks and traps to keep your new PC full of bloatware. So you’re on your own to an extent. But there are ways around that.
‘Potentially Unwanted’ Crap
Dad’s then-new Acer PC also came with actual malware, in the guise of “potentially unwanted programs,” or PUPs.
The programs don’t call themselves that; it’s a term used by anti-malware companies such as MalwareBytes(Opens in a new window). It describes software you probably didn’t install on purpose, that you don’t want, and that you’ll likely find unusable. But it’s necessary to say “potentially,” because it’s possible you really wanted to install a toolbar for your browser called “Search Protect” from a company named Conduit(Opens in a new window) or a search engine for your browser called Binkiland.
In reality, that’s about as likely as wanting to be set on fire. Both of those “programs,” among others, were on Dad’s PC. They existed only to take over his browsing experience; each appears on a list of browser hijackers(Opens in a new window) from Wikipedia. Check the list, and delete any you see. The list can and will go on and on, as hijackers make new threats. It’s telling that searching for “Search Protect” or Binkiland brings up absolutely no link for people to download those programs—only to remove the hijackers’ files.
These programs did a number on my dad’s PC. I couldn’t get the installed browsers (IE and Firefox) to go to a website to download new tools to deal with those threats. I had to download the clean-up software to my workstation, then use TeamViewer to do a remote file transfer of the EXE installer to Dad’s desktop.
Also note that at this point, we uninstalled McAfee Security Suite, which came free with the Acer as well. You may not consider antivirus software to be bloatware, but it certainly can be. Acer didn’t put it on there to be altruistic; McAfee paid for placement. McAfee was likely to slow the PC more than other AV products we could install later, and it would eventually cost $79 after the trial was over. No, thanks.
Here’s a rundown of the tools used to clean the hijacking PUPs:
MalwareBytes
The free version of MalwareBytes comes with a trial of the Premium version, so it’s worth running on every fresh installation of Windows. Also, the scans take a lot less time on a new Windows install. After 14 days, you lose features such as real-time protection and anti-ransomware, but it’s worth running up front. Just remember after that two weeks, you should get some real-time anti-malware protection.
Steven Gould’s Cleanup
This donationware(Opens in a new window) does the trick for Windows XP on up.
CCleaner
This Windows cleanup tool can not only scrape away temp files and other detritus, but it can also uninstall apps built into Windows. I’m not talking bloatware but actual apps that Microsoft created to work with Windows. Consider them OS-sanctioned crap. Click on Tools, then uninstall, and you’ll get a list of possibilities to delete. (This suggestion might be controversial: CCleaner got hit with data-collecting malware in 2017, and in 2020, Windows’ own antivirus flagged it as a PUP but seems to have now cleaned up its act.)
I ran each of these tools multiple times, MalwareBytes in particular. It kept finding instances of the PUPs, so we turned to the internet (which we could finally surf again) to find instructions(Opens in a new window) for manually deleting individual PUP files. Which we did, with glee. After cleanups were run, the system wasn’t totally bug-free. But it was certainly cleaner than it had been hours before.
Don’t Do What We Did
Let me make it clear: I do NOT recommend going through the steps above.
If we bought that computer today, it would come with Windows 11. Start with a full reset of the OS using the Windows 11 Reset Tool. It’s the first thing anyone buying a new PC at retail should do after they take it out of the box. This should set the PC back to a pristine state, without bloatware (except the Microsoft-supplied stuff you may not want, such as the Edge browser).
Recommended by Our Editors

(Credit: PCMag/Microsoft)
Better yet, vote against bloatware with your wallet. Buy a PC from a maker that guarantees a clean Windows install or at least offers it as an option. Microsoft, naturally, has a clean version of Windows on its Surface devices.
Again, that’s clean as defined by Microsoft—you may not want OneNote or Microsoft’s Mail app. But it’s a lot easier to get rid of Windows add-on software than other bloatware. Right-click anything you see in the Windows Start menu and select Uninstall.
Custom-built-PC manufacturers that promise you a bloatware-free installation of Windows include Maingear(Opens in a new window), Falcon Northwest(Opens in a new window), and Velocity Micro(Opens in a new window). Another option is to go with a local reseller. Or, buy a Mac or a Chromebook and avoid Windows altogether. Or to save money, install Linux on your old PC. (That wasn’t really an option for my dad.)
If you’re wedded to using an older version of Windows, the only surefire way to get the same result is to reinstall the OS completely with a totally fresh, clean configuration. That’s not possible with most retail PCs that came with Windows 7, 8, or 8.1. Whether the operating system installer is an image on a partition of the hard drive or comes on a USB flash drive, it’s likely going to install Windows with all the bloatware, fresh as an outhouse, as well.
You can also find the option to download ISO files of Windows 7 and 8.1 and even 10 at the Microsoft Software Recovery site(Opens in a new window). You’ll need to verify a 25-character product key from a retail version of Windows to download and fully activate the operating system. Keys from computer makers—called OEMs, or original equipment manufacturers—won’t work.

(Credit: PCMag/Microsoft)
Why Is This Happening?
You might be wondering why big-name PC makers and software developers are loading all this bloatware with extra “internet wrapper” PUPs on new systems. The answer? Money, of course. As PC sales dwindle, so do software purchases, and companies scramble to make up for their losses.
For more details, read this article by How-To Geek(Opens in a new window). It examined programs from every major download site, including CNET’s Downloads.com, Tucows, FileHippo, Softpedia, Snapfiles, and more. Every site bundled crapware into the desired software. Some of those sites have multiple download “buttons,” some of which are actually ads, on every page, to obfuscate and confuse users into downloading the wrong thing. That story is from pre-COVID 2019, but it’s unlikely anything has changed. PC sales went up a bit during the pandemic but are back in freefall.
Always download software from the original developer’s site—if you can find it. Unfortunately, even Google search results tend to default to download sites such as those listed above.
Years ago, pundit Ed Bott called for a PC “Truth in Labeling Act”(Opens in a new window) to force PC manufacturers to tell users everything that is pre-installed. This is an excellent idea that will never happen. It would also be great if download sites, some of which claim they don’t allow any type of malware(Opens in a new window), would do the same.
Like What You’re Reading?
Sign up for SecurityWatch newsletter for our top privacy and security stories delivered right to your inbox.
This newsletter may contain advertising, deals, or affiliate links. Subscribing to a newsletter indicates your consent to our Terms of Use and Privacy Policy. You may unsubscribe from the newsletters at any time.

Technology
New stealthy submarine glider set for autonomous undersea missions

The ocean depths are a new frontier explored by humans and autonomous vehicles.
Leading the charge is Northrop Grumman’s innovative Manta Ray uncrewed underwater vehicle (UUV), a technological innovation set to revolutionize undersea missions.
The Manta Ray UUV (Northrop Grumman)
Engineering inspired by nature
The Manta Ray UUV was built through a Defense Advanced Research Projects Agency (DARPA) program. It is a testament to human ingenuity and nature’s inspiration. Drawing from the hydrodynamic form of its namesake, the manta ray, this extra-large glider vehicle promises to soar through the ocean on long-range missions without human assistance.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER

The Manta Ray UUV (Northrop Grumman)
MORE: THIS BULLETPROOF BODY ARMOR EXOSKELETON INNOVATION CAN TAKE ROUNDS FROM AK-47
A cloak of secrecy surrounding the Manta Ray
Details on the Manta Ray are sparse, shrouded in mystery, much like the ocean depths it’s designed to explore. What we do know is that it’s built for endurance and versatility, capable of carrying various payloads tailored to specific missions.
GREECE PROPOSES 2 MARINE PARKS AS PART OF $830M ENVIRONMENTAL PROTECTION PROGRAM

The Manta Ray UUV (Northrop Grumman)
MORE: DIVE INTO THE SEA WITH THIS STATE-OF-THE-ART UNDERWATER DRONE
Technological underwater leap forward
Northrop Grumman isn’t just creating a vehicle but pioneering advanced autonomous technologies. The Manta Ray’s energy-saving systems and modular design are set to revolutionize subsea warfare and beyond.

The Manta Ray UUV (Northrop Grumman)
MORE: IT MAY LOOK LIKE AN EAGLE, BUT IT’S ACTUALLY A STEALTHY BIRD-DRONE FOR COVERT MISSIONS
Advancing UUV technology
The Manta Ray program is set to introduce critical technologies for a new class of UUVs. These technologies include:
- Novel energy management techniques for UUV operations and undersea energy harvesting at operationally relevant depths
- Low-power, high-efficiency propulsion systems that redefine undersea travel
- New methods for underwater detection and classification of hazards and counter-detection threats
- Mission management approaches for extended durations, taking into account the dynamic maritime environment
- Leveraging existing maritime data sets and exploiting novel maritime parameters for high-efficiency navigation, command, control and communications (C3)
- Innovative solutions to mitigate biofouling, corrosion and material degradation for long-duration missions
The program’s multiphase effort includes at-sea demonstrations of these critical technologies, employing a disciplined systems engineering approach to define objectives and identify enabling technologies needed for future systems.
The Manta Ray UUV (Northrop Grumman)
Kurt’s key takeaways
The Manta Ray UUV is more than just a machine; it’s a leap into the future of undersea exploration and combat. Its ability to operate autonomously and adapt to various missions represents a significant advancement in unmanned maritime technology.
With the deployment of the Manta Ray UUV and similar autonomous technologies, what concerns do you have about the escalation of undersea warfare and its potential consequences for global security? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Technology
The Mercedes G-Wagen, the ultimate off-road status symbol, goes electric
/cdn.vox-cdn.com/uploads/chorus_asset/file/25413855/pre_media_24c0076_005.jpg)
The very expensive, boxy status symbol is now even status symbol-ier thanks to a 116 kWh battery and all-electric drive train, complete with four individually controlled motors with a maximum total output of 432 kW — or the equivalent of about 580 horsepower — and a max torque 1,164 Newton-meters.
“I recently joked that it’s like the Birkin bag of Mercedes,” Mercedes-Benz CEO Ola Källenius said on the Decoder podcast back in 2022. “Everybody wants one, and the waiting time is really long. It may even be the most desirable car in our portfolio.”
But with great power comes great expense. The Mercedes-Benz G 580 with EQ technology (an ungainly name for an exotic EV, but I’ll allow it) will start at €142,621.50 ($152,184.27), while the first edition trim goes for €192,524.15 ($205,432.89). That’s a premium over the gas models, which typically start at around $143,000. At launch, the Edition One trim will be exclusive to the US market and will arrive at dealerships in the second half of 2024.
The G 580, or EQG if you will, will be built on a ladder frame concept, which the automaker says is fundamental to its off-roading. Like its gas-powered equivalents, the ladder frame includes an independent front suspension with double wishbones, as well as a newly developed rigid rear axle for a lower center of gravity. The battery will propel the EQG to an estimated 473 km (293 miles) on the WLTP standard, which will likely be even lowered when based on the less optimistic EPA rating.
The electric G-Wagen will come with a whole caravan of nifty circus tricks, including a tank turn (which Mercedes has branded its G-Turn) for sharper, on-axis rotations. G-Turn will work on loose, unpaved roads and trails and only at low speeds. And a three-speed intelligent off-road crawl function will keep the electric SUV at the optimal speed while traveling over uneven surfaces. And Mercedes boasts that the EQG will remain stable on slopes up to 35 degrees and has a maximum fording depth of 850 millimeters (33 inches).
Of course, all that off-roading requires extra protection for the battery, which is stored in the floor of the vehicle for that low center of gravity. Every grain of gravel is a potential hazard when you’re driving around with a two-tiered lithium-ion battery with 216 cells installed in 12 cell modules between three cooling levels under your feet.
The underbody skid plate, which is unique to the electric G-Class, is made from “an intelligent material mix” that includes carbon, which “increases rigidity compared to alternatives made from steel or aluminum,” the company says. It also ensures long-lasting corrosion protection and saves weight. The plate is 26 millimeters thick, weighs 57.6 kilograms, and is attached to the ladder frame with more than 50 steel screws.
And in what is becoming an increasingly normal thing to do with new EVs, Mercedes has decided to give its electric G-Wagen a fake engine noise, branded here as G-Roar. Inspired by the gas lineup’s “emotional V8 sounds,” the G-Roar will use external speakers to emit a sound that simulates the “deep bass and sonorous tones” of its fuel-sipping sibling. The sounds can change when switching between drive modes: Comfort produces a more restrained fake engine noise, while Sport will hit you right in the feelings (Mercedes also describes it as “emotional”).
Even with an emphasis on off-roading over performance, the G 580 with EQ technology (nope, still ungainly, going back to EQG) is no slouch on the pavement. The electric SUV can accelerate from 0 to 100 km/h in 4.7 seconds and will be electronically limited to a maximum speed of 180 km/h (or 112 mph).
The exterior is nearly identical to the current model year of gas-fueled G-Wagens. You do get illuminated accents on the grille, which also can be replaced with an optional blacked-out front panel. The bonnet is slightly raised, and the rear wheel wells include air curtains for better aerodynamic performance. There’s also a new A-pillar cladding and a spoiler lip on the roof. But otherwise, it would be difficult to pick out the EV in an all-G-Class lineup.
A rear-mounted design box looks ideal for a spare tire, but open it up and — surprise! — it’s charging cables and other optional goodies, like snow chains. Of course, if you want to be a traditionalist, you can absolutely stow your spare tire in there. No judgment.
Inside, the electric G-Wagen is sticking to what works, keeping the passenger grab bar and surrounding everything with carbon fiber. There are plenty of physical buttons, and the air vents are delightfully tactile and circular. The pedals are covered in raised rivets because, you know, off-road. And the 12.3-inch digital display runs on Mercedes’ well-received MBUX infotainment system — but also supports Apple CarPlay and Android Auto.
Rear-seat passengers can enjoy a variety of media on their personal 11.6-inch touchscreens that are mounted on the back of the front seats. Content can be moved from the rear to the front display — but video watching and internet browsing are reserved for parked mode only.
The electric G-Wagen first emerged in concept form back in 2021 and then again in 2022, despite the company’s lack of clarity around production plans. (To compensate, Mercedes released a ridiculously high concept promotional video set in a 1970s-era space opera with aliens.)
But since then, there have been a lot of electric off-roaders, including the Ford F-150 Lightning, Chevy Silverado EV, Hummer EV, and Rivian R1T and R1S. Whether any of these vehicles actually spend a single second doing real off-road stuff — as opposed to picking up grass fertilizer at The Home Depot — is entirely up for debate. The electric G-Wagen will likely be no different, as the boxy SUV has always been seen more frequently in the driveways of the über rich than on the trails in Moab.
Still, the EQG is a sign that while it has pulled back some of its early predictions about electrification, Mercedes still understands that even its super luxury status symbols will need to go electric.
Technology
How to turn your iPhone into instant foreign language translator
In today’s interconnected world, the ability to communicate across language barriers is more important than ever. Apple has recognized this need and, in a recent iOS update, introduced a nifty feature that allows you to translate languages instantly without even opening the Translate app.
This feature utilizes the “Dynamic Island,” a pill-shaped area at the top of the iPhone screen that can change size and shape to accommodate various types of alerts, notifications and interactions, turning it into a kind of front-and-center information hub. The Dynamic Island feature is available on the iPhone 15 models, which includes the iPhone 15, iPhone 15 Plus, iPhone 15 Pro and iPhone 15 Pro Max.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER
Translate feature on iPhone (Kurt “CyberGuy” Knutsson)
MORE: TOP AFFORDABLE CELLPHONE PLANS
How to set up the Translate Action Button on iPhone 15
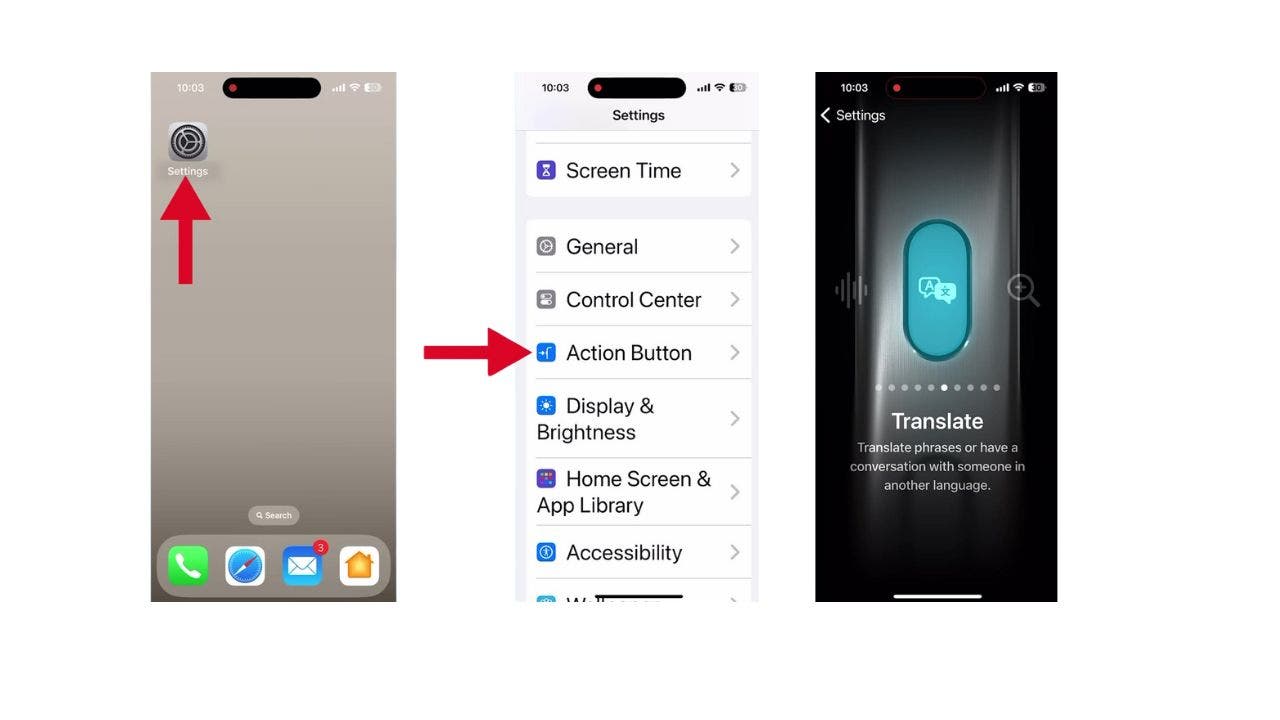
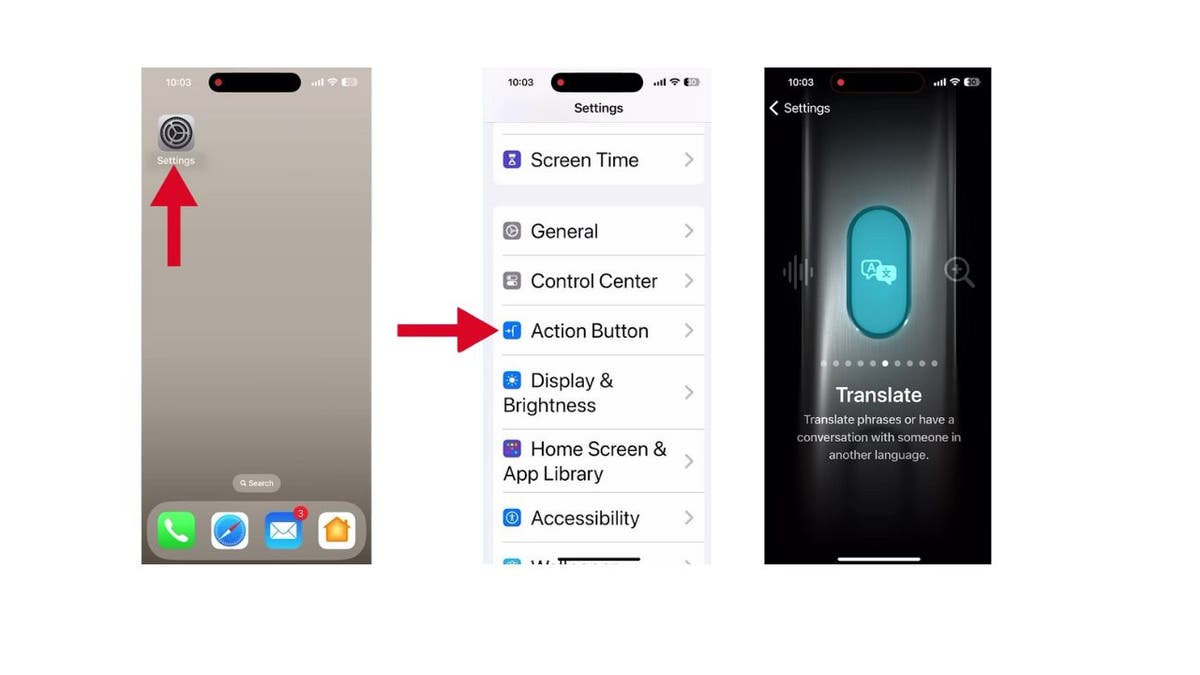
Getting started is simple. Here’s how you can set up the Translate option using the Action Button on your iPhone:
- Open Settings on your iPhone
- Scroll down and tap the Action Button
- Swipe through the carousel of actions until you get to Translate
Steps to set up the Translate Action Button (Kurt “CyberGuy” Knutsson)
MORE: HOW TO UPDATE YOUR PASSCODE ON YOUR IPHONE
How to use the Translate Action Button on iPhone 15
Once you’ve set it up, using it is just as easy:
- On the upper left side of your iPhone 15, press and hold the Action Button for a moment.
- Continue holding the Action Button until the Dynamic Island changes to display “English, Listening”.
- Start speaking the phrase you want to translate.
- After a moment, the translated text will appear on your screen and will be said aloud.
- If you need to hear the translation again, simply tap the play button.
Make sure to release the Action Button after the Dynamic Island shows “English, Listening” to ensure the feature works correctly.
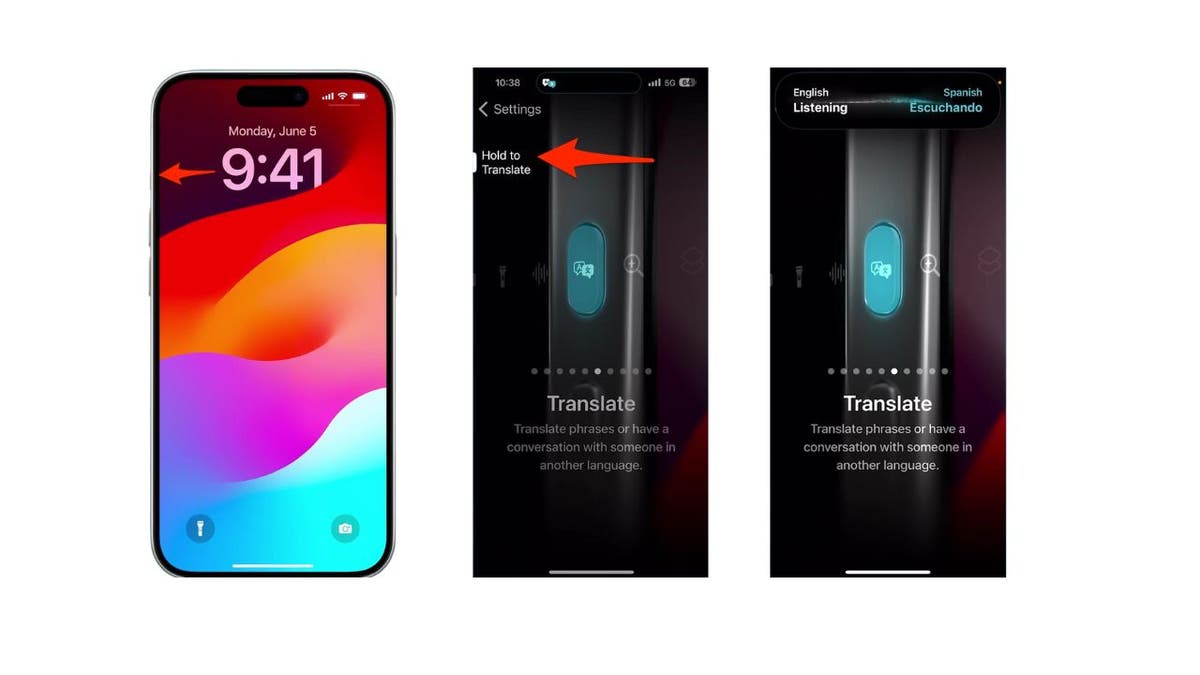
Steps to use the Translate Action Button (Kurt “CyberGuy” Knutsson)
MORE: HOW TO CREATE OR LEAVE GROUP TEXT ON YOUR IPHONE
How to adjust your translation settings
While you can’t change the Translate settings directly from the Action Button, you can still customize your experience within the Translate app itself:
- Open the Translate app.
- Tap on the top or bottom language listed, and a list of languages will appear for you to choose from.
- You can also toggle whether you want to translate from English to another language or vice versa.
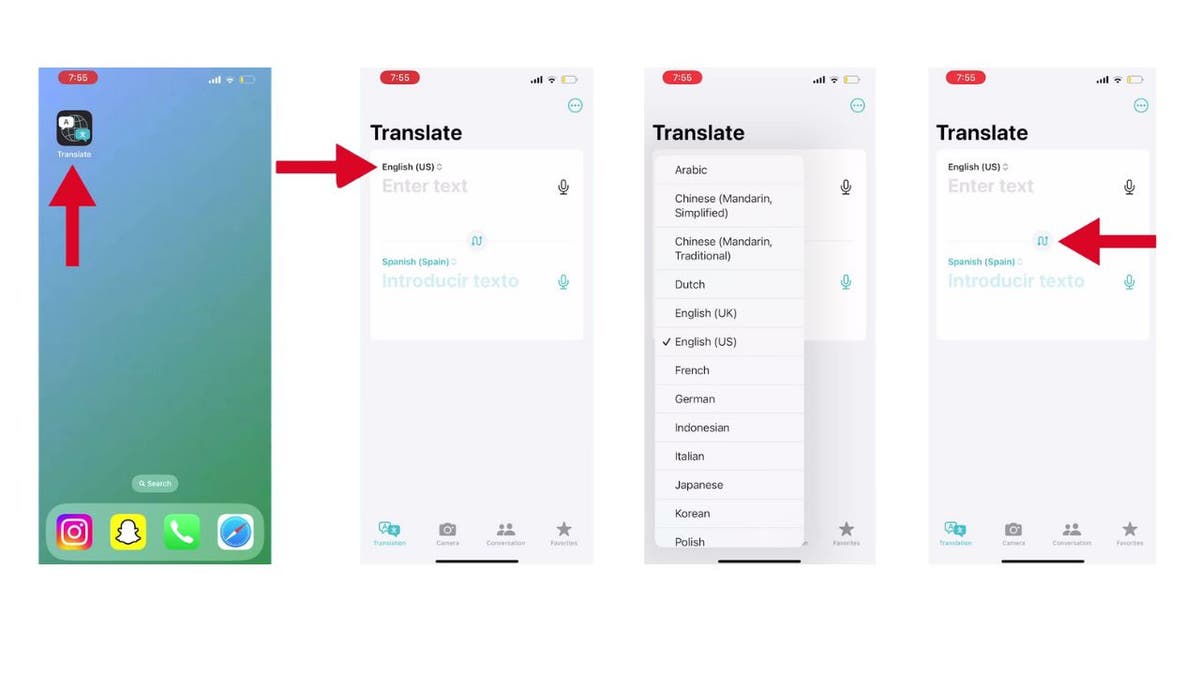
Steps to adjust your translation settings (Kurt “CyberGuy” Knutsson)
MORE: 8 WAYS TO LOCK UP YOUR PRIVATE STUFF ON YOUR IPHONE
Kurt’s key takeaways
Apple’s latest update is more than just a technical enhancement. It’s a step toward a world where language differences are no longer a barrier to communication. Whether you’re traveling abroad, learning a new language or connecting with friends and family across the globe, the ability to translate on the fly is a game-changer. It’s a testament to how technology can bring us closer together, making the vast world just a little bit smaller.
Have you ever found yourself in a situation where instant translation would have made a significant difference? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
-

 Politics1 week ago
Politics1 week agoNine questions about the Trump trial, answered
-

 World6 days ago
World6 days agoIf not Ursula, then who? Seven in the wings for Commission top job
-

 World1 week ago
World1 week agoHungary won't rule out using veto during EU Council presidency
-

 Movie Reviews1 week ago
Movie Reviews1 week agoFilm Review: Season of Terror (1969) by Koji Wakamatsu
-

 World1 week ago
World1 week agoCroatians vote in election pitting the PM against the country’s president
-

 World1 week ago
World1 week agoGroup of EU states should recognise Palestine together, Michel says
-

 Politics6 days ago
Politics6 days agoTrump trial: Jury selection to resume in New York City for 3rd day in former president's trial
-

 World1 week ago
World1 week agoThe Take: How Iran’s attack on Israel unfolded